Security researchers from Infoblox have successfully intercepted millions of malicious push notification advertisements by exploiting a DNS misconfiguration technique known as “lame nameserver delegation,” gaining complete visibility into a large-scale affiliate advertising operation without directly compromising any systems.
The researchers claimed to have identified abandoned domains used by threat actors, receiving copies of over 57 million logs over a two-week period that exposed widespread deceptive practices, scam activity, and brand impersonation targeting victims globally.
The attack leveraged a vulnerability called “Sitting Ducks,” where domain owners configure their domains to use external nameservers that lack information about those domains.
When researchers discovered that a malicious push notification network had abandoned several domains through lame delegation, they claimed the domains at the DNS provider without needing to register them.
Within an hour of taking control, their servers were flooded with traffic from victim devices sending detailed device information, user metrics, and advertisement data in unencrypted cleartext.
The researchers expanded their operation from monitoring one domain to nearly 120 misconfigured domains within a day, collecting 30 megabytes per second of logs.
This wasn’t a traditional adversary-in-the-middle attack the researchers occupied a position “on the side” of the threat actor’s infrastructure, passively receiving duplicate copies of every notification sent to victims.
Scale and Impact
The intercepted data revealed a global push notification advertising network delivering deceptive content to victims across more than 60 languages.
Victims received an average of 140 notifications daily, with some subscribed for over a year to the service.
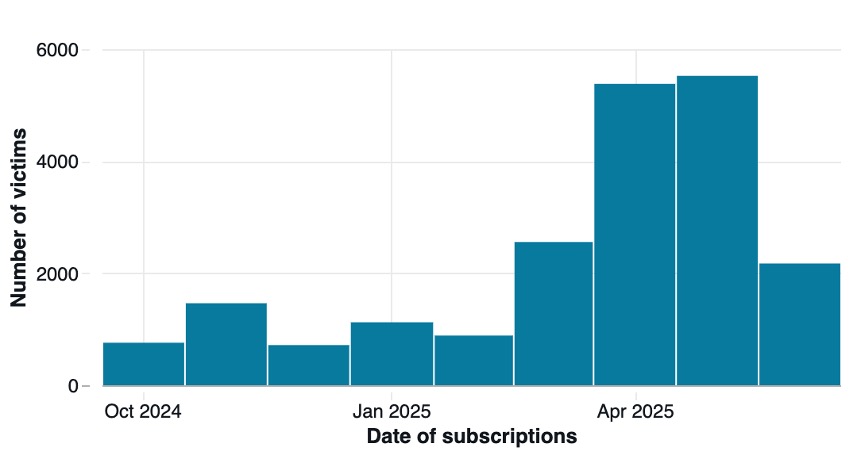
The notifications impersonated legitimate financial institutions including Bradesco, Sparkasse, MasterCard, Touch ‘n Go, and GCash, while also promoting gambling scams, fake security alerts, and adult content.
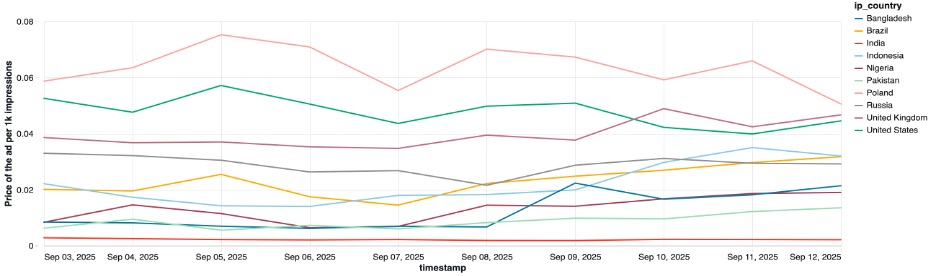
Geographic analysis showed that 50% of traffic targeted South Asia, particularly Bangladesh, India, Indonesia, and Pakistan.
Despite the massive scale, the operation’s economics were surprisingly poor the threat actor encoded click-through-rate estimates averaging just 1 in 60,000, with actual rates confirming these dismal numbers at approximately 630 clicks from 52 million advertisements.
Researchers estimated the operators generated only $350 daily from the monitored domains.
Security Implications
The research highlights critical DNS hygiene failures affecting both malicious actors and legitimate organizations.
Different delays mean that despite getting paid per 1000 ad impressions, this threat actor shows victims the same ad, up to 20 times per day.
The same Sitting Ducks technique has been exploited by threat actors like Vacant Viper to hijack dormant domains from legitimate companies and use them for malware distribution through traffic distribution systems like 404TDS.
Security experts warn that abandoned domains with lame delegations become “sitting ducks” that can be claimed repeatedly for different malicious campaigns, often without domain owners noticing the compromise.
Organizations must audit their DNS configurations to ensure all nameserver delegations are correctly maintained and that external nameservers have complete records for configured domains.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
