A vulnerability affecting the Mitsubishi Electric Iconics Suite, a widely deployed supervisory control and data acquisition (SCADA) system used across industrial sectors, including automotive, energy, and manufacturing.
The flaw, tracked as CVE-2025-0921, carries a CVSS score of 6.5 (Medium severity) and enables attackers to trigger denial-of-service (DoS) conditions on affected systems, compromising operational availability.
Vulnerability Overview
| CVE Identifier | Vulnerability Description | CVSS Score |
|---|---|---|
| CVE-2025-0921 | Execution with unnecessary privileges vulnerability in multiple services of Mitsubishi Electric Iconics Digital Solutions GENESIS64 | 6.5 – Medium |
According to Paloalto Network, the vulnerability stems from privileged file system operations within the Iconics Suite’s AlarmWorX64 MMX Pager Agent component.
When exploited, attackers with local non-administrative access can manipulate critical system binaries, leading to system corruption and rendering industrial control systems inoperable.
The flaw affects Microsoft Windows versions 10.97.2 and earlier of the Iconics Suite.
CVE-2025-0921 allows threat actors to misuse privileged file system operations by manipulating the SMSLogFile configuration path stored in the IcoSetup64.ini file.
Attackers can create symbolic links redirecting logging operations to critical Windows drivers such as cng.sys, which provides cryptographic services essential for system boot processes.
The exploitation becomes particularly effective when combined with CVE-2024-7587, a separate vulnerability in the GenBroker32 installer that grants excessive file permissions to the C:ProgramDataICONICS directory.
This permission misconfiguration allows any local user to modify configuration files that should be restricted to administrators.
Attack Methodology
In a proof-of-concept demonstration, researchers showed how an attacker with non-privileged access could redirect SMS logging operations to overwrite the cng.sys driver.
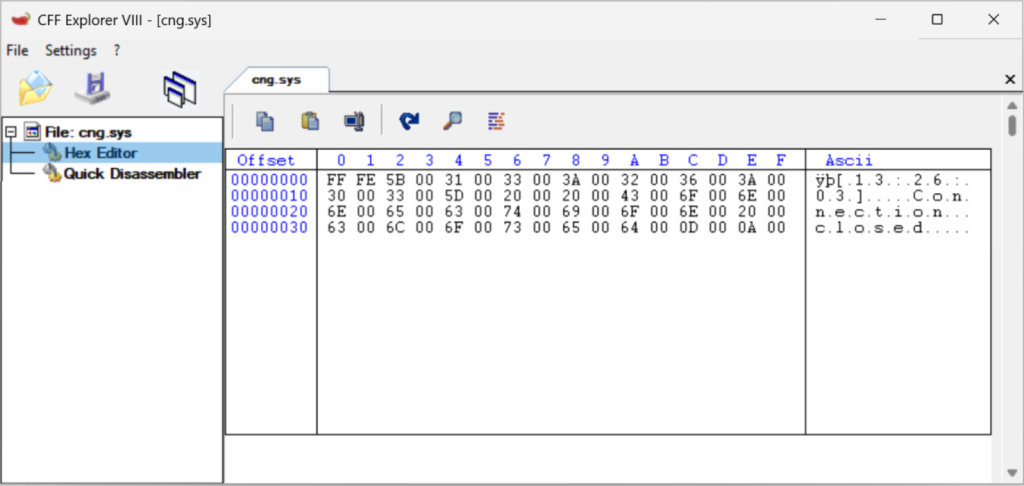
By creating a symbolic link from the configured SMSLogFile path to C:WindowsSystem32cng.sys, subsequent SMS alert operations corrupt the driver file with log data instead of valid binary code.
Upon system reboot, Windows attempts to load the corrupted driver, resulting in boot failure and an endless repair loop.
This creates a persistent DoS condition on critical operational technology (OT) engineering workstations, potentially disrupting industrial monitoring and control operations.

Mitsubishi Electric has released a security advisory detailing remediation measures for CVE-2025-0921.
System administrators should immediately apply the recommended workarounds, which address all vulnerabilities identified in the Iconics Suite assessment.
Industrial organizations operating Iconics Suite versions 10.97.2 and earlier should prioritize patching and implement the vendor-recommended security controls to prevent potential service disruptions.
The vulnerability highlights the critical importance of proper access controls and privilege management in industrial control system environments where availability is paramount.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
