Security researchers have identified a sophisticated multi-stage malware campaign dubbed SHADOW#REACTOR that chains together obfuscated Visual Basic Script (VBS) execution, resilient PowerShell stagers, text-only payload delivery mechanisms, and .NET Reactor–protected in-memory loaders to deploy Remcos RAT while evading detection and analysis reliably.
Initial infection begins when users execute a malicious VBS script, typically delivered through socially engineered lures, which launches the first in a series of execution stages designed to reconstruct and perform the final Remcos payload entirely in memory.
The infection begins with the retrieval and execution of an obfuscated Visual Basic Script hosted at a compromised infrastructure.
The script executes via wscript.exe with error suppression and constructs a heavily obfuscated, base64-encoded PowerShell payload with deliberate corruption via placeholder characters.
Rather than embedding malicious functionality directly, the VBS acts as a minimal execution bridge, launching PowerShell with inline commands that normalize, decode, and execute the next stage entirely in memory.
The intrusion chain demonstrates how threat actors continue to weaponize commodity scripting languages combined with modern obfuscation and living-off-the-land binary (LOLBin) abuse to establish footholds in enterprise and small-to-medium business environments.
This multi-layer bootstrap ensures wscript.exe spawns powershell.exe with unusually large command strings while leaving minimal static indicators within the VBS itself.
Resilient PowerShell Staging Pipeline
The decoded PowerShell stager implements a controlled download-and-validate loop that repeatedly fetches remote content until reaching a predefined minimum size threshold.
This approach allows payload updates to be managed remotely while tolerating partial or failed downloads.
The stager selects architecture-specific resources qpwoe64.txt for 64-bit processes and qpwoe32.txt for 32-bit processes from attacker infrastructure and writes downloaded content to the %TEMP% directory using UTF-8 encoding.
Once qpwoe files meet expected size criteria, the stager dynamically constructs a secondary PowerShell script (jdywa.ps1) that reads the staging file, applies custom transformations, base64-decodes content into a byte array, and reflectively loads the resulting .NET assembly using built-in reflection APIs.
This layer invokes the central orchestrator method MyLibrary.Helper.Ruseysn() with parameters controlling subsequent execution behavior.
The transformed content resolves to a .NET assembly protected with .NET Reactor, a commercial code protection tool that converts intermediate language code to native machine code while applying control flow obfuscation, string encryption, and anti-tampering checks.
This protection makes static analysis significantly more difficult and complicates automated sandbox analysis.
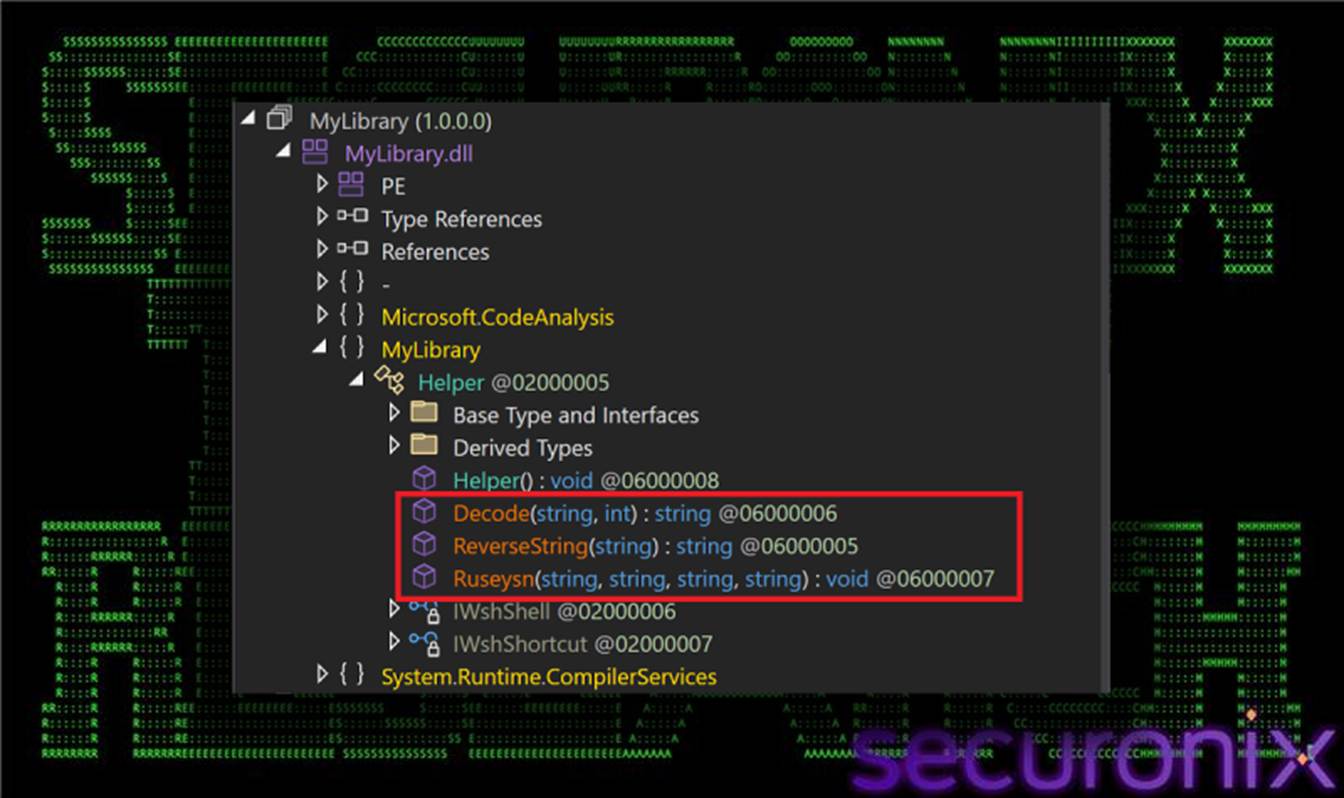
The Reactor-protected loader functions as a mid-stage execution controller responsible for coordinating all subsequent actions. All human-readable strings are concealed using custom string decryption implementing seeded XOR encryption with a rolling key.
