Security researchers have identified a sophisticated backdoor malware variant, PDFSIDER, that leverages DLL side-loading to evade endpoint detection and response (EDR) systems.
The threat demonstrates advanced persistent threat (APT) tradecraft, combining evasion mechanisms with encrypted command-and-control capabilities to maintain covert access on compromised systems.
PDFSIDER’s infection chain originates through spear-phishing campaigns delivering ZIP archives containing a legitimate executable signed with valid certificates.
The payload masquerades as PDF24 Creator, productivity software developed by Miron Geek Software GmbH, used for PDF creation and file conversion.
When victims execute the EXE file, it silently initializes without display, launching the malware’s infection sequence.
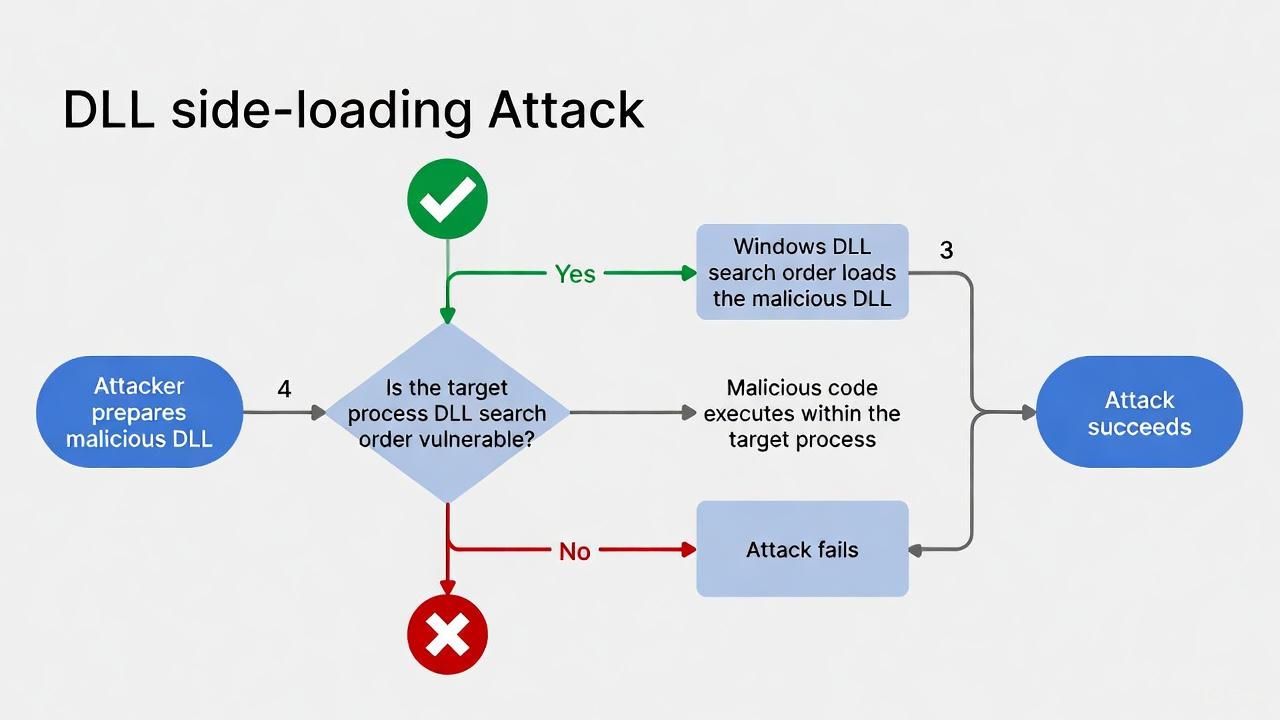
The attack noted known vulnerabilities in PDF24 software, allowing threat actors to deploy the malicious payload through DLL side-loading.
This technique positions a malicious cryptbase.dll adjacent to the legitimate PDF24.exe application, causing the legitimate process to load the attacker’s DLL instead of the authentic system library.
