Facebook’s massive 3 billion active users make it an attractive target for sophisticated phishing campaigns. As attackers grow more inventive, a hazardous technique is gaining traction: the “Browser-in-the-Browser” (BitB) attack.
This advanced social engineering method creates custom-built fake login pop-ups that are nearly indistinguishable from legitimate authentication windows, enabling credential theft on an unprecedented scale.
This method exploits a fundamental user behavior: the familiarity people have with third-party login pop-ups.
By simulating a legitimate authentication screen within a browser tab, attackers effectively mask credential-harvesting pages behind what appears to be an official Facebook login prompt.
The BitB technique operates with deceptive simplicity. Instead of redirecting users to an external phishing site, the attack creates an entirely fake window embedded within the legitimate browser interface.
Security researchers at Trellix observed a significant surge in Facebook phishing scams during the second half of 2025, with the BitB technique emerging as the most notable tactic.
This crucial distinction makes the attack far more convincing users see a pop-up appearing within their familiar browser environment, complete with legitimate-looking URLs and branding elements.
Attack Methodology
The typical BitB campaign begins with a carefully crafted phishing email, often disguised as a communication from a law firm.
These emails typically reference a fake legal notice regarding an infringing video and include a malicious hyperlink posed as a Facebook login link.
The shortened URL (often using services like lnk.ink) initially directs users to a fake Meta CAPTCHA verification page an additional evasion layer designed to appear authentic.
Once the user attempts to verify themselves, they encounter the BitB pop-up window displaying a Facebook login prompt.
The window displays the genuine Facebook URL, lending immediate credibility. However, examination of the underlying code reveals the URL is merely hardcoded into the malicious page, not a legitimate authentication portal. Users who enter their credentials unknowingly submit them directly to the attacker.
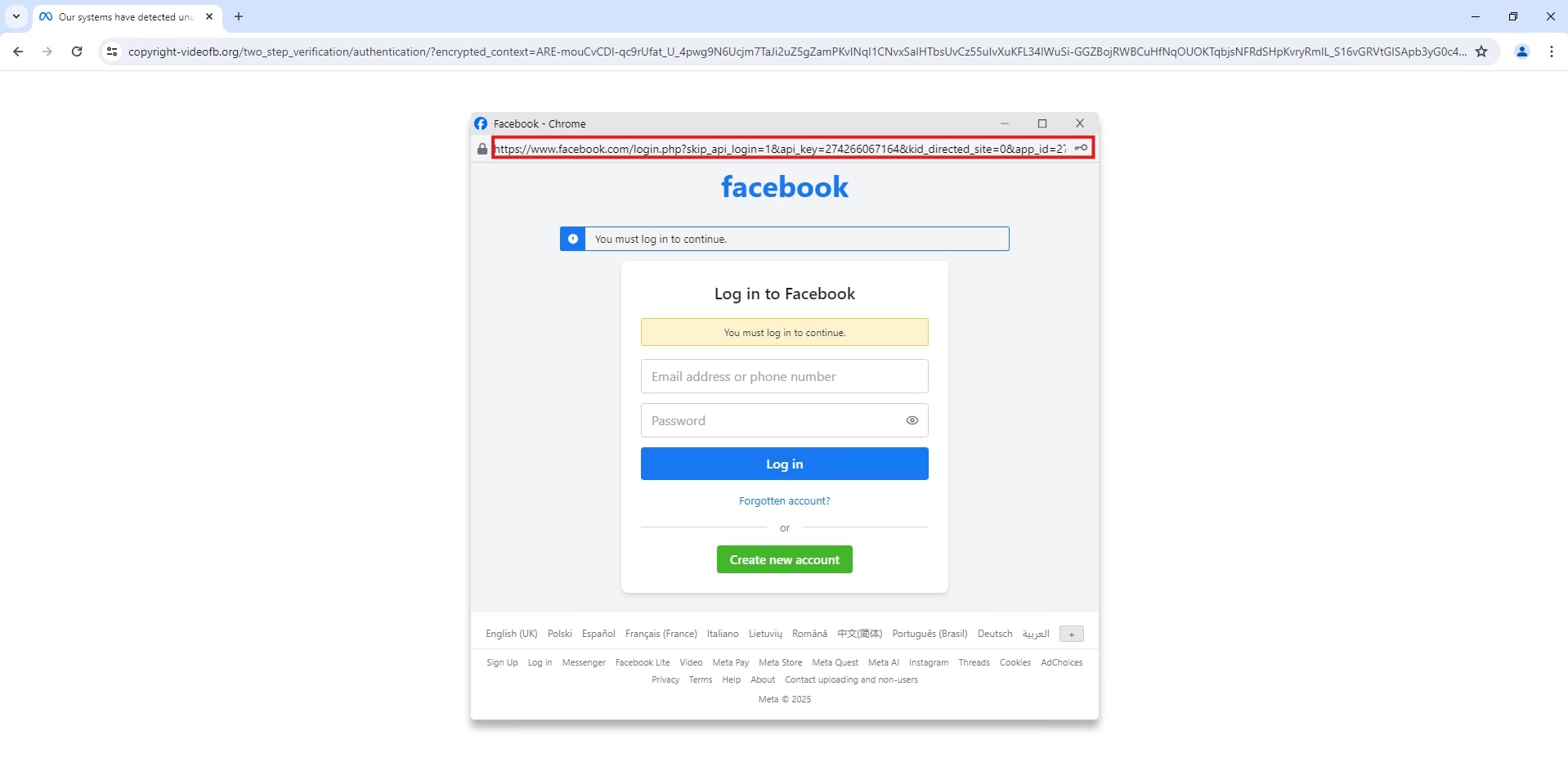
While BitB represents an escalation, attackers continue leveraging proven social engineering themes.
