A newly discovered advanced cloud-native Linux malware framework named VoidLink focuses on cloud environments, providing attackers with custom loaders, implants, rootkits, and plugins designed for modern infrastructures.
VoidLink is written in Zig, Go, and C, and its code shows signs of a project under active development, with extensive documentation, and likely intended for commercial purposes.
Malware analysts at cybersecurity company Check Point say that VoidLink can determine if it runs inside Kubernetes or Docker environments and adjust its behavior accordingly.

However, no active infections have been confirmed, which supports the assumption that the malware was created “either as a product offering or as a framework developed for a customer.”
The researchers note that VoidLink appears to be developed and maintained by Chinese-speaking developers, based on the interface locale and optimizations.
Source: Check Point
VoidLink capabilities
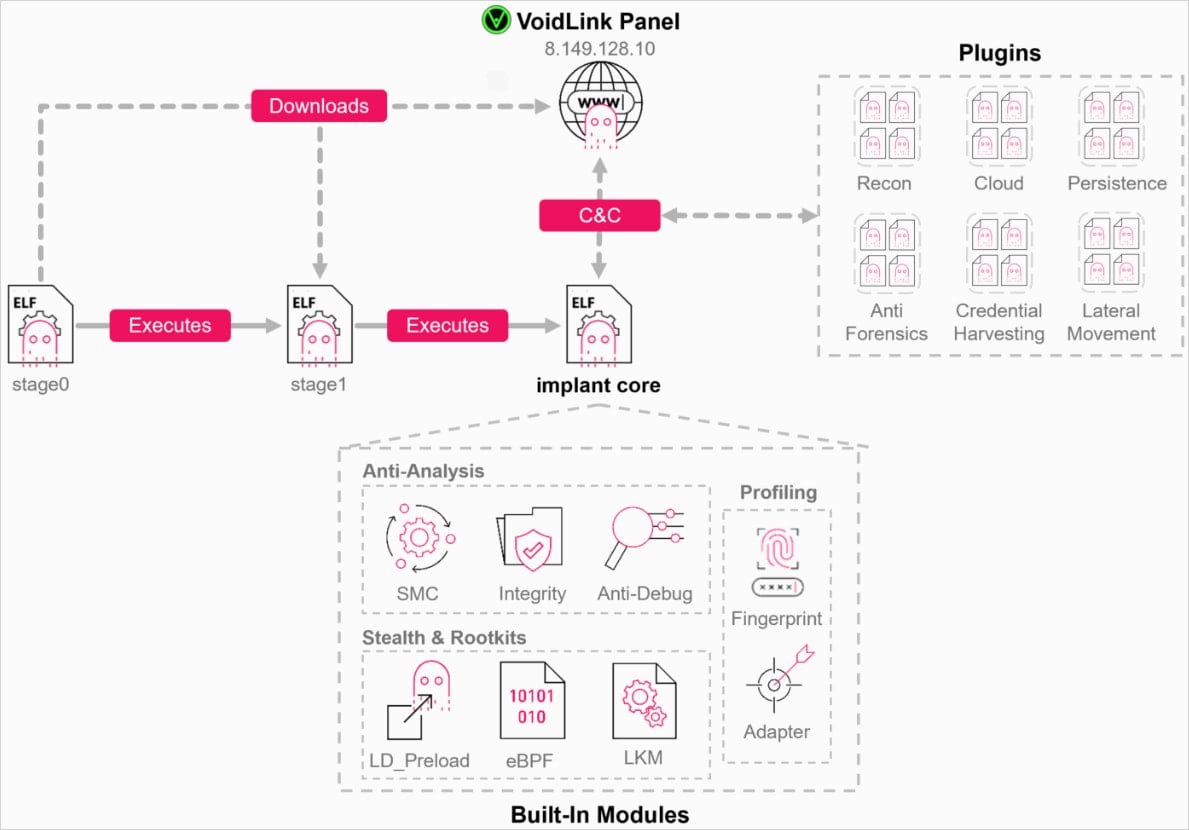
VoidLink is a modular post-exploitation framework for Linux systems that enables hackers to control compromised machines while staying hidden, extend functionality with plugins, and adapt behavior to specific cloud and container environments.
Once the implant is activated, it checks whether it is running in Docker or Kubernetes, and queries cloud instance metadata for providers such as AWS, GCP, Azure, Alibaba, and Tencent, with plans to add Huawei, DigitalOcean, and Vultr.
The framework collects system details such as the kernel version, hypervisor, processes, and network state, and scans for EDRs, kernel hardening, and monitoring tools.
All the information and a risk score calculated based on installed security solutions and hardening measures are delivered to the operator, allowing them to adjust module behavior, like slower port scanning and longer beaconing intervals.
