Security researchers and penetration testers gain a comprehensive open-source reconnaissance platform with the release of Argus v2.0, a Python-based information gathering toolkit that consolidates 135 specialised modules into a unified command-line interface.
The toolkit addresses the growing complexity of modern attack surface management by providing integrated access to network mapping, web application analysis, and threat intelligence gathering within a single framework.
Technical Architecture and Core Capabilities
Argus v2.0 represents a complete architectural overhaul from its predecessor, introducing a professional CLI with 25+ commands and multi-threaded execution.
Developed by Tunisian security researcher jasonxtn, Argus transforms fragmented reconnaissance workflows into streamlined operations through its modular architecture and concurrent execution capabilities.
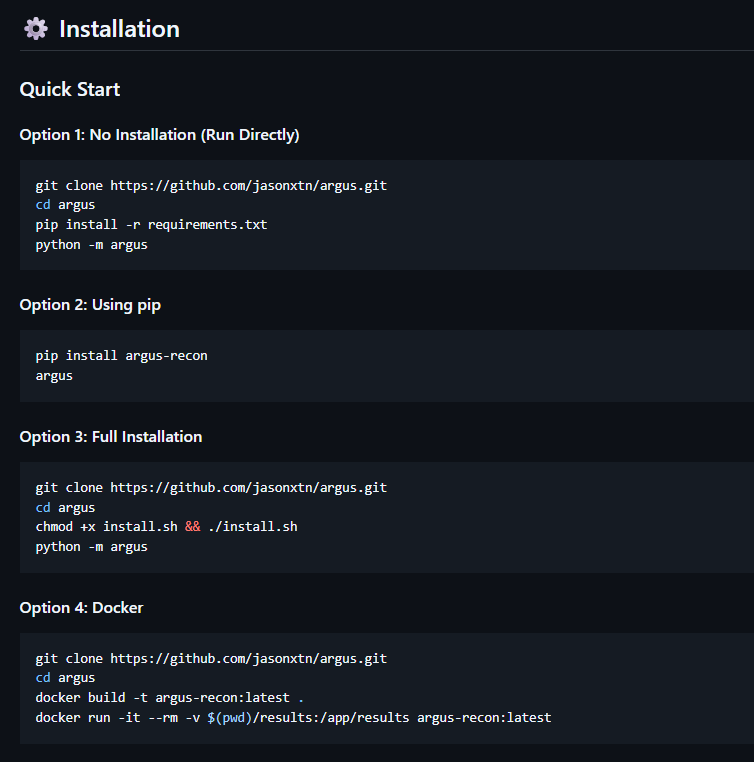
The toolkit supports four deployment methods: direct Python execution, pip installation, automated shell script deployment, and Docker containerization.
This flexibility enables security teams to deploy Argus across diverse operational environments, from isolated lab networks to cloud-based reconnaissance platforms.
The configuration system supports API integration with major threat intelligence services including Shodan, VirusTotal, Censys, Have I Been Pwned, and SSL Labs.
Users can manage credentials through environment variables or centralized settings files, enabling scalable deployment across security teams.
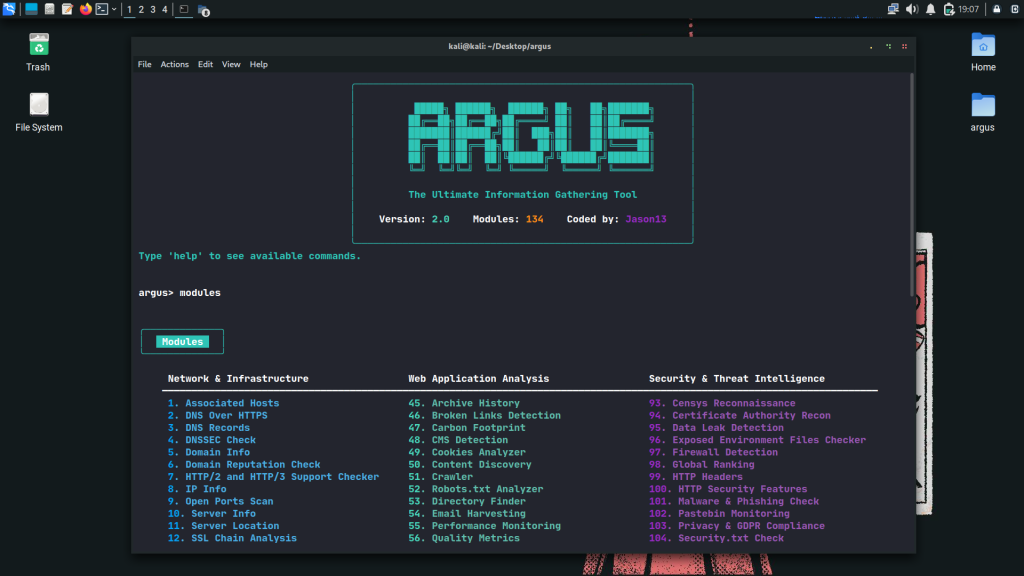
Argus organizes its 135 modules across three primary domains, providing comprehensive coverage of the modern attack surface:
| Category | Module Count | Key Capabilities |
|---|---|---|
| Network & Infrastructure | 52 modules | DNS analysis, SSL/TLS inspection, port scanning, ASN lookup, BGP routing analysis, SNMP enumeration |
| Web Application Analysis | 50 modules | CMS detection, crawler integration, CORS testing, API endpoint discovery, JavaScript analysis, vulnerability scanning |
| Security & Threat Intelligence | 33 modules | Malware/phishing checks, data leak detection, credential breach lookup, cloud exposure assessment, certificate transparency monitoring |
Network reconnaissance capabilities include DNSSEC validation, zone transfer detection, IPv6 reachability testing, and TLS cipher suite analysis.
The web application modules automate detection of misconfigurations, exposed repositories, and third-party script risks.
Security intelligence features integrate with external platforms to identify compromised credentials, malicious infrastructure, and data exposures.
Installation and Operational Workflow
Security practitioners can deploy Argus through multiple pathways. The pip installation method provides rapid deployment via pip install argus-recon, while the automated installer script configures complete development environments.
Docker support enables containerized operations with persistent volume mounting for results storage.
The interactive CLI supports batch operations, allowing analysts to execute multiple modules simultaneously against single or multiple targets.
Export capabilities include TXT, CSV, and JSON formats, facilitating integration with existing reporting pipelines and SIEM platforms.
Argus includes explicit legal disclaimers emphasizing educational and ethical use only. The author maintains no liability for misuse, requiring users to obtain explicit authorization before scanning target systems.
This positioning aligns with responsible disclosure practices and professional penetration testing standards.
Version 2.0’s breaking changes from the 1.x series demonstrate commitment to professional-grade tooling over backward compatibility.
The expansion from 50 to 135 modules indicates active development responsive to evolving reconnaissance requirements. Integration with established threat intelligence platforms suggests maturity suitable for production security operations.
For security teams managing complex attack surfaces, Argus v2.0 offers a compelling alternative to fragmented reconnaissance toolchains, consolidating critical intelligence gathering capabilities into a maintainable, extensible framework.
The combination of Python accessibility and comprehensive module coverage positions Argus as a valuable addition to offensive security toolkits and defensive monitoring arsenals alike.
Follow us on Google News, LinkedIn, and X to Get Instant Updates ancd Set GBH as a Preferred Source in Google.
