Malicious Chrome extensions on the Chrome Web Store masquerading as productivity and security tools for enterprise HR and ERP platforms were discovered stealing authentication credentials or blocking management pages used to respond to security incidents.
The campaign was discovered by cybersecurity firm Socket, which says it identified five Chrome extensions targeting Workday, NetSuite, and SAP SuccessFactors, collectively installed more than 2,300 times.
“The campaign deploys three distinct attack types: cookie exfiltration to remote servers, DOM manipulation to block security administration pages, and bidirectional cookie injection for direct session hijacking,” reports Socket.

“The extensions target the same enterprise platforms and share identical security tool detection lists, API endpoint patterns, and code structures, indicating a coordinated operation despite appearing as separate publishers.”
The extensions were published under different names but the researchers say they share identical infrastructure, code patterns, and targeting. Four of the extensions were published under the developer name databycloud1104, while the fifth used different branding under the name Software Access.
While the extensions affected only 2,300 users, the theft of enterprise credentials could fuel large-scale ransomware and data theft attacks.
Marketed as tools for enterprise users
Socket says the extensions were promoted to users of enterprise HR and ERP platforms, presenting themselves as tools designed to improve productivity, streamline workflows, or enhance security controls.
Several of the extensions claimed to offer simplified access to “premium tools” for Workday, NetSuite, and other platforms.
One of the more popular extensions, Data By Cloud 2, was installed 1,000 times and promoted as a dashboard offering bulk management tools and faster access for users managing multiple enterprise accounts.
Another extension, Tool Access 11, positioned itself as a security-focused add-on that would restrict access to sensitive administrative features. Its listing claimed the extension could limit user interactions with “special tools” to prevent account compromise.
Other extensions in the group used similar language about providing “access” to tools and services, requesting permissions that appeared consistent with enterprise integrations.
However, Socket says none of the extensions disclosed cookie extraction, credential exfiltration, or the blocking of security administration pages. The privacy policies for the extensions also did not mention that user data would be collected.
Socket’s analysis of the extensions found they used a mix of malicious behavior, including authentication cookie exfiltration, administrative page blocking, and session hijacking via cookie injection.
Multiple extensions continuously extracted authentication cookies named “__session” for a targeted domain, which contain active login tokens for Workday, NetSuite, and SuccessFactors.
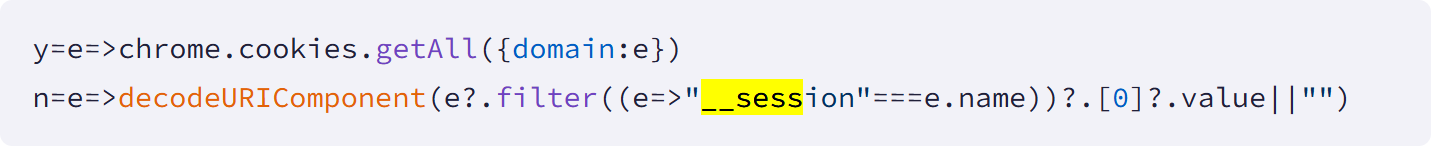
Source: Socket
These tokens were exfiltrated every 60 seconds to remote command-and-control servers, allowing attackers to maintain access even when users logged out and back in.
Two extensions, Tool Access 11 and Data By Cloud 2, blocked access to security and incident response pages within Workday. Using page title detection, the extensions either erased content on the pages or redirected administrators from management pages.
“Tool Access 11 targets 44 administrative pages including authentication policies, security proxy configuration, IP range management, and session controls,” explains Socket.
“Data By Cloud 2 expands this to 56 pages by adding password management, account deactivation, 2FA device controls, and security audit logs.”
Blocking access to these pages could prevent legitimate administrators from responding to security incidents if one is detected.
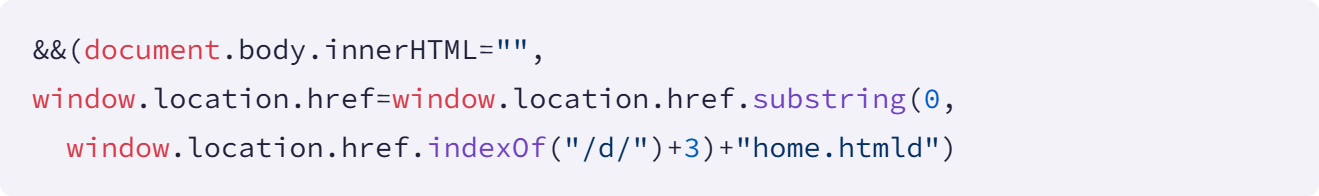
Source: Socket
Finally, Socket says the Software Access extension implemented the most malicious behavior by also including a feature that allows bidirectional cookie manipulation. In addition to stealing session tokens, the extension could receive stolen cookies from the attacker’s server and inject them directly into a browser.
By setting authentication cookies via the C2, the researchers say that the attackers could take over authenticated sessions without entering usernames, passwords, or multi-factor authentication codes. Socket says this enabled immediate account takeover across targeted enterprise platforms.
Socket says they reported the extensions to Google, and at the time of publishing this article, they appear to have been taken down.
Anyone who was using these extensions should report them to their security admins for further incident response and change their passwords on the targeted platforms.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