The implant communicates with the operator using multiple protocols (HTTP, WebSocket, DNS tunneling, ICMP), wrapped in a custom encrypted messaging layer called ‘VoidStream’, which camouflages traffic to resemble normal web or API activity.
Source: Check Point
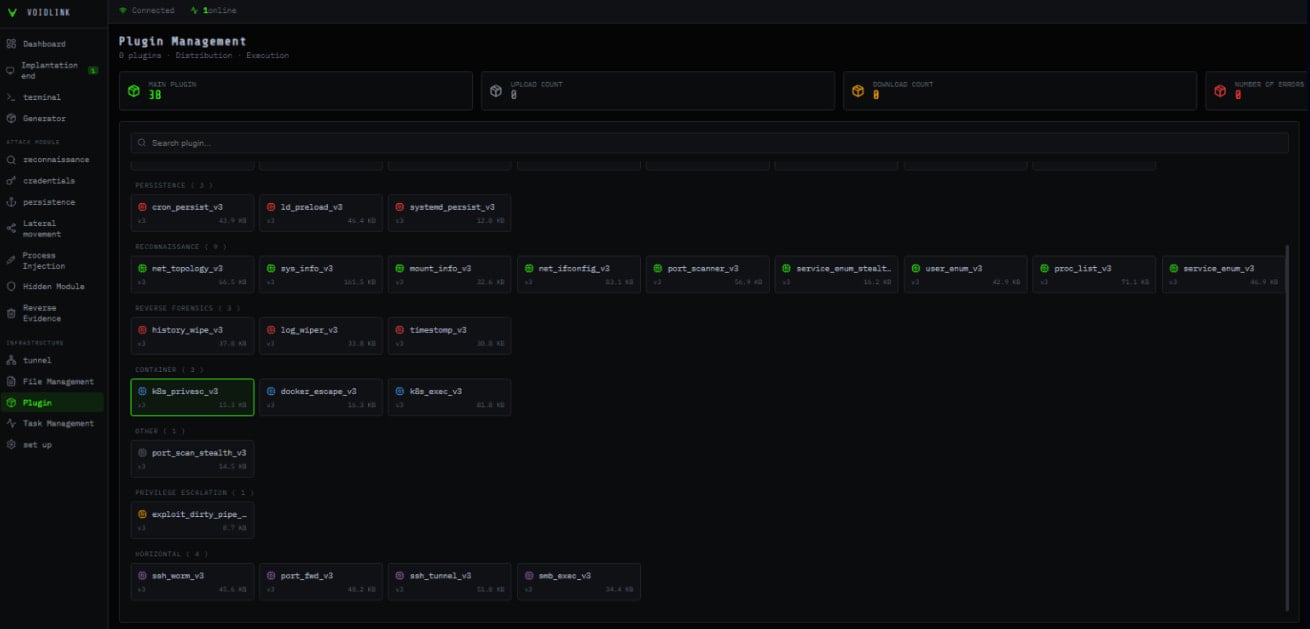
VoidLink’s plugins are ELF object files loaded directly into memory and call framework APIs via syscalls.
According to Check Point’s analysis, current VoidLink versions use 35 plugins in the default configuration:
- Reconnaissance (system, users, processes, network)
- Cloud and container enumeration and escape helpers
- Credential harvesting (SSH keys, Git credentials, tokens, API keys, browser data)
- Lateral movement (shells, port forwarding and tunneling, SSH-based propagation)
- Persistence mechanisms (dynamic linker abuse, cron jobs, system services)
- Anti-forensics (log wiping, history cleaning, timestomping)
Source: Check Point
To ensure these operations stay undetected, VoidLink uses a set of rootkit modules that hide processes, files, network sockets, or the rootkit itself.
Depending on the host’s kernel version, the framework uses LD_PRELOAD (older versions), LKMs (loadable kernel modules), or eBPF-based rootkits.
Additionally, VoidLink can detect debuggers in the environment, uses runtime code encryption, and performs integrity checks to detect hooks and tampering, all advanced anti-analysis mechanisms.
If tampering is detected, the implant self-deletes, and the anti-forensic modules erase logs, shell history, login records, and securely overwrite all files dropped on the host, minimizing exposure to forensic investigations.
Check Point researchers say that VoidLink is developed with stealth in mind, as it “aims to automate evasion as much as possible” by thoroughly profiling the targeted environment before choosing the best strategy.
They note that the new framework “is far more advanced than typical Linux malware” and is the work of developers with “a high level of technical expertise” and very skilled in multiple programming languages.
“The sheer number of features and its modular architecture show that the authors intended to create a sophisticated, modern and feature-rich framework,” the researchers say.
Check Point provides in the report today a set of indicators of compromise along with technical details about the modules and a list of discovered plugins.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
