On January 13, 2026, Check Point Research published its analysis of VoidLink, a Chinese-developed Linux malware framework designed to target cloud environments.
Following this disclosure, the Sysdig Threat Research Team (TRT) examined VoidLink’s binaries to understand its loader chain, rootkit internals, and control mechanisms.
VoidLink’s most significant innovation addresses a persistent challenge in Linux malware: the lack of kernel module portability.
Traditional LKM rootkits embed pre-compiled modules for specific kernel versions, severely limiting compatibility. VoidLink solves this through Server-Side Rootkit Compilation (SRC), where the C2 server dynamically builds kernel modules on demand for each target’s specific kernel version.
When the implant requests compilation via POST to /compile, it transmits kernel metadata (kernel release, available compilers, and header availability).
The findings reveal an unprecedented approach to kernel portability that fundamentally challenges how defenders must understand cross-platform rootkit deployment.
The C2 responds with a compiled module eBPF, hybrid, or LKM matched precisely to the target environment.
This architecture is unprecedented in documented malware. Previous frameworks like Krasue RAT embedded seven pre-compiled rootkits (covering only specific versions), while Drovorub relied on a single pre-compiled module.
VoidLink’s approach removes this limitation entirely, supporting unlimited kernel versions without requiring client-side build tools or bloating the 1.2MB implant.
Chinese Development With AI Fingerprints
Technical analysis indicates professional developers combined with AI-assisted code generation.
The embedded kernel source contains extensive Chinese comments demonstrating genuine expertise including awareness of the Linux 5.7 change where kallsyms_lookup_name stopped being exported, requiring kprobe-based workarounds.
Simultaneously, evidence of AI assistance includes uniform debug formatting across modules, placeholder data (“John Doe” in templates), and consistent _v3 versioning across all plugins (BeaconAPI_v3, docker_escape_v3, timestomp_v3).
The most likely scenario involves skilled Chinese-speaking developers using AI to accelerate boilerplate generation while providing core architectural and security expertise themselves.
VoidLink profiles installed security products in real-time, detecting CrowdStrike, SentinelOne, Carbon Black, Falco, Wazuh, OSSEC, osquery, and auditd through process enumeration and path probing.
Upon detection, the malware adjusts beacon timing from aggressive (4096ms base delay with 20% jitter) to paranoid (1024ms base delay with 30% jitter).
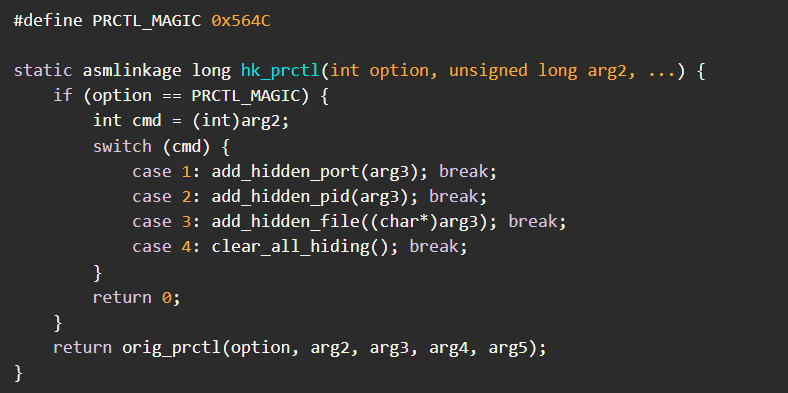
The framework provides three control channels for redundancy: prctl magic interface (local rootkit control via 0x564C magic value), Berkeley Packet Filter map updates (for eBPF-based stealth), and ICMP covert channel (allowing remote commands via ping packets with 0xC0DE magic ID).
This triple-layer approach ensures persistence even when primary C2 channels are disrupted.
Detection Despite Sophistication
Despite advanced evasion, VoidLink remains detectable through runtime monitoring. Sysdig Secure users have rules available targeting rootkit installation, fileless execution, kernel module injection, and eBPF loading.
Falco’s default ruleset includes detection for memfd_create-based fileless execution. The distinctive syscall sequence fork, prctl(PR_SET_NAME), socket, connect, memfd_create, and execveat creates a recognizable behavioral signature.
VoidLink’s specialized Kubernetes and container escape capabilities, combined with cloud-native detection (AWS, GCP, Alibaba, Tencent metadata endpoints), position it as a serious threat to modern infrastructure.
Organizations must prioritize runtime threat detection over static signatures, as VoidLink actively adapts to evade conventional security tools.
The framework’s maturity including a complete C2 dashboard, 37 operational plugins, and mesh networking capabilities suggests sustained development effort and real-world operational deployment potential.
Indicators of Compromise
| Stage/Type | Description | Hash (SHA256 or similar) |
|---|---|---|
| Stage 0 | Dropper | 70aa5b3516d331e9d1876f3b8994fc8c18e2b1b9f15096e6c790de8cdadb3fc9 |
| Stage 1 | Dropper | 13025f83ee515b299632d267f94b37c71115b22447a0425ac7baed4bf60b95cd |
| Implant | Remote-compile | 4c4201cc1278da615bacf48deef461bf26c343f8cbb2d8596788b41829a39f3f |
| Self-compile variant | — | 05eac3663d47a29da0d32f67e10d161f831138e10958dcd88b9dc97038948f69 |
| Zig debug variant | — | 15cb93d38b0a4bd931434a501d8308739326ce482da5158eb657b0af0fa7ba49 |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
