Active Directory serves as the central repository for an organization’s authentication infrastructure, making it a prime target for sophisticated threat actors.
The NTDS.dit database, which stores encrypted password hashes and critical domain configuration data, is the crown jewel of enterprise security.
Successful acquisition of this file can lead to complete organizational compromise, enabling attackers to assume any identity within the domain without requiring social engineering or traditional login attacks.
Within Windows domain infrastructures, Active Directory functions as the authentication and authorization backbone, controlling access rights and trust relationships across the organization.
The NTDS.dit file (NT Directory Services Directory Information Tree) sits at the heart of this system, located by default in C:WindowsNTDS on every domain controller.
This database file holds the domain’s complete repository, including:
- User credentials and password hashes for every domain account.
- Domain Administrator and high-privilege account credentials.
- Group membership information and policy configurations.
- System records and trust relationships.
For threat actors, obtaining the NTDS.The dit file provides complete visibility into the organization’s identity infrastructure.
Combined with the SYSTEM registry hive needed for decryption, adversaries can recover these hashes, perform offline password cracking, and assume any identity. This direct credential theft eliminates the need for complex attack vectors, providing unrestricted access to the entire network infrastructure.
Attack Methodology and Execution
The attack methodology proves remarkably covert and leverages legitimate administrative tools to evade detection.
Analysis from the Trellix Advanced Research Center notes security professionals, SOC teams, and infrastructure defenders with practical insights into identity-focused attacks
After achieving administrative control with system-level privileges, adversaries typically follow a multi-stage approach to extract and exfiltrate the NTDS.dit file.
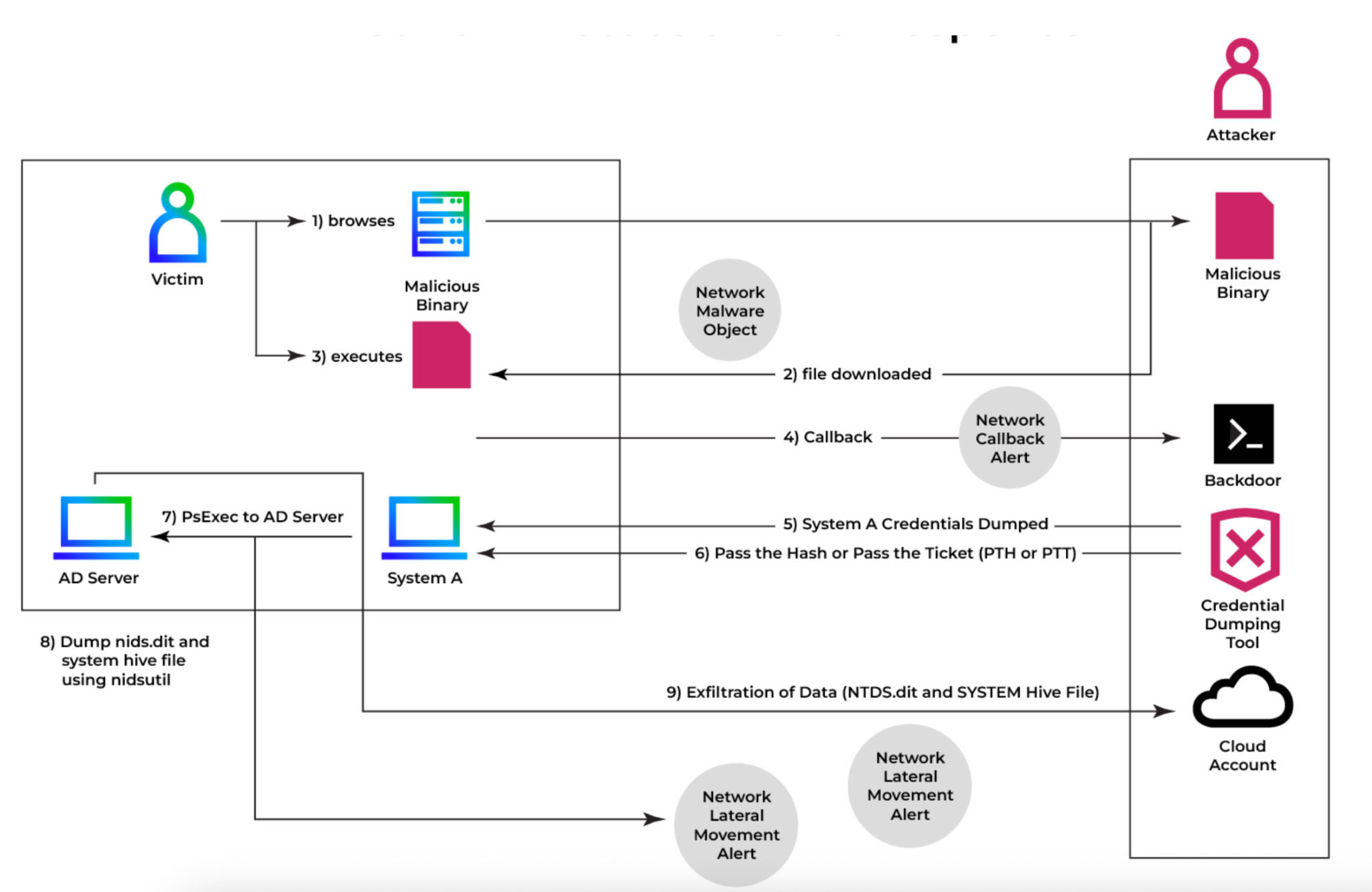
Attackers commonly leverage built-in utilities like vssadmin to generate Volume Shadow Copies, effectively circumventing file locking mechanisms that protect the NTDS.dit file during normal domain controller operations.
Tools like SecretsDump from the Impacket framework, Mimikatz, or DSInternals PowerShell modules process the extracted database to decrypt password hashes.
The Volume Shadow Copy Service allows creation of backup snapshots while the system remains operational, giving attackers access to locked files without triggering immediate alarms.
The NTDS.dit file is then retrieved using various methods including ntdsutil.exe, esentutl, or direct copy commands from the shadow volume.
Many advanced persistent threat (APT) groups including APT28, APT41, and FIN6 have demonstrated sophisticated capabilities in executing these attacks.
