The Aisuru/Kimwolf botnet launched a new massive distributed denial of service (DDoS) attack that peaked at 31.4 Tbps and 200 million requests per second, setting a new record.
The attack was part of a campaign targeting multiple companies, most of them in the telecommunications sector, and was detected and mitigated by Cloudflare last year on December 19.
Aisuru is responsible for the previous DDoS record that reached 29.7 Tbps. Another attack that Microsoft attributed to the botnet peaked at 15.72 Tbps and originated from 500,000 IP addresses.

Due to its timing, Cloudflare named the latest Aisuru campaign “The Night Before Christmas” and characterized it as an “unprecedented bombardment” on telecommunications service providers and IT organizations.
“The campaign targeted Cloudflare customers as well as Cloudflare’s dashboard and infrastructure with hyper-volumetric HTTP DDoS attacks exceeding rates of 200 million requests per second (rps) alongside Layer 4 DDoS attacks peaking at 31.4 Terabits per second, making it the largest attack ever disclosed publicly,” Cloudflare says in a report today.
More than half of the attacks in the Aisuru DDoS campaign lasted between one and two minutes, with just 6% taking longer. Most of them (90%) peaked between 1-5 Tbps, and roughly 94% were in the range of 1-5 billion packets per second.
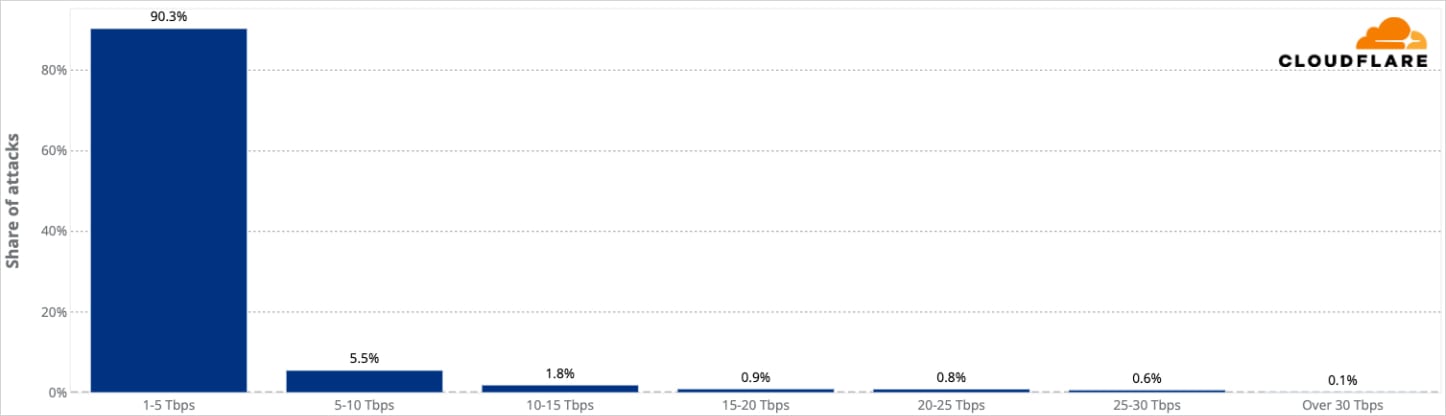
Source: Cloudflare
Despite the scale of these hyper-volumetric attacks, Cloudflare says they were detected and mitigated automatically and didn’t trigger any internal alerts.
Aisuru botnet’s power comes from compromised IoT devices and routers. However, the attack sources in “The Night Before Christmas” campaing were Android TVs, Cloudflare says in the report.
In its 2025 Q4 DDoS Threat Report, Cloudflare provides a retrospective of events throughout the year, confirming that the period recorded a 121% increase in DDoS attacks compared to 2024, with 47.1 million incidents.
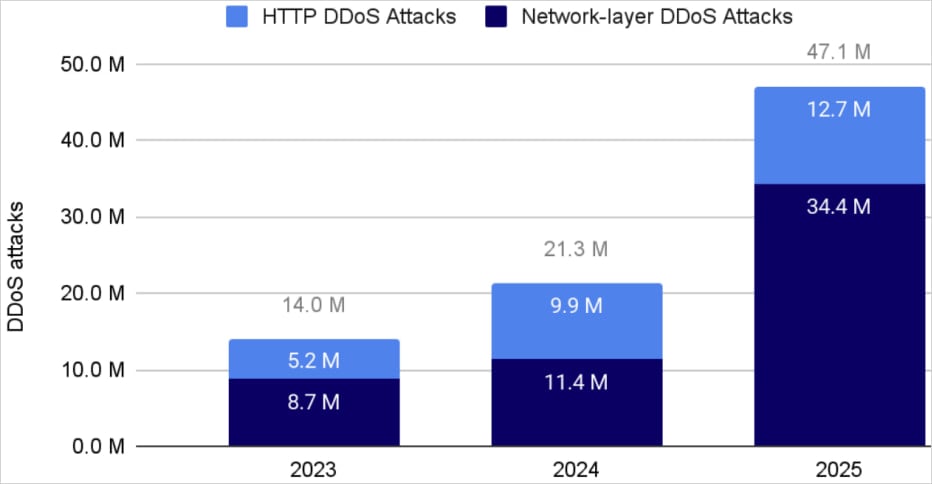
Source: Cloudflare
Cloudflare mitigated an average of 5,376 DDoS attacks per hour in 2025, with the 73% of those being network-layer attacks, and the rest being HTTP-based.
