Threat actors have employed a new technique to distribute malicious code named “EtherHiding,” which abuses Binance’s Smart Chain (BSC) contracts to host parts of a malicious code chain to hide them inside the blockchain.
To inject malicious JavaScript codes into the blockchain systems, threat actors used compromised WordPress sites redirected to Cloudflare Worker hosts to achieve evasive distribution.
“In the attack flow, a site is defaced with a very believable overlay demanding a browser update before the site can be accessed. The fake “update” turns out to be vicious infostealer malware like RedLine, Amadey, or Lumma.”, reads the post by Guardio Labs.
API security isn’t just a priority; it’s the lifeline of businesses and organizations. Yet, this interconnectivity brings with it an array of vulnerabilities that are often concealed beneath the surface.
EtherHiding Malware
This new technique has also been termed “ClearFake,” which distributes malicious codes through compromised websites by displaying fake browser update overlays.
According to the reports shared with Cyber Security News, it was confirmed that threat actors have been targeting vulnerable WordPress websites to inject two malicious scripts into the web pages.
These malicious scripts load the Binance Smart Chain (BSC) JS library, which fetches other malicious scripts from the blockchain that are injected into the site. Moreover, this code also triggers the download of the third-stage payload from the attacker-controlled server (C2).
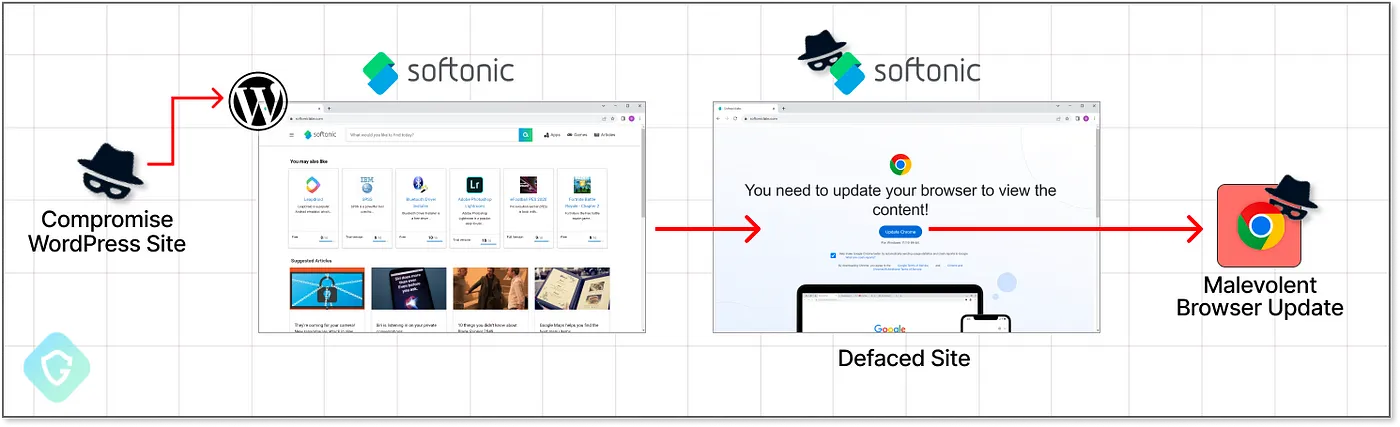
The fake browser update overlays are prompted for Google Chrome, Microsoft Edge, or Mozilla Firefox browser users. When the victims click the “update” button, they are directed to download a malicious executable from Dropbox or other legitimate websites.
Blockchain technology, while being a powerful tool, can also be exploited in various ways, such as in the spread of malware or in the exfiltration of stolen data and files. These malicious activities can be difficult to track and shut down using traditional law enforcement methods.
A complete report about ClearFake has been published by Guardio Labs, providing detailed information about the distribution technique, exploitation methods, reason for Binance usage, and other information.
Indicators of Compromises (IOCs)
| Related BSC Addresses/Contracts: ———————————– 0xfc1fE66FB63c542A3e4D45305DaB196E5EcA222A 0x7f36D9292e7c70A204faCC2d255475A861487c60 3ed Stage IP Addresses: 3rd Stage Attacker Controlled Domains: Compromised WordPress Sites (Detected Last 14 Days): Malware Hashes (samples): Malware Filename samples (Note UNICODE abuse in filenames): |
Protect yourself from vulnerabilities using Patch Manager Plus to quickly patch over 850 third-party applications. Take advantage of the free trial to ensure 100% security.
