A severe vulnerability in Windows Server Message Block (SMB) client authentication has emerged as a critical threat to Active Directory environments.
CVE-2025-33073, a logical flaw in NTLM reflection handling, enables authenticated attackers to escalate to SYSTEM-level privileges and compromise domain controllers, potentially allowing them to take over entire Active Directory forests.
| Field | Value |
| CVE ID | CVE-2025-33073 |
| Vulnerability Title | Windows SMB Client NTLM Reflection Privilege Escalation |
| Affected Product | Windows SMB (Server Message Block) Client |
| Vulnerability Type | CWE-284: Improper Access Control |
| CVSS v3.1 Score | 8.8 |
Overview of the Vulnerability
Microsoft describes the vulnerability as “improper access control in Windows SMB.” However, security researchers have discovered the vulnerability is far more dangerous than initially characterized.
The flaw exploits NTLM local authentication mechanisms, allowing attackers to relay authentication from compromised machines back to themselves with SYSTEM privileges, bypassing traditional SMB signing protections.
The vulnerability leverages a sophisticated credential-coercion technique. Attackers register DNS records with specially crafted, marshalled target information (e.g., srv1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA) and use coercion methods such as PetitPotam to force machines to authenticate to attacker-controlled servers.
When the target detects the crafted DNS name, Windows SMB client libraries strip the marshalled information, leaving only the hostname (e.g., srv1).
The SMB client then signals the server to perform local NTLM authentication. This triggers a critical flaw: LSASS (Local Security Authority Subsystem Service) copies its SYSTEM token into a shared authentication context.
When attackers relay this authentication back to the target machine, they inherit SYSTEM privileges without requiring SMB signing to be disabled.
The attack succeeds because the vulnerability lies in the SMB client’s authentication negotiation process, not in signature enforcement.
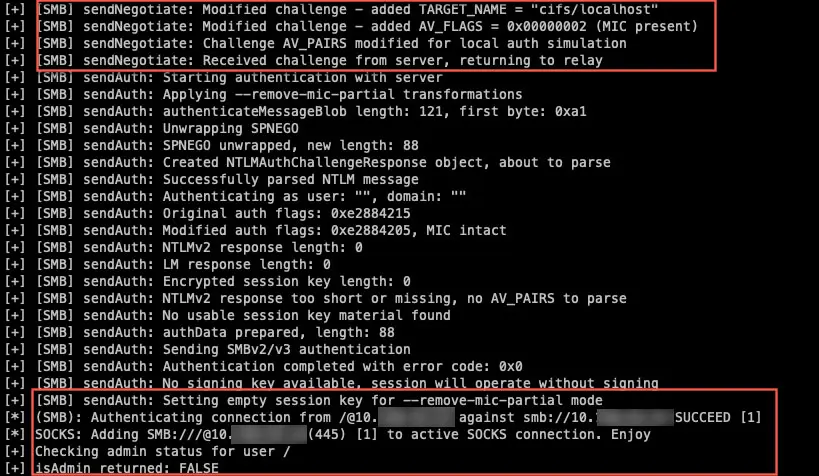
Even machines with SMB signing enabled remain vulnerable when relaying to LDAP, LDAPS, and other protocols through partial Message Integrity Code (MIC) removal techniques that exploit protocol-specific authentication handling.
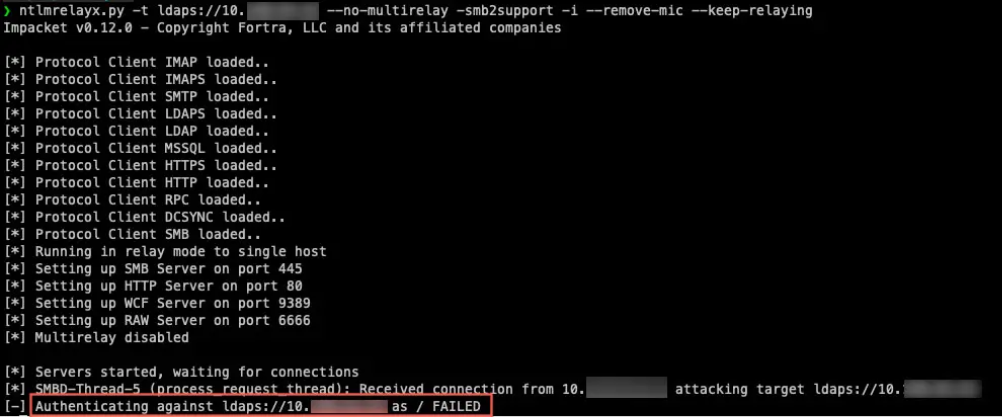
Security researchers have demonstrated that CVE-2025-33073 enables cross-protocol relay attacks previously thought impossible.
By stripping specific NTLMSSP flags (Negotiate Sign, Negotiate Seal) while preserving the MIC, attackers can relay SMB authentication to LDAP and LDAPS services on domain controllers.
This permits attackers to modify Active Directory objects directly adding compromised accounts to privileged groups, modifying access controls, or executing DCSync attacks to extract the entire credential database.
The vulnerability also extends to Kerberos reflection attacks, creating multiple attack vectors even on hardened environments.
Research indicates these techniques work across environments with channel binding and signing enforced, making traditional defenses insufficient.
Seven months after public disclosure, most organizations have failed to patch affected systems. Penetration testers consistently discover vulnerable hosts on enterprise networks, from workstations to domain controllers and tier-zero servers.
The exploitation process is trivial, using publicly available tools like ntlmrelayx.py, with partial MIC removal modifications, whichautomatically execute complete environment compromises.
According to depth security Immediate remediation requires installing Microsoft security updates and enforcing SMB signing universally across all domain-joined systems.
Organizations must also implement channel binding enforcement on LDAP and LDAPS services, restrict DNS record registration to administrative accounts only, and segment broadcast domains to prevent network-level exploitation vectors.
 SMB Relay with Signing” class=”wp-image-175362″ srcset=”https://gbhackers.com/wp-content/uploads/2026/01/image-80.png 819w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-300×174.png 300w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-768×446.png 768w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-723×420.png 723w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-150×87.png 150w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-696×405.png 696w” sizes=”auto, (max-width: 819px) 100vw, 819px”/>
SMB Relay with Signing” class=”wp-image-175362″ srcset=”https://gbhackers.com/wp-content/uploads/2026/01/image-80.png 819w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-300×174.png 300w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-768×446.png 768w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-723×420.png 723w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-150×87.png 150w, https://gbhackers.com/wp-content/uploads/2026/01/image-80-696×405.png 696w” sizes=”auto, (max-width: 819px) 100vw, 819px”/>Additionally, blocking all NetNTLMv1 authentication and enforcing Kerberos exclusively reduces attack surface.
However, organizations should note that Kerberos reflection attacks also pose significant risks without proper defenses.
The vulnerability represents a fundamental flaw in NTLM reflection mitigations not a simple signing bypass and demands comprehensive authentication hardening as an immediate priority.
Follow us on Google News, LinkedIn, and X to Get Instant Updates ancd Set GBH as a Preferred Source in Google.
