Gootloader malware has resurfaced, employing sophisticated evasion techniques to exploit malformed ZIP archives and obfuscation mechanisms to bypass security detection systems.
The Gootloader malware campaign, tracked as a partnership between Storm-0494 and Vanilla Tempest, has returned in late 2025 with an alarming ability to evade detection.
The threat operates through a specialized delivery mechanism a deliberately malformed ZIP archive designed to thwart automated analysis while remaining executable on victim systems running Windows.
This architectural approach, combined with hashbusting and custom obfuscation techniques, explains why Gootloader consistently maintains low detection rates across enterprise security tools.
The ZIP Archive as a Defense Evasion Weapon
When users receive Gootloader, they download what appears to be a standard ZIP file containing a JScript file.
However, the archive is intentionally malformed to create a detection gap. The ZIP format stores its directory structure at the end of the file, meaning a tool reads from the file’s tail backward to interpret contents.
Gootloader exploits this architectural detail by concatenating 500 to 1,000 identical ZIP archives together sequentially.
Because ZIP parsers begin at the end, only the final archive’s directory gets read, while hundreds of preceding structures remain unused.
The practical result: victim systems using Windows’ native unarchiver extract the malicious JScript successfully, yet specialized analysis tools like 7-Zip, WinRAR, and even VirusTotal’s extraction utilities fail or produce corrupted output.
The archive’s “End of Central Directory” structure is further truncated, missing two critical bytes from the standardized format specification.
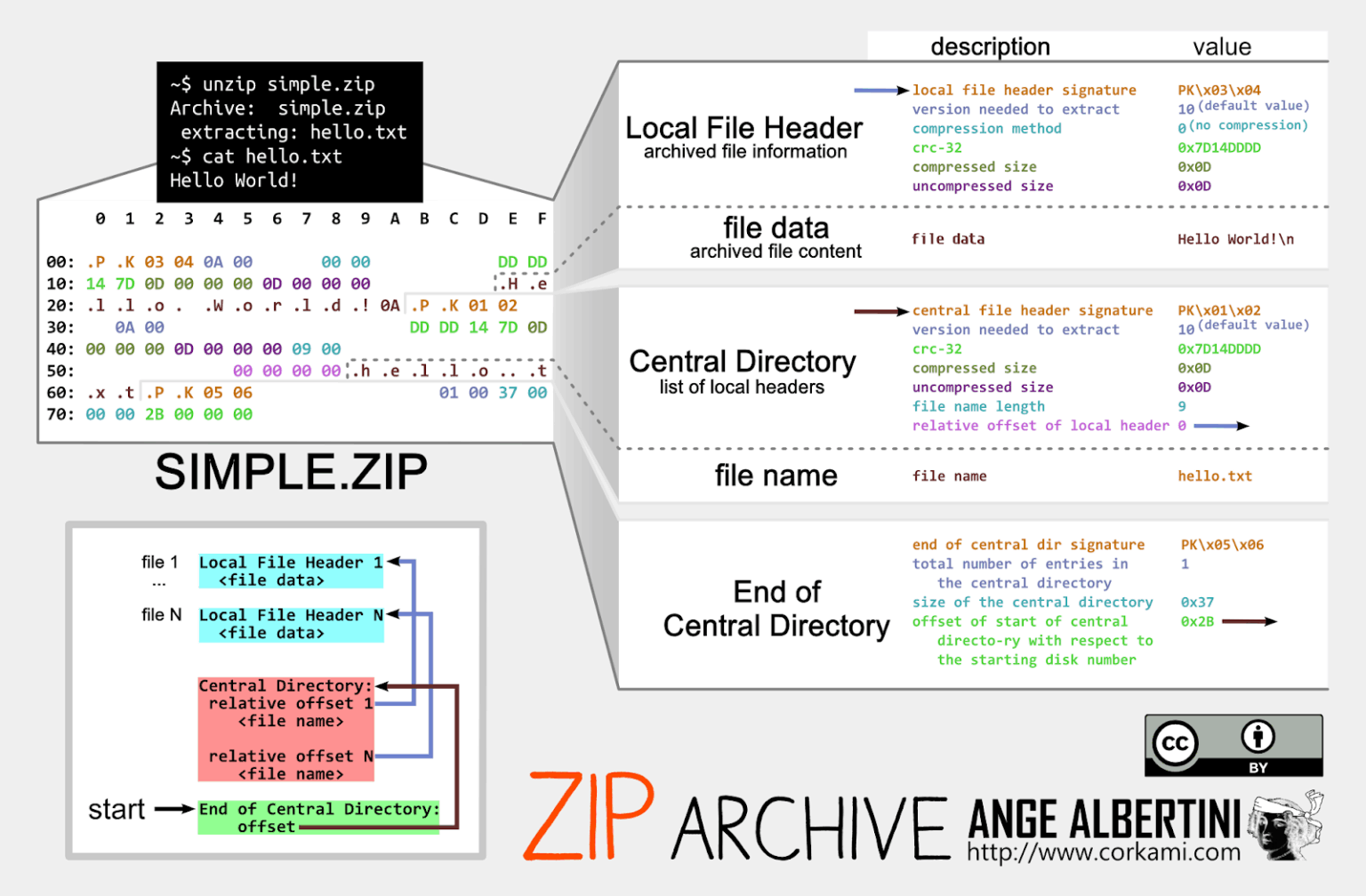