Q4 was up 31% quarter-over-quarter and 58% year-over-year, indicating that the trend of increasing numbers of DDoS attacks continues.
During this quarter, the most targeted industries were telecommunication service providers, IT and services firms, gambling and casinos, and gaming companies.
The largest source of the attacks was Bangladesh, followed by Ecuador and Indonesia. Cloudflare also noted Argentina jumping to the fourth place while Russia dropped five posts to number 10.
According to the report, DDoS attacks last year targeted mostly organizations in China, Hong Kong, Germany, Brazil, and the United States.
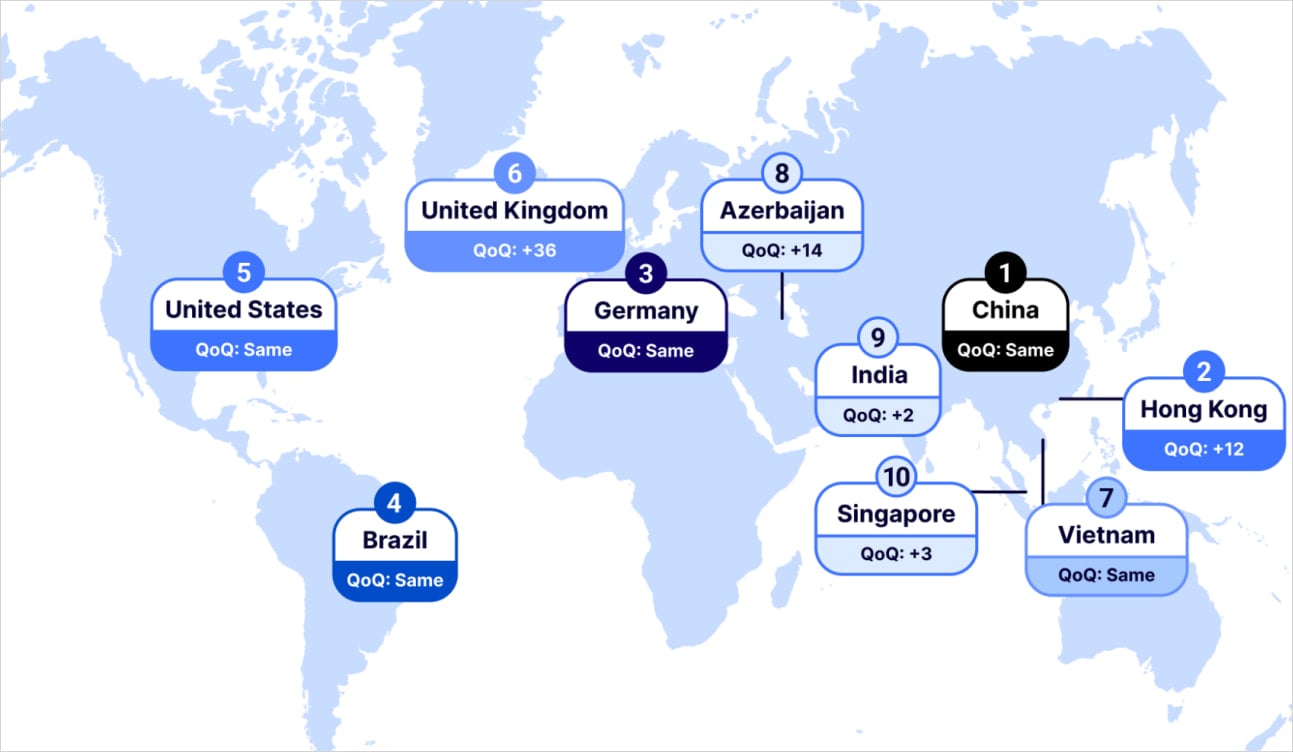
Source: Cloudflare
Cloudflare’s report highlights a 600% increase in network-layer attacks exceeding 100 Mpps and a 65% QoQ increase in attacks larger than 1 Tbps. The internet firm also notes that more than 71.5% of all recorded HTTP DDoS attacks come from known/documented botnets.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
