A complex espionage campaign attributed to Chinese APT group Lotus Blossom, active since 2009.
The investigation uncovered a sophisticated compromise of Notepad++ distribution infrastructure that delivered Chrysalis, a previously undocumented custom backdoor with extensive remote access capabilities.
The attack chain began at IP address 95.179.213.0, where execution of notepad++.exe and GUP.exe preceded download of a malicious update.exe file.
This NSIS installer deployed a renamed Bitdefender Submission Wizard executable to the hidden %AppData%Bluetooth directory for DLL sideloading.
When executed, it loaded a malicious log.dll that decrypted the Chrysalis backdoor using custom algorithms combining linear congruential generators, FNV-1a hashing, and MurmurHash finalization.
The Chrysalis backdoor reveals itself as a feature-rich implant implementing 15 distinct command capabilities.
Configuration data encrypted with RC4 key “qwhvb^435h&*7” disclosed the C2 URL https://api.skycloudcenter.com/a/chat/s/70521ddf-a2ef-4adf-9cf0-6d8e24aaa821, which deliberately mimics Deepseek API formatting to blend with legitimate traffic.
The URL resolves to Malaysian IP address 61.4.102.97. The backdoor communicates using user agent “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.4044.92 Safari/537.36” to appear as standard browser traffic.
Command capabilities include spawning interactive reverse shells (4T), remote process execution (4V), file read/write operations (4Y, 4W, 4X), complete file transfer protocols (4c, 4d), self-removal functionality (4), and drive enumeration (4_).
A mutex “GlobalJdhfv_1.0.1” prevents multiple instances. Persistence is established through Windows service creation or registry modifications.
Chrysalis implements two sophisticated API hashing routines using FNV-1a with constant 0x811C9DC5 and MurmurHash finalization (0x85EBCA6B).
String obfuscation uses position-dependent character transformation combining bit rotations and XOR operations.
The main module uses hardcoded XOR key “gQ2JR&9;” applied five times through XOR, addition, and subtraction operations.
Investigators discovered ConsoleApplication2.exe, a loader exploiting Microsoft’s undocumented Warbird code protection framework.
The loader invokes NtQuerySystemInformation with SystemCodeFlowTransition parameter (0xB9) to execute embedded Metasploit block_api shellcode within Microsoft-signed binary memory.
This technique downloads Cobalt Strike beacons from api.wiresguard.com/users/system.
Forensic analysis uncovered a renamed Tiny-C-Compiler executing malicious C source code from conf.c.
