Seqrite Labs has uncovered a sophisticated spear-phishing campaign targeting Argentina’s judicial sector with a multi-stage infection chain designed to deploy a stealthy Rust-based Remote Access Trojan (RAT).
The campaign primarily targets Argentina’s judicial institutions, legal professionals, justice-adjacent government bodies, and academic legal organizations.
Attackers abuse legitimate Argentine federal court rulings specifically, preventive detention review documents to establish credibility and facilitate successful malware delivery.
The initial vector leverages targeted spear-phishing emails containing a weaponized ZIP archive with three components: a malicious LNK file (info/juicio-grunt-posting.pdf.lnk), a BAT-based loader script (info/health-check.bat), and an authentic-looking judicial PDF decoy (info/notas.pdf).
The operation, named Operation Covert Access, demonstrates advanced social engineering tactics combined with robust anti-analysis mechanisms to achieve persistent access within judicial institutions and legal organizations across South America.
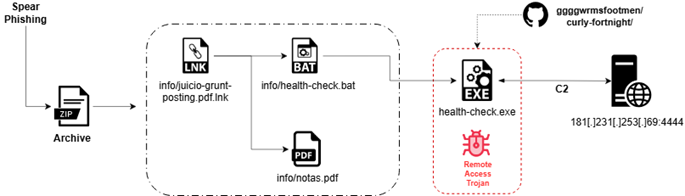
When users interact with the LNK file, the execution chain initiates silently while displaying the decoy document to the victim, enabling stealthy payload deployment without triggering suspicion.
Decoy Document Analysis
The decoy document is a legitimate-appearing Argentine federal court resolution written in formal legal Spanish, purporting to originate from the Poder Judicial de la Nación and referencing the real Tribunal Oral en lo Criminal y Correccional N° 2 de la Capital Federal.
It discusses judicial review of preventive detention with conditional release provisions, complete with case numbering, judicial signatures, and procedural language citing specific articles of the Argentine Criminal Procedure Code.
The document’s structure, terminology, and formatting closely mirror authentic court rulings, significantly increasing credibility among legal professionals and substantially increasing the likelihood of user interaction.
Stage 1 involves the LNK file executing PowerShell from the system directory with execution policy bypass and hidden window mode. The shortcut contains a PDF icon disguising the malicious shortcut as a legitimate document.
Stage 2 features the BAT loader establishing connections to GitHub-hosted repositories to retrieve the second-stage payload.
The PowerShell command uses spoofed User-Agent strings and saves the downloaded executable (health-check.exe) as msedge_proxy.exe within the Microsoft Edge user data directory to appear legitimate.
Stage 3 deploys msedge_proxy.exe, the primary RAT component, which performs extensive anti-analysis checks including VM detection (VMware, VirtualBox, Hyper-V, QEMU, Xen, Parallels), sandbox environment detection, and debugger identification through PEB checks and timing-based analysis.
The RAT collects system information, including hostname, username, OS name, and privilege levels, then establishes C2 communication using fallback mechanisms supporting both IPv4 and IPv6, defaulting to 181.231.253.69:4444.
Command and Control Capabilities
The malware advertises a comprehensive command set including PERSIST for persistence installation, DOWNLOAD and UPLOAD for file operations, HARVEST for credential theft, ENCRYPT and DECRYPT for ransomware functionality, and ELEVATE for privilege escalation.
All commands arrive Base64-encoded, with the RAT supporting modular post-exploitation capabilities including DLL-based ransomware, stealer modules, and complete persistence lifecycle management.
The RAT implements multiple persistence techniques through registry Run keys using randomized legitimate-looking value names (SecurityHealthSystray, MicrosoftEdgeAutoLaunch, Teams Machine Installer) and scheduled tasks via schtasks with elevated privileges.
A dedicated PERSIST_REMOVE command enables complete cleanup capability, deleting all registry entries and scheduled tasks upon operator command.
Operation Covert Access demonstrates the continued effectiveness of socially engineered intrusion chains targeting high-trust institutional environments.
Organizations should implement enhanced email filtering for spoofed legal documents, disable LNK file execution from email sources, enforce PowerShell execution policies, and deploy endpoint detection and response solutions capable of identifying suspicious process chains and C2 communications patterns.
IOCs
| Hash | Name / File Path | C2 Server |
|---|---|---|
| dc802b8c117a48520a01c98c6c9587b5 | info/juicio-grunt-posting.pdf.lnk | |
| 45f2a677b3bf994a8f771e611bb29f4f | D:auto_black_abuseresourcesunzipped20251215_140518_2025-11-2813adde53bd767d17108786bcc1bc0707c2411a40f11d67dfa9ba1a2c62cc5cf3.zip | |
| 02f85c386f67fac09629ebe5684f7fa0 | info/health-check.bat | |
| 976b6fce10456f0be6409ff724d7933b | msedge_proxy.exe | |
| 233a9dbcfe4ae348c0c7f4c2defd1ea5 | info/notas.pdf | |
| — | — | 181.231.253.69:4444 |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
