Criminal infrastructure often fails for the same reasons it succeeds: it is rushed, reused, and poorly secured.
Security researchers recently demonstrated this vulnerability by exploiting the very malware infrastructure designed to steal victims’ credentials.
StealC Malware and Its Infrastructure Weaknesses
StealC is an infostealer malware distributed under a Malware-as-a-Service (MaaS) model since early 2023.
The malware targets cookies, passwords, and sensitive data from infected computers through a polished web panel that tracks campaigns.
However, in spring 2025, the StealC operation experienced significant setbacks when researchers discovered critical vulnerabilities in their infrastructure.
Following the release of StealC v2, the web panel code leaked publicly. During analysis, researchers identified an exploitable XSS (Cross-Site Scripting) vulnerability within the control panel.
This security flaw allowed researchers to monitor StealC operators’ activities, collect system fingerprints, track active sessions, and, ironically, steal session cookies from infrastructure designed explicitly for cookie theft.
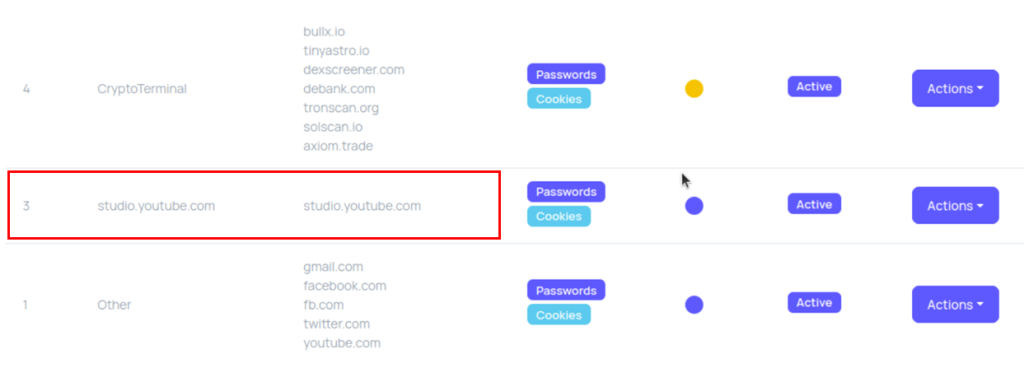
By exploiting the panel vulnerability, researchers identified a threat actor known as “YouTubeTA” who compromised over 5,000 victim machines.
The stolen data included more than 390,000 passwords and 30 million cookies. Screenshots captured by the malware showed victims searching for cracked versions of Adobe Photoshop and After Effects.
YouTubeTA’s distribution method involved hijacking legitimate YouTube channels with established subscriber bases and long posting histories, as reported by CyberArk.
After periods of inactivity, these compromised channels began promoting malware-laced cracked software downloads.
The StealC panel’s “markers” feature highlighted studio.youtube.com credentials, confirming the threat actor’s strategy of stealing YouTube creator accounts to perpetuate further infections.
Fingerprinting Reveals Single Operator Identity
Panel analysis revealed YouTubeTA operates as a single threat actor rather than an organized group.
Hardware fingerprinting showed consistent screen dimensions and WebGL renderer data indicating the use of an Apple M3 processor.
Language support showed English and Russian capabilities, while timezone data (GMT+0300, Eastern European Summer Time) narrowed the geographic location.
When the operator temporarily accessed the panel without VPN protection in July 2025, researchers captured an IP address associated with Ukrainian ISP TRK Cable TV, confirming Eastern European attribution consistent with other indicators.
This breach highlights inherent weaknesses in the MaaS model. While enabling individual operators like YouTubeTA to efficiently steal hundreds of thousands of credentials, the model creates supply chain vulnerabilities.
Poor security practices by StealC developers, including failure to implement httpOnly cookie protections, exposed their entire customer base to researcher monitoring.
This demonstrates how infrastructure flaws can simultaneously compromise multiple threat actors, providing valuable intelligence opportunities for security researchers and law enforcement.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