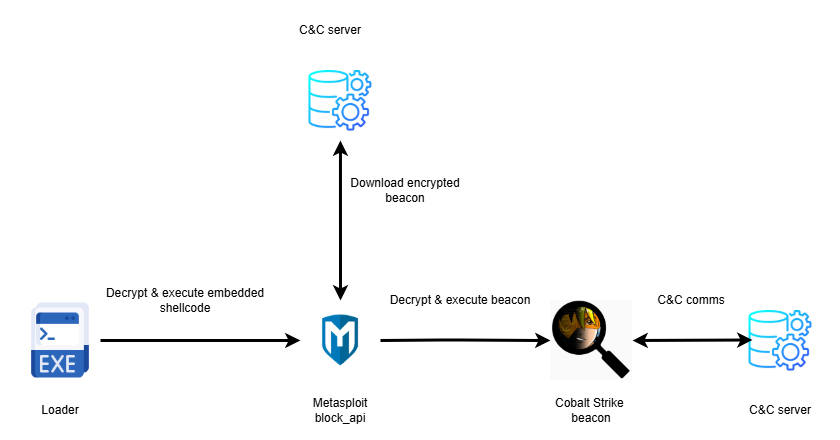
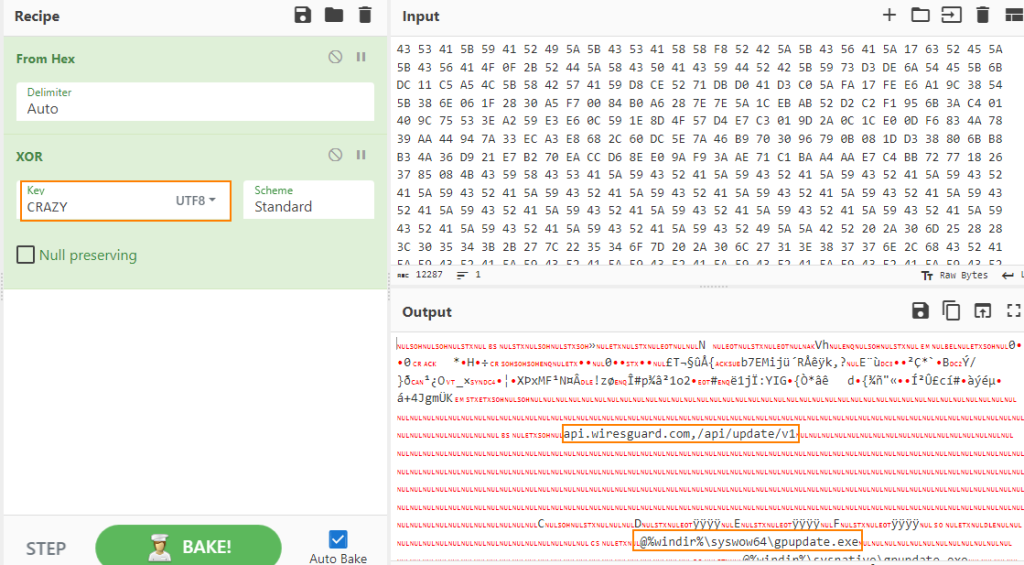
The shellcode employs rolling XOR decryption before transferring execution to Cobalt Strike HTTPS beacon using http-get endpoint api.wiresguard.com/update/v1 and http-post endpoint api.wiresguard.com/api/FileUpload/submit.
According to Rapid7, threat intelligence pivoting identified four additional loader variants sharing identical Cobalt Strike configurations and the same public key, indicating coordinated campaign activity.
Attribution to Lotus Blossom is based on similarities with Symantec research, particularly the Bitdefender Submission Wizard DLL sideloading technique and shared infrastructure indicators.
The Chrysalis campaign demonstrates significant evolution in tradecraft, combining custom malware with commodity frameworks and rapid operationalization of public security research.
Organizations should monitor for hidden %AppData% directories containing executables, NtQuerySystemInformation abuse patterns, and suspicious Deepseek-style API traffic to detect potential compromise.
Indicators of compromise (IoCs)
| update.exe | a511be5164dc1122fb5a7daa3eef9467e43d8458425b15a640235796006590c9 |
| [NSIS.nsi] | 8ea8b83645fba6e23d48075a0d3fc73ad2ba515b4536710cda4f1f232718f53e |
| BluetoothService.exe | 2da00de67720f5f13b17e9d985fe70f10f153da60c9ab1086fe58f069a156924 |
| BluetoothService | 77bfea78def679aa1117f569a35e8fd1542df21f7e00e27f192c907e61d63a2e |
| log.dll | 3bdc4c0637591533f1d4198a72a33426c01f69bd2e15ceee547866f65e26b7ad |
| u.bat | 9276594e73cda1c69b7d265b3f08dc8fa84bf2d6599086b9acc0bb3745146600 |
| conf.c | f4d829739f2d6ba7e3ede83dad428a0ced1a703ec582fc73a4eee3df3704629a |
| libtcc.dll | 4a52570eeaf9d27722377865df312e295a7a23c3b6eb991944c2ecd707cc9906 |
| admin | 831e1ea13a1bd405f5bda2b9d8f2265f7b1db6c668dd2165ccc8a9c4c15ea7dd |
| loader1 | 0a9b8df968df41920b6ff07785cbfebe8bda29e6b512c94a3b2a83d10014d2fd |
| uffhxpSy | 4c2ea8193f4a5db63b897a2d3ce127cc5d89687f380b97a1d91e0c8db542e4f8 |
| loader2 | e7cd605568c38bd6e0aba31045e1633205d0598c607a855e2e1bca4cca1c6eda |
| 3yzr31vk | 078a9e5c6c787e5532a7e728720cbafee9021bfec4a30e3c2be110748d7c43c5 |
| ConsoleApplication2.exe | b4169a831292e245ebdffedd5820584d73b129411546e7d3eccf4663d5fc5be3 |
| system | 7add554a98d3a99b319f2127688356c1283ed073a084805f14e33b4f6a6126fd |
| s047t5g.exe | fcc2765305bcd213b7558025b2039df2265c3e0b6401e4833123c461df2de51a |
Network indicators
| 95.179.213.0 |
| api[.]skycloudcenter[.]com |
| api[.]wiresguard[.]com |
| 61.4.102.97 |
| 59.110.7.32 |
| 124.222.137.114 |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
