An operational security failure allowed researchers to recover data that the INC ransomware gang stole from a dozen U.S. organizations.
A deep forensic examination of the artifacts left behind uncovered tooling that had not been used in the investigated attack, but exposed attacker infrastructure that stored data exfiltrated from multiple victims.
The operation was conducted by Cyber Centaurs, a digital forensics and incident response company that disclosed its success last November and now shared the full details with BleepingComputer.

The Cyber Centaurs investigation began after a client U.S. organization detected ransomware encryption activity on a production SQL Server.
The payload, a RainINC ransomware variant, was executed from the PerfLogs directory, which is typically created by Windows. However, ransomware actors have begun to use it more frequently for staging.
The researchers also noticed the presence of artifacts from the legitimate backup tool Restic, although data exfiltration had occurred during the lateral movement stage and the threat actor had not used the utility in this attack.
This caused a shift in the researchers’ investigation “from incident response to infrastructure analysis.”
The traces that INC ransomware left behind included renamed binaries (like ‘winupdate.exe’), PowerShell scripts to execute Restic, hardcoded repository configuration variables, and backup commands.
Restic-related remnants indicated that the threat actor was using the backup tool selectively as part of its operational toolkit.
One of the discovered PowerShell scripts, ‘new.ps1’, contained Base64-encoded commands for Restic and included hardcoded environment variables used to run the tool (access keys, repository paths, and S3 passwords for encrypted repositories).
“If INC routinely reused Restic-based infrastructure across campaigns, then the storage repositories referenced in attacker scripts were unlikely to be dismantled once a ransom event concluded,” the researchers theorized.
“Instead, those repositories would likely persist as long-lived attacker-controlled assets, quietly retaining encrypted victim data well after negotiations ended or payments were made.”
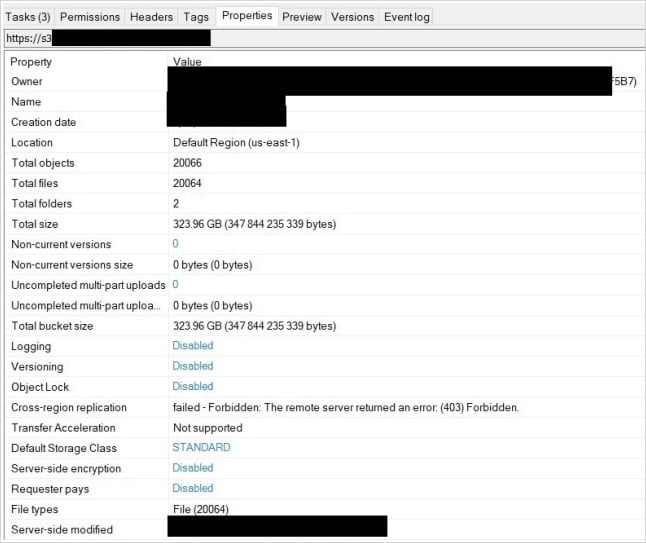
If this were the case, data stolen from other organizations could still be available in an encrypted form and could potentially be recovered from the backup server.
To validate this hypothesis, the team developed a controlled, non-destructive enumeration process that confirmed the presence of encrypted data stolen from 12 unrelated organizations in the healthcare, manufacturing, technology, and service sectors in the United States.
None of the organizations were Cyber Centaurs clients, and the incidents were unrelated, distinct ransomware events.
Source: Cyber Centaurs
The researchers then decrypted the backups and preserved the copies while contacting law enforcement to help validate ownership and guide them through the proper procedure.
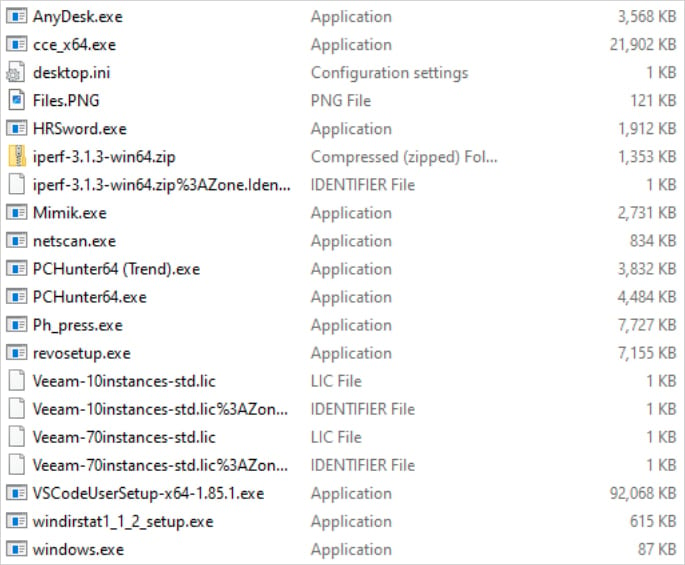
The Cyber Centaurs report lists multiple tools used in INC ransomware attacks, which include, among others, cleanup tools, remote access software, and network scanners.
Source: Cyber Centaurs
The researchers also created YARA and Sigma rules to help defenders detect the Restic backup tool or its renamed binaries in the environment or running from suspicious locations, which could signal a ransomware attack in development.
INC ransomware is a ransomware-as-a-service (RaaS) operation that emerged in mid-2023.
The threat actor claimed several high-profile victims over the years, including Yamaha Motor, Xerox Business Solution, Scotland’s NHS, McLaren Health Care, the Texas State Bar, Ahold Delhaize, the Panama Ministry of Economy, the Pennsylvania AG Office, and Crisis24.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
