As our daily lives become more time-pressured and interconnected, digital calendars have emerged as indispensable tools for managing personal and professional commitments.
Yet, this very convenience carries a latent risk one that can expose millions to unseen security threats.
Recent research by Bitsight TRACE reveals that over 390 abandoned domains linked to iCalendar synchronization requests are currently receiving sync calls from nearly 4 million devices, primarily iOS and macOS users.
These forgotten calendar domains represent a significant, overlooked attack surface that can be exploited on a large scale.
Unlike traditional phishing, where users are educated to scrutinize unexpected emails, the calendar vector relies on protocol trust and user complacency.
Whenever a user subscribes to an external calendar be it for public holidays, event reminders, or exclusive promotions their device sets up recurring sync requests to that domain.
If the domain expires or is hijacked, attackers can inject arbitrary events. These events may contain malicious links and attachments, effectively turning a trusted organizational tool into an attack vector for phishing, malware, or social engineering campaigns.
Bitsight’s research began with sinking a single domain distributing German holiday events via .ics files.
Observing over 11,000 unique IP addresses contacting this domain every day, analysts expanded the investigation, identifying an additional 347 expired domains some as prominent as those related to FIFA events and global religious calendars.
These domains collectively receive sync requests from nearly 4 million unique devices daily. Most users and enterprises are unaware that calendar apps continue to poll expired or hijacked servers in the background, making this a silent and persistent risk.
Modern Infrastructure and Monetization
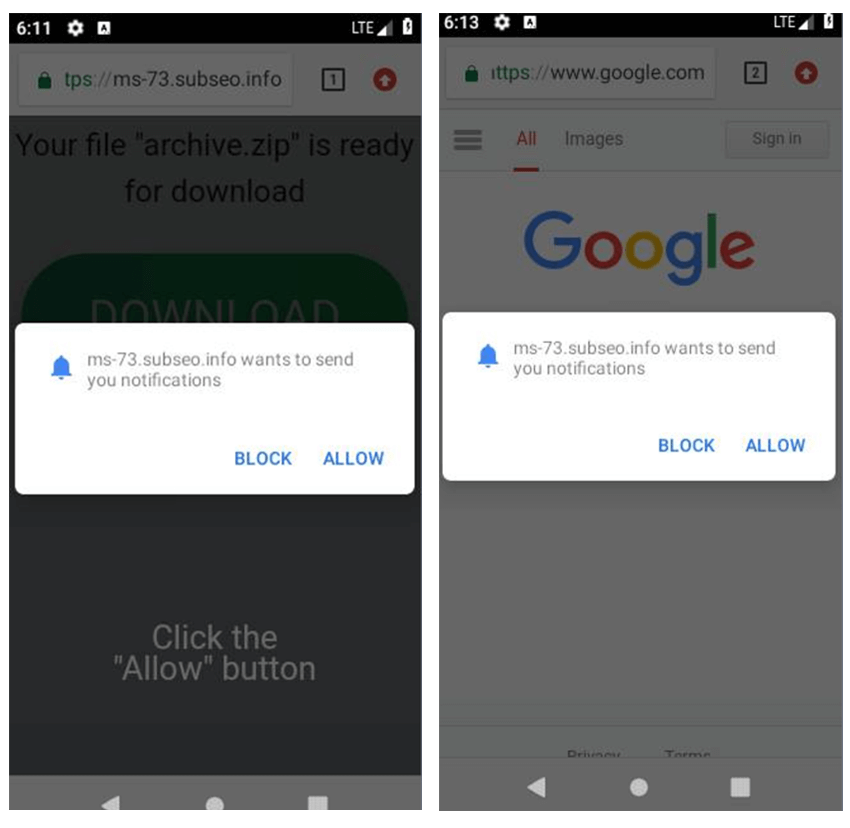
Modern attackers deploy dedicated infrastructure to trick users into subscribing often using compromised legitimate websites or redirect chains.
By making it seem like the user needs to solve a captcha by clicking “Allow” to view the original content.
