Pwn2Own Automotive 2026 has ended with security researchers earning $1,047,000 after exploiting 76 zero-day vulnerabilities between January 21 and January 23.
The Pwn2Own Automotive hacking competition focuses on automotive technologies and took place this week in Tokyo, Japan, during the Automotive World auto conference.
Throughout the contest, the hackers targeted fully patched in-vehicle infotainment (IVI) systems, electric vehicle (EV) chargers, and car operating systems (e.g., Automotive Grade Linux).

Before TrendMicro’s Zero Day Initiative publicly discloses them, vendors have 90 days to develop and release security fixes for zero-days that were exploited and reported during the Pwn2Own contest.
Team Fuzzware.io won the Pwn2Own Automotive 2026 contest after taking home $215,000 in cash, followed by Team DDOS with $100,750 and Synactiv with $85,000.
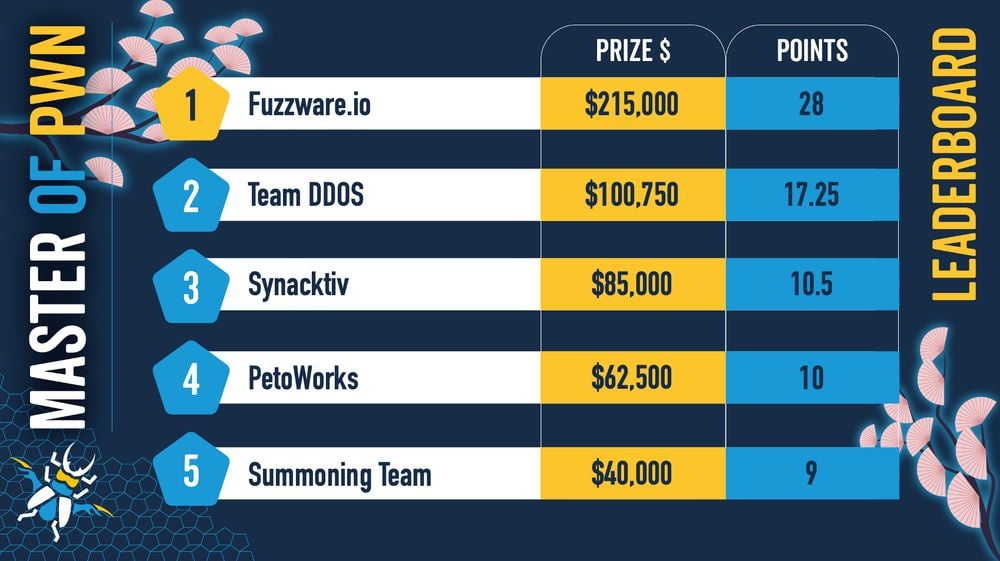
In total, Fuzzware.io earned $118,00 after hacking an Alpitronic HYC50 Charging Station, an Autel charger, and a Kenwood DNR1007XR navigation receiver on the first day.
They were also awarded another $95,000 for demonstrating multiple zero-days in the Phoenix Contact CHARX SEC-3150 charging controller, the ChargePoint Home Flex EV charger, and the Grizzl-E Smart 40A EV charging station on the second day, and an additional $2,500 after a bug collision while attempting to root an Alpine iLX-F511 multimedia receiver on the last day of the contest.
Synacktiv Team also collected $35,000 after chaining an out‑of‑bounds write flaw and an information leak to hack the Tesla Infotainment System via a USB-based attack on the first day of Pwn2Own.
The full schedule for the third day and the results for each challenge are available here, while the complete schedule for Pwn2Own Automotive 2026 is available here.
During the Pwn2Own Automotive 2024 contest, hackers collected another $1,323,750 after demoing 49 zero-day bugs and hacking a Tesla car twice. Last year, security researchers earned another $886,250 after exploiting 49 zero-days at Pwn2Own Automotive 2025.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