This approach effectively bypasses traditional EDR detection mechanisms that monitor suspicious DLL injection attempts.
Technical Architecture
Upon successful execution, PDFSIDER initializes Winsock connectivity and begins gathering system intelligence.
The PDF24.exe loads the attacker’s DLL instead of the real system cryptbase.dll, granting code execution.
The malware operates predominantly in memory, minimizing disk artifacts and reducing forensic visibility.
Command execution occurs through anonymous pipes constructed around cmd.exe, with the CREATE_NO_WINDOW flag ensuring no console window appears to the victim.
The malware extracts comprehensive system information, generates a unique system identifier, and transmits collected data to the attacker’s infrastructure.
This architecture enables threat actors to establish remote command shells with interactive capabilities, allowing arbitrary shell command execution and output exfiltration.
A critical technical indicator involves the embedded Botan 3.0.0 cryptographic library configured for AES-256-GCM authenticated encryption.
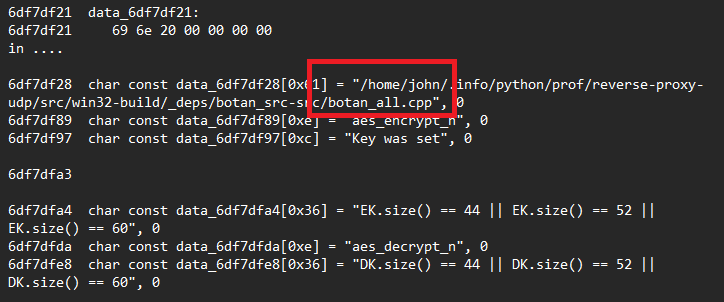
The malware implements AEAD (Authenticated Encryption with Associated Data) in Galois/Counter Mode, ensuring all inbound and outbound communications remain encrypted and authenticated.
This sophisticated cryptographic implementation indicates threat actors prioritize maintaining the integrity and confidentiality of their command channels typical of espionage-focused operations rather than financially motivated malware.
All sensitive data undergoes decryption exclusively in memory, preventing unencrypted artifacts from reaching disk. This approach substantially complicates detection by security monitoring tools and incident responders.
Threat actors provisioned C2 infrastructure through leased VPS services. The infrastructure funnels encrypted exfiltrated data through DNS port 53, obscuring malicious traffic within legitimate DNS communications.
Evasion Mechanisms
PDFSIDER incorporates multi-stage environment validation routines designed to detect sandboxes, virtual machines, and analysis laboratories.
The malware leverages the GlobalMemoryStatusEx function to assess system RAM capacity; systems with insufficient memory commonly associated with virtual environments trigger early termination.
Additionally, the malware implements debugger detection mechanisms, further ensuring execution only in authentic operational environments rather than controlled security analysis platforms.
PDFSIDER represents a sophisticated threat that demonstrates how traditional security tools can be circumvented through legitimate application exploitation and memory-resident execution.
Organizations should implement behavioral monitoring, elevated process execution controls, and cryptographic anomaly detection.
The incident underscores the critical importance of application patching and defense-in-depth strategies combining multiple detection layers.
Threat actors continue leveraging legitimate software vulnerabilities increasingly facilitated by AI-powered code analysis tools to maintain persistent, covert access within enterprise networks.
Indicators of Compromise (IOCs)
| File Name | MD5 Hash | Status |
|---|---|---|
| About.dll | e0e674ec74d323e0588973aae901b5d2 | Clean |
| Cryptbase.dll | 298cbfc6a5f6fa041581233278af9394 | Malicious |
| Language.dll | 80e4a29270b828c1f97d9cde9475fcbd | Clean |
| NotifyIcon.dll | 96ff508f9be007062b1770691f489e62 | Clean |
| Pdf24.exe | a32dc85eee2e1a579199050cd1941e1d | Clean |
| Settings.dll | 9f9dd5a432b4dde2160c7a7170e0d069 | Clean |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
