Indian users’ trust in government services through a sophisticated Android malware campaign that impersonates Regional Transport Office (RTO) challan notifications.
This campaign represents an evolution from previous RTO-themed malware, featuring advanced anti-analysis techniques, a modular three-stage architecture, and a structured backend infrastructure for data collection and remote operations.
The malware spreads through social engineering tactics, with attackers sending fake RTO challan notifications via WhatsApp messages.
Researchers at Seqrite Labs discovered this active threat, which distributes malicious applications outside the Google Play Store primarily through WhatsApp and messaging platforms.
These messages create urgency by claiming users have pending traffic violations that require immediate attention. When users click the provided links, they download malicious APK files from external sources, bypassing Google Play Store’s security protections.
Three-Stage Infection Process
Stage 1: Dropper and Cryptominer
The initial application acts as a dropper, decrypting and installing subsequent malware stages.
It simultaneously runs a cryptocurrency mining module that activates when the device screen locks, reducing user suspicion. Once Stage 2 installs successfully, the mining activity terminates and control is transferred to the next component.
Stage 2: Persistence and Backend Initialization
This stage establishes long-term persistence by registering multiple broadcast receivers, hiding the launcher icon, and maintaining continuous background execution.
It initializes connectivity with Google Firebase backend infrastructure for victim data storage, remote configuration, and command-and-control communication.
Stage 2 also runs independent cryptomining operations, serving as both a control layer and monetization component.
Stage 3: Data Theft and Surveillance
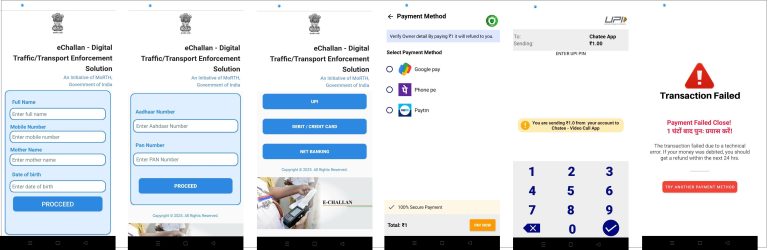
The final stage presents a fraudulent user interface mimicking official government portals with authentic RTO branding.
Users are prompted to verify their identity or clear pending challans. To proceed, victims must grant high-risk permissions including SMS access, call logs, notification listener, and storage access.
Once granted, the malware harvests personal identity information, banking notifications, OTP messages, transaction alerts, and device metadata. All collected data is transmitted to attacker-controlled servers in structured JSON format.
Seqrite researchers gained access to the backend infrastructure, revealing the campaign’s true scale and sophistication.
The backend stored highly sensitive information including full names, phone numbers, Aadhaar numbers, PAN numbers, UPI PINs, credit card details, and net banking credentials.
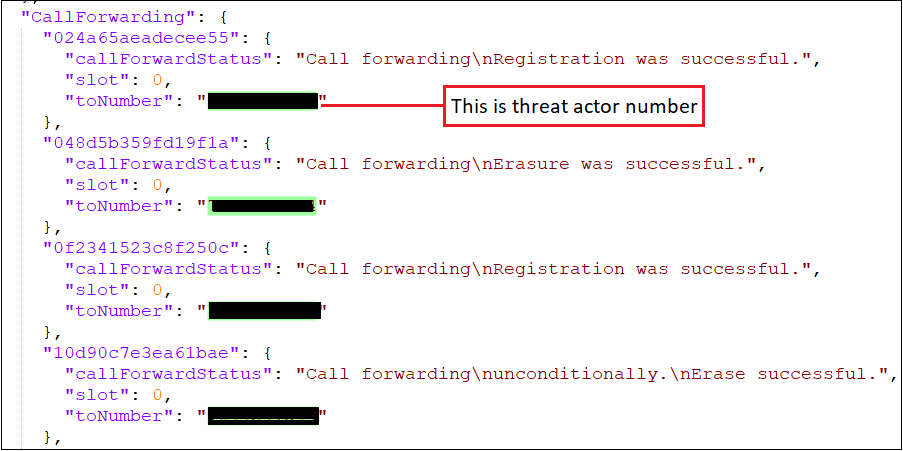
Beyond data storage, the backend functions as an active command-and-control system enabling remote configuration of SMS forwarding numbers, tracking device activity, and centralized monitoring of infected devices.
This infrastructure allowed operators to manage stolen data, monitor campaign performance, and remotely control malware behavior.
Infection Scale and Impact
Beyond acting as a data repository, the backend infrastructure was actively used as a command-and-control (C2) system.
Approximately 7,400 devices were infected according to backend records. While not all victims provided complete permissions, a significant number granted SMS access and submitted highly sensitive personal and financial information, leading to large-scale financial fraud and identity theft.
Users should install trusted mobile security solutions like Quick Heal Mobile Security for Android malware, which detects these threats as variants of Android.Dropper.A.
Compared to earlier RTO malware variants, this campaign shows significant improvements: three-stage modular architecture versus single-stage APK file, dynamic remote configuration replacing hardcoded logic, extensive anti-analysis techniques, full surveillance toolkit, and dual monetization through fraud and mining.
The malware enables several high-risk scenarios including real-time OTP interception for financial fraud, bank account takeover, SIM swap facilitation, loan and credit fraud using stolen identity documents, and WhatsApp or social media account hijacking.
Never download applications from unofficial sources, verify government notifications through official channels, and carefully review permission requests before granting access to sensitive device functions.
This campaign demonstrates a highly organized threat group focused on long-term exploitation, combining social engineering, cloud-based infrastructure, and real-time financial surveillance to target Indian mobile users.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
