Marquis Software Solutions, a Texas-based financial services provider, is blaming a ransomware attack that impacted its systems and affected dozens of U.S. banks and credit unions in August 2025 on a security breach reported by SonicWall a month later.
The software company provides data analytics, compliance reporting, CRM tools, and digital marketing services to more than 700 banks, credit unions, and mortgage lenders across the United States.
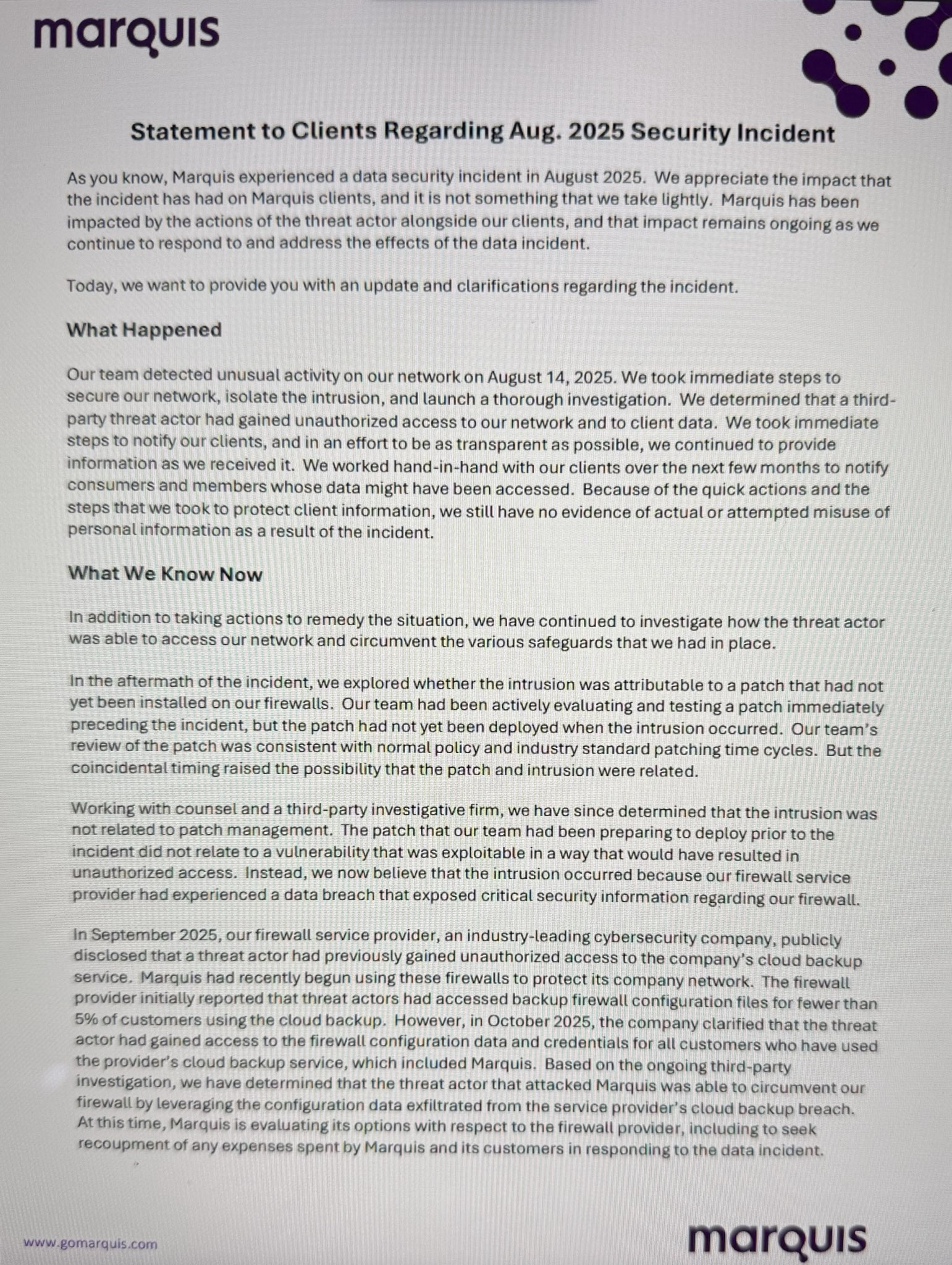
In statements to customers earlier this week seen by BleepingComputer, Marquis says the ransomware operators didn’t breach its systems by exploiting an unpatched SonicWall firewall, as previously believed.

Instead, the attackers used information obtained from firewall configuration backup files stolen after gaining unauthorized access to SonicWall’s MySonicWall online customer portal.
“Based on the ongoing third-party investigation, we have determined that the threat actor that attacked Marquis was able to circumvent our firewall by leveraging the configuration data extracted from the service provider’s cloud backup breach,” Marquis said.
“At this time, Marquis is evaluating its options with respect to the firewall provider, including to seek recoupment of any expenses spent by Marquis and its customers in responding to the data incident.”
SonicWall disclosed the security breach mentioned by Marquis on September 17, when it warned customers to reset their MySonicWall account credentials and said the incident affected only about 5% of its firewall customers using its cloud backup service.
The company also warned that threat actors could extract access credentials and tokens, making it “significantly easier” to compromise affected customers’ firewalls. However, roughly three weeks later, SonicWall issued an update confirming that all customers using its cloud backup service were affected by the September breach.
One month later, it published another update stating that a Mandiant investigation into the September attack found evidence linking the incident to state-sponsored hackers.
SonicWall added that the MySonicWall breach was unrelated to attacks by the Akira ransomware gang that targeted MFA-protected SonicWall VPN accounts in late September.
Cybersecurity company Huntress reported on October 13 that it had observed threat actors compromising over 100 SonicWall SSLVPN accounts in a large-scale campaign using stolen, valid credentials. However, Huntress found no evidence linking these attacks to the SonicWall cloud backup hack, and SonicWall did not respond to BleepingComputer’s requests for comment at the time.
BleepingComputer reached out again earlier this week, but a SonicWall spokesperson has yet to reply.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