The loader performs path de-obfuscation, optional anti-analysis checks, and retrieves the next in-memory .NET stage from attacker infrastructure via teste32.txt or teste64.txt resources.
Configuration data is separately retrieved through an obfuscated URL passed as the aurie parameter.
Final Payload and MSBuild Handoff
Analysis of decrypted configuration data confirms the final payload is Remcos RAT, a commercially available remote administration tool repurposed by threat actors for malicious purposes.
The loader constructs the full path to MSBuild.exe and passes both the decoded .NET assembly and configuration blob as parameters to MyApp.Program.wibqqw(), leveraging MSBuild as a trusted Microsoft-signed component to execute the final payload under the guise of normal system activity.
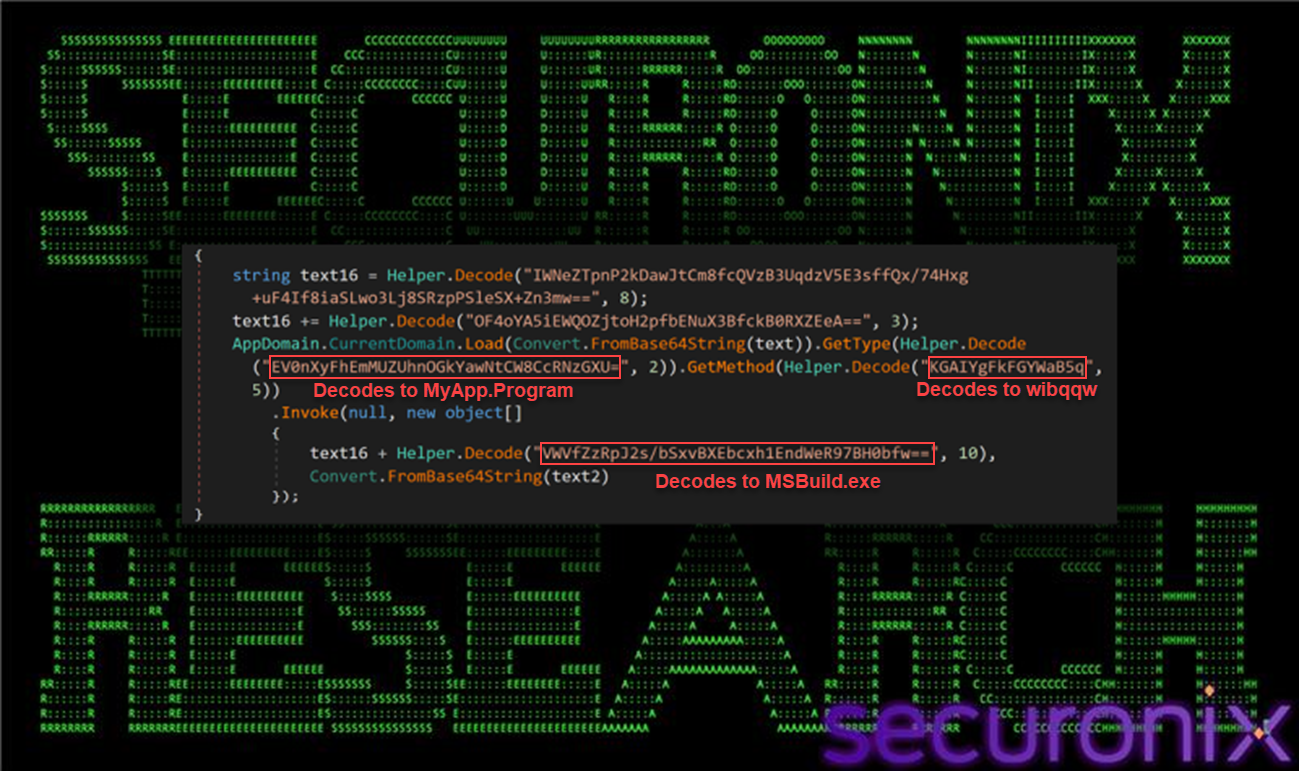
The complete SHADOW#REACTOR framework demonstrates how relatively common commodity tools can be operationalized within highly modular loader stacks to significantly increase stealth and defender friction.
Each stage adds incremental complexity while giving attackers flexibility to update individual components independently, allowing the campaign to operate at scale against enterprise environments through opportunistic, socially engineered delivery mechanisms.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
