An exposed command-and-control server hosting a complete deployment of the BYOB (Build Your Own Botnet) framework, a sophisticated post-exploitation tool targeting Windows, Linux, and macOS systems.
The discovery, made through Hunt.io’s AttackCapture tooling, reveals an active campaign that has operated for approximately ten months with multi-platform remote access capabilities and integrated cryptocurrency mining operations.
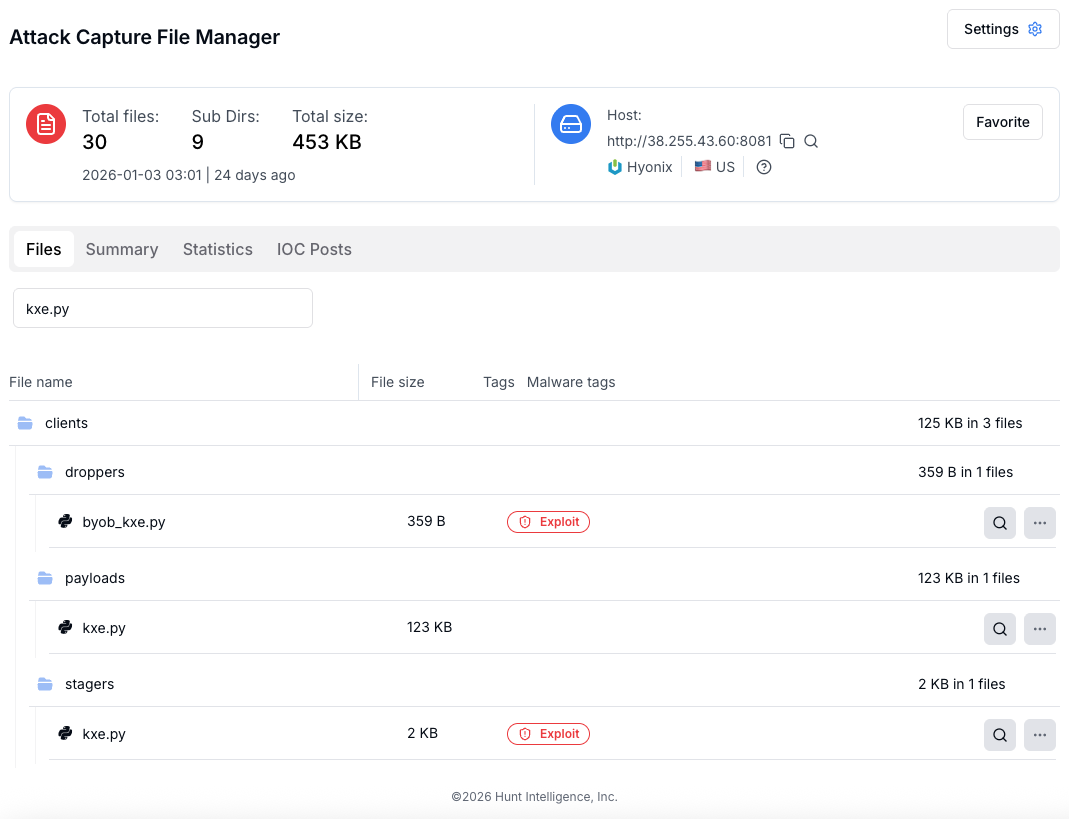
The exposed open directory was discovered on IP address 38[.]255[.]43[.]60 port 8081, a server hosted by Hyonix in Los Angeles.
Analysis revealed the server actively distributed malicious payloads, including droppers, stagers, and full remote access trojans designed to compromise multiple operating systems.
The infrastructure consists of five C2 nodes spanning the United States, Singapore, and Panama, with documented activity dating back to March 2024.
BYOB Framework
Investigation of the infrastructure uncovered an unusual dual-purpose operation. Two of the five command and control servers hosted both BYOB framework components and XMRig cryptocurrency mining software, indicating the threat actors combined remote access capabilities with passive revenue generation through cryptojacking.
The affected dual-use nodes were located at 15[.]235[.]186[.]150 in Singapore and 108[.]230[.]121[.]11 on a US AT&T network.
The primary C2 server exhibited an atypical configuration with multiple web servers running simultaneously, including IIS 10.0 on standard HTTP/HTTPS ports, Apache 2.4.41 on port 8080, and Python SimpleHTTP on port 8081 for payload distribution.
An exposed RDP port (3389) has remained active since December 2023, suggesting dedicated attack infrastructure rather than compromised legitimate systems.
The BYOB framework employs a three-stage infection chain designed to evade detection while establishing persistent remote access.
Stage one consists of a compact 359-byte Python dropper that uses multiple obfuscation layers including Base64 encoding, Zlib compression, and Marshal serialization.
This dropper fetches a 2KB stager that performs anti-virtualization checks by scanning for VirtualBox, VMware, and Hyper-V indicators in environment variables and running processes.
Multi-Stage Infection
After passing security checks, the stager retrieves the final 123KB payload containing the full remote access trojan.
The stager serves as an intermediate loader that performs critical security checks before deploying the main payload. This separation ensures the full 122KB payload is never exposed to analysis environments.
The malware disguises itself using the name “Java-Update-Manager” to appear as legitimate software and implements seven distinct persistence mechanisms across all three target platforms.
On Windows, it leverages Registry Run Keys and Startup folder shortcuts. Linux systems are compromised through crontab entries, while macOS devices are infected via LaunchAgent plist files.
The exposed framework includes extensive post-exploitation modules providing keylogging with window context tracking, screenshot capture, Outlook email harvesting through COM automation, raw packet sniffing for network traffic interception, and process manipulation capabilities.
The malware can terminate security software, bypass Windows User Account Control prompts, and maintain encrypted HTTP-based command and control communications.
Analysis of captured payloads confirms the framework performs comprehensive system reconnaissance including public IP discovery through api[.]ipify[.]org, geolocation queries to ipinfo[.]io, and collection of hostname, username, MAC address, and privilege level information.
These capabilities enable threat actors to profile victims and determine valuable targets for further exploitation or data exfiltration operations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