Account suspension or violation notices remain common, claiming users have violated copyright or community standards. Unauthorized login alerts warning of suspicious activity from unrecognized devices also persist.
Security update messages claiming Facebook has detected threats and requires identity re-verification continue to deceive users.
Abuse of Legitimate Infrastructure
A critical aspect of modern Facebook phishing is the weaponization of trusted services. Attackers host phishing pages on legitimate cloud platforms like Netlify and Vercel, lending unwarranted credibility to malicious sites.
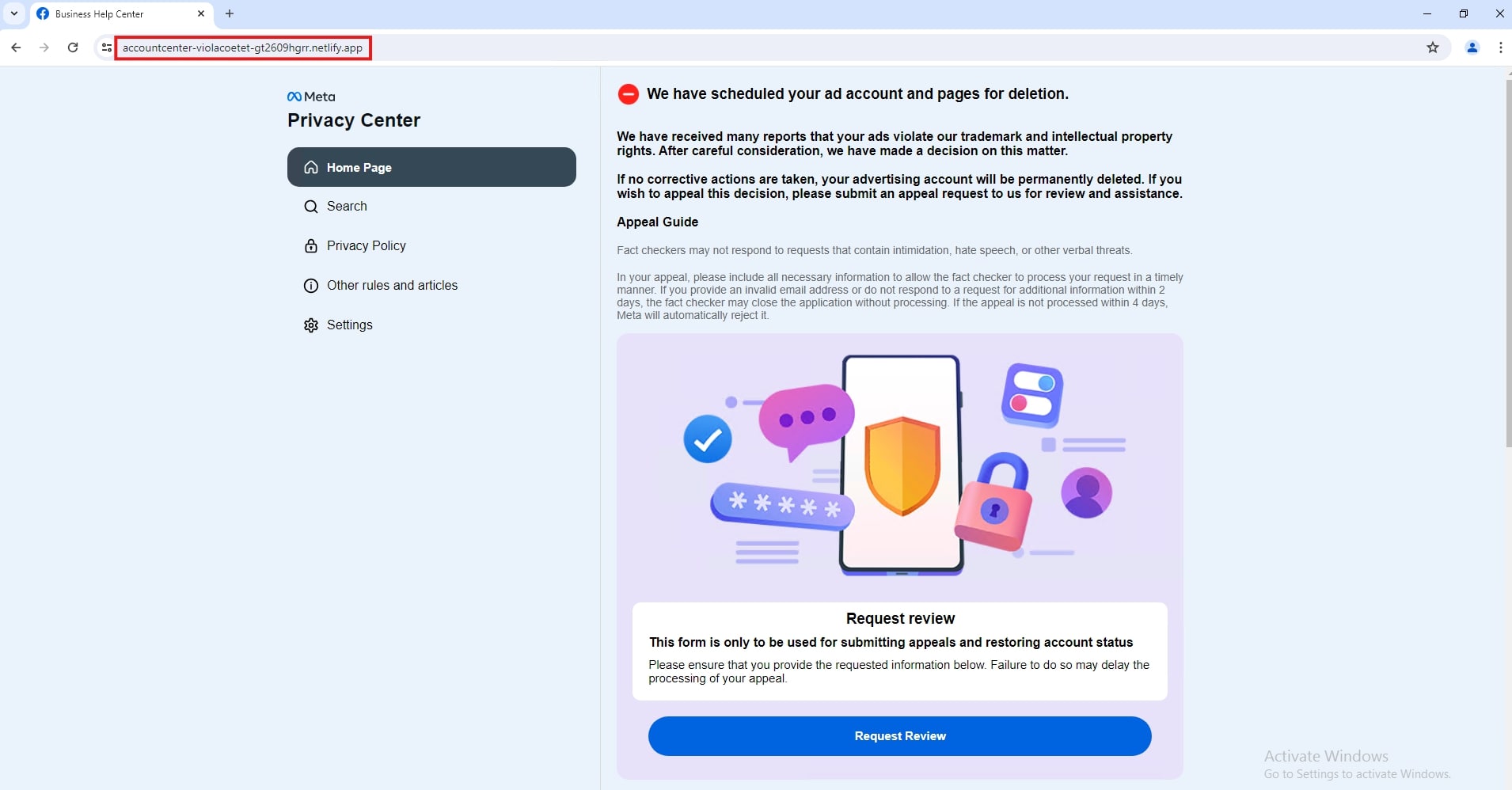
URL shorteners such as lnk.ink and rebrand.ly mask phishing destinations and evade traditional security filters.
This abuse of trusted infrastructure effectively bypasses many organizations security measures while making phishing pages appear legitimate.
The evolution of Facebook phishing reflects a troubling trend: attackers are combining technical sophistication with social engineering precision.
The BitB technique represents a watershed moment it proves credential theft no longer requires convincing users to visit external domains. Instead, attackers can harvest data directly within familiar browser environments.
Organizations and users must recognize that standard security awareness training is insufficient against these sophisticated attacks.
A comprehensive defense strategy combining user vigilance with platform-level security measures is now essential.
Multi-factor authentication, browser-based security indicators, and email filtering capable of detecting shortened URLs remain critical defenses against these evolving threats.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