The severity stems not from simple data compromise, but from wholesale infrastructure identity theft. Trellix Helix addresses this challenge through cross-platform correlation of endpoint, network, and cloud telemetry, revealing the complete attack sequence that individual security solutions cannot detect.
When Trellix Helix detects NTDS.dit exfiltration, it generates a CRITICAL severity alert titled “Credential Theft: Exfiltration Of Active Directory Database (NTDS.dit)”.
The detection mechanism correlates endpoint telemetry with network behavior and policy events to identify suspicious activities across multiple attack stages.
The platform observes remote PsExec sessions being leveraged to extract the Active Directory database file, a technique attackers commonly use to obtain password hashes for every account in the domain.
The platform’s correlation engine pieces together concerning patterns from multiple security signals including suspicious outgoing HTTP traffic from workstations using Domain Admin accounts, PsExec remote administration tool usage, unusual registry tool activity on Domain Controllers, lateral movement alerts, and suspicious SMB file-sharing traffic on port 445.
Each detection point is enriched with MITRE ATT&CK context, specifically mapping to technique T1003.003 (OS Credential Dumping: NTDS), showing which tactics align with known adversary behaviors
Recommended Response Actions
Based on comprehensive threat analysis, organizations should immediately implement multi-layered defenses when NTDS.dit theft is detected
Immediate containment:
- Isolate affected systems from the network to prevent lateral movement.
- Disable compromised user accounts, particularly Domain Administrator accounts.
- Block outbound connections from affected hosts to prevent exfiltration.
Credential reset and rotation:
- Reset passwords for all privileged accounts immediately.
- Reset the KRBTGT account password twice with appropriate waiting periods to invalidate Kerberos tickets.
- Enable multi-factor authentication (MFA) for all administrative accounts.
System hardening:
- Restrict admin shares and disable unnecessary SMB access.
- Implement application whitelisting to prevent unauthorized tool execution.
- Deploy Credential Guard on Windows systems.
- Monitor and restrict Volume Shadow Copy operations.
Detection enhancement:
- Deploy Trellix Endpoint Security and Network Security across critical assets.
- Configure automated response playbooks for credential theft scenarios.
- Establish baseline behavior profiles for administrative tools.
The theft of the NTDS.dit file represents more than just a data breach it signifies complete loss of identity, trust, and control within a Windows domain.
Traditional defenses operating in isolation frequently miss warning signs when attackers use native tools and low-noise techniques.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