This truncation causes parsing errors in tools attempting to verify the archive’s integrity. Additionally, Gootloader randomizes non-critical header fields such as “Disk Number” and “Number of Disks,” causing certain unarchiving utilities to expect multi-part archives that never exist.
These modifications combine to create what researchers term a “hashbusting” defense every user downloading Gootloader receives a cryptographically unique file, rendering signature-based detection ineffective.
Why This Matters for Defenders
The Gootloader developer has maintained involvement with ransomware operations since at least 2020, specifically handling initial access their responsibility is delivering working malware that bypasses defenses and executes successfully.
In years prior, Gootloader malware comprised approximately 11 percent of all malware observed circumventing enterprise security tools.
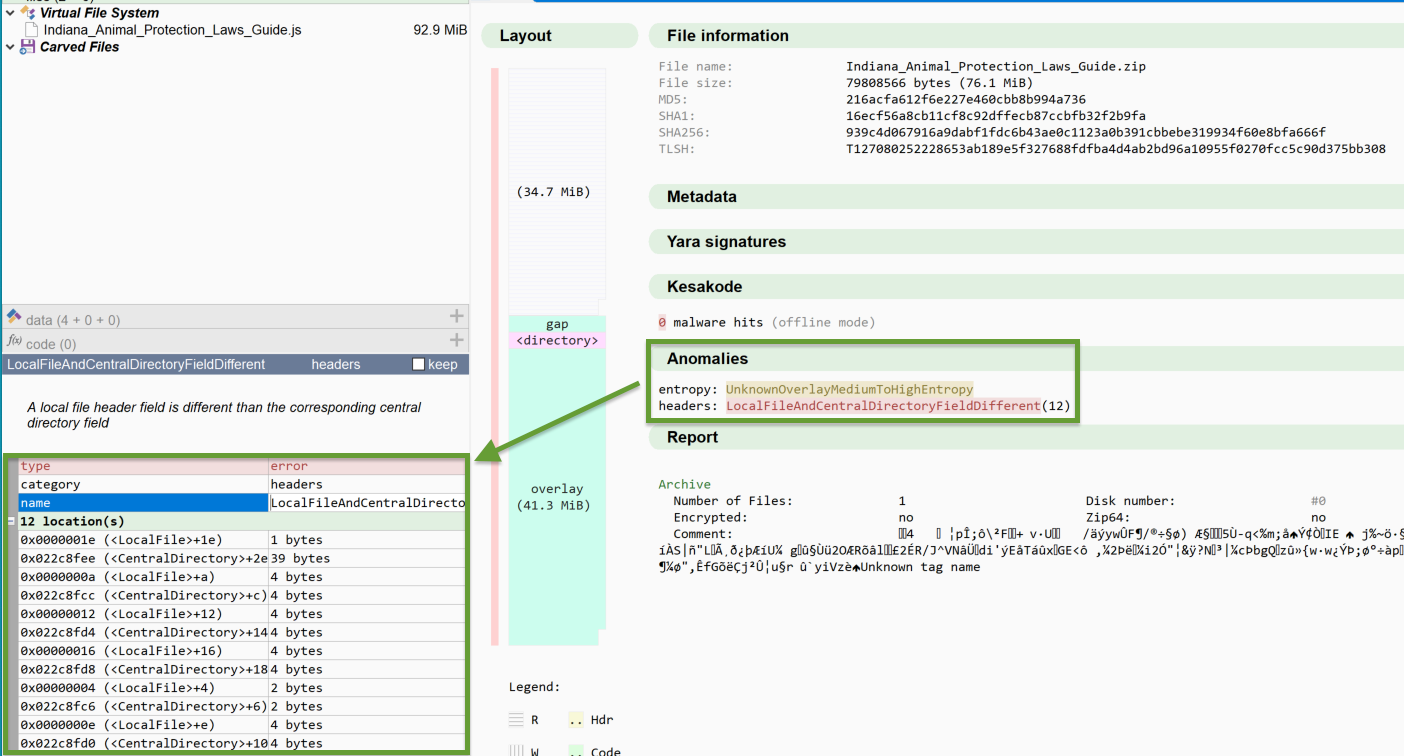
Malcat’s anomaly engine highlighted one of the other issues with the ZIP archives: multiple elements of the local file’s metadata differ from what’s in the central directory.
The November 2025 campaign reactivation, following collaboration between Storm-0494 and threat actor Vanilla Tempest (currently deploying Rhysida ransomware), indicates this capability remains highly valued within criminal ecosystems.
Recent observations by Huntress reveal additional sophistication: the actor now embeds custom WOFF2 font files within JavaScript code using Z85 encoding, transforming what appears as gibberish character sequences in source code into legitimate filenames when rendered in browsers.
This technique defeats static string analysis keyword searches for “invoice,” “contract,” or “agreement” return nothing because those words never exist in the source code itself, only as substituted glyphs at runtime. The practical consequence is that traditional content inspection fails.