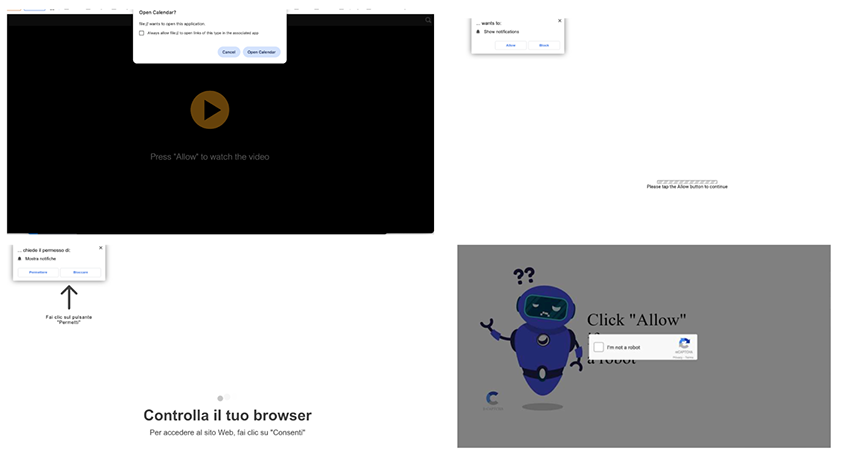
They monetize access either through classic phishing and malware distribution, or innovative means such as pushing VPN installations (which may turn devices into residential proxy nodes), or even selling push notification “ad space” through platforms like Pushground and RichAds.
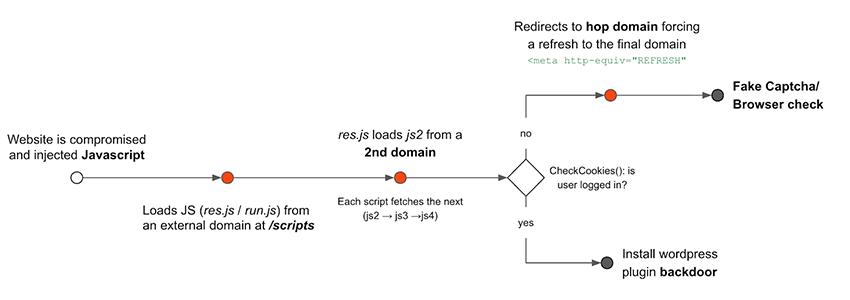
The sophistication of these networks is underscored by their scale and persistence; several domains exhibit behavioral patterns characteristic of advanced Traffic Distribution Systems and known malware campaigns like Balada Injector.
The research uncovered two significant types of sync requests to their sinkhole:
- Base64-encoded URIs.
- Webcal query parameters.
Both suggest background sync activity, meaning existing device subscriptions are vulnerable for months or years, long after the user forgets their origin.
Unlike email, calendar events enjoy inherent user trust. There is little monitoring or routine security awareness training concerning calendar-based attacks.
Once compromised, a calendar event can mimic legitimate meeting invites or reminders, even carrying the branding and formatting of familiar services or colleagues. The threat spectrum includes:
- Phishing: Stealing credentials through fake event links.
- Malware: Attaching malicious files or triggering unwanted app installations.
- Social engineering: Creating urgency with fake “system alerts” or official-seeming reminders.
Recent attacks have also leveraged advanced methods, such as deploying JavaScript via .ics files in open-source suites (e.g., Zimbra 0days), or attempting AI prompt injections targeting digital assistants like Google Gemini.
What Can Be Done?
The APKs worked similarly, they were light, a few KB and pretended to be various games, such as “Genshin Impact” or “Plant vs Zombies”.
Security researchers emphasize the need for organizational and individual vigilance:
- Audit and remove unknown calendar subscriptions.
- Treat calendar event links with the same caution as email links.
- Implement calendar subscription policies for corporate devices.
- Incorporate calendar threats into cybersecurity training programs.
- Where possible, block unknown calendar sync domains at the network perimeter.
While major providers like Apple and Google have markedly improved platform security Google’s use of proxy servers for calendar sync notably mitigates direct exploitability many open-source and third-party calendar solutions lag behind.
As adoption of digital calendars continues to grow, awareness and investment in calendar security are crucial.
Abandoned domains and silent sync requests are emerging as one of the most powerful entry points for attackers underscoring the importance of maintaining vigilance, updating protocols, and making calendar security a first-class concern in modern cyber hygiene.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
