Hacktivists became significantly more dangerous in 2025, moving beyond their traditional DDoS attacks and website defacements to target critical infrastructure and ransomware attacks.
That’s one of the conclusions of a new blog post from Cyble adapted from the threat intelligence company’s 2025 Threat Landscape report.
The trend began in earnest with Z-Pentest’s targeting of industrial control systems (ICS) in late 2024, and grew from there. Cyble said it expects those attacks to continue to grow in 2026, along with growing use of custom tools by hacktivists and “deepening alignment between nation-state interests and hacktivists.”
Hacktivist Attacks on Critical Infrastructure Soar
Z-Pentest was the most active of the hacktivist groups targeting ICS, operational technology (OT) and Human Machine Interface (HMI) environments. Dark Engine (Infrastructure Destruction Squad) and Sector 16 also persistently targeted ICS environments, while Golden Falcon Team, NoName057(16), TwoNet, RipperSec, and Inteid also claimed multiple ICS attacks.
HMI and web-based Supervisory Control and Data Acquisition (SCADA) interfaces were the systems most frequently targeted by hacktivists. Virtual Network Computing (VNC) environments were targeted less frequently, but “posed the greatest operational risks to several industries,” Cyble said.
Building Management Systems (BMS) and Internet of Things (IoT) or edge-layer controllers were also targeted by the groups, reflecting a wider trend toward exploiting poorly secured IoT interfaces.

Europe was the primary region targeted by pro-Russian hacktivist groups, with Spain, Italy, the Czech Republic, France, Poland, and Ukraine the most frequent targets of those groups.
State Interests and Hacktivism Align
Cyble also noted increasing alignment between hacktivist groups and state-aligned interests.
When Operation Eastwood disrupted NoName057(16)’s DDoS infrastructure in July 2025, the group rapidly rebuilt its capacity and resumed operations against Ukraine, the EU, and NATO, “underscoring the resilience of state-directed ecosystems,” Cyble said.
U.S. indictments “further exposed alleged structured cooperation between Russian intelligence services and pro-Kremlin hacktivist fronts,” the blog post said. The Justice Department revealed GRU-backed financing and direction of the Cyber Army of Russia Reborn (CARR) and state-sanctioned development of NoName057(16)’s DDoSia platform. Z-Pentest has also been identified as part of the CARR ecosystem and linked to GRU.
Pro-Ukrainian hacktivist groups are less formally connected to state interests, but groups like the BO Team and the Ukrainian Cyber Alliance launched data destruction, encryption and wiper attacks targeting “key Russian businesses and state machinery,” and Ukrainian actors also claimed to pass exfiltrated datasets to national intelligence services.
Hacktivist groups Cyber Partisans BY (Belarus) and Silent Crow significantly compromised Aeroflot’s IT environment in a long-term breach, claiming to exfiltrate more than 20TB of data, sabotaging thousands of servers, and disrupting airline systems, a breach that was confirmed by Russia’s General Prosecutor.
Other hacktivists aligned with state interests include BQT.Lock (BaqiyatLock, aligned with Hezbollah) and Cyb3r Av3ngers/Mr. Soul Team, which has been linked to Iran’s Islamic Revolutionary Guard Corps (IRGC) and has also targeted critical infrastructure.
Hacktivist Sightings Surge 51%
Cyble said hacktivist sightings surged 51% in 2025, from 700,000 in 2024 to 1.06 million in 2025, “with the bulk of activity focused on Asia and Europe.”
“Pro-Russian state-aligned hacktivists and pro-Palestinian, anti-Israel collectives continued to be the primary drivers of hacktivist activity throughout 2025, shaping the operational tempo and geopolitical focus of the threat landscape,” the researchers said.
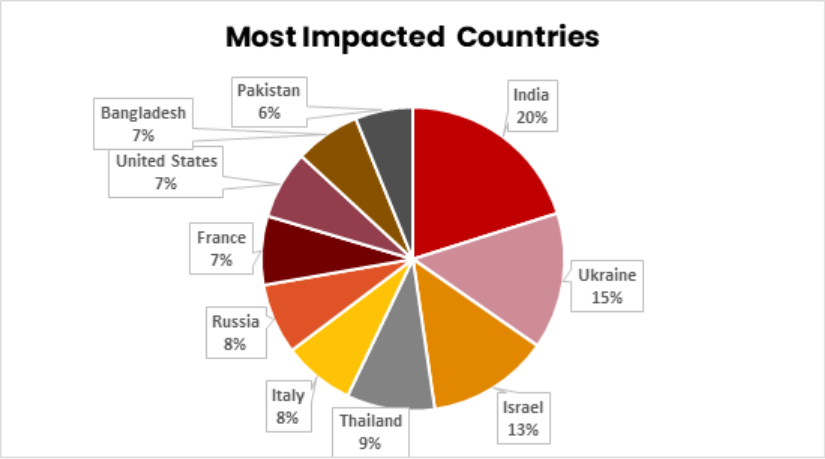
India, Ukraine and Israel were the countries most targeted by hacktivist activity in 2025 (chart below).

Government & Law Enforcement, Energy & Utilities, Education, IT, Transportation & Logistics, and Manufacturing saw the most growth in hacktivist attacks, while the Agriculture & Livestock, Food & Beverages, Hospitality, Construction, Automotive, and Real Estate also saw increasing attack numbers.
“Hacktivism has evolved into a geopolitically charged, ICS-focused threat, continuing to exploit exposed OT environments and increasingly weaponizing ransomware as a protest mechanism,” Cyble said.
“In 2026, hacktivists and cybercriminals will increasingly target exposed HMI/SCADA systems and VNC takeovers, aided by public PoCs and automated scanning templates, creating ripple effects across the energy, water, transportation, and healthcare sectors,” the researchers predicted.