When the JScript executes (typically via Windows Script Host after double-clicking the malicious file), it establishes persistence through a newly modified approach.
The malware drops two shortcut files (.LNK) and additional JScript files into the user’s AppData directory and Startup folder. Notably, the shortcuts reference their targets using Windows 8.3 short filenames legacy aliases like “MOLECU1.LNK” instead of “Molecular Ecology.lnk.”
These short filename references, generated automatically by NTFS for compatibility with older systems, appear rarely in modern environments, creating a behavioral anomaly worth monitoring.
The attack sequence occurs with alarming speed. Reconnaissance from deployed backdoors (Supper SOCKS5) begins within 20 minutes of execution.
Domain Controller compromise has been observed within 17 hours of initial infection, enabling attackers to create privileged accounts and execute Volume Shadow Copy enumeration typical precursor activity before ransomware deployment.
Defenders should implement dynamic detection methodologies rather than relying on static signatures, given Gootloader’s continuous hashing of payloads.
Monitoring for abnormal ZIP archive characteristics specifically files with 100+ concatenated archive structures and truncated End of Central Directory records provides an early detection vector.
Process monitoring should flag WScript executing JScript files from the AppDataLocalTemp directory, where ZIP extraction occurs by default. Additionally, changing the default application association for .JS files from Windows Script Host to Notepad prevents accidental execution while maintaining legitimate scripting capability for experienced users.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
