Hundreds of malicious skills are distributed through OpenClaw’s marketplace, transforming the popular AI agent ecosystem into a new supply chain attack vector.
Threat actors are weaponizing the platform’s extensibility features to deliver droppers, backdoors, and infostealers disguised as legitimate automation tools.
OpenClaw Skills Become Malware Distribution Channel
OpenClaw is a self-hosted AI agent that executes shell commands, file operations, and network requests on users’ systems.
The platform’s functionality is extended through skills third-party packages distributed via the ClawHub marketplace.
These skills contain SKILL.md files with metadata and instructions, along with executable scripts and resources.
VirusTotal Code Insight has analyzed over 3,016 OpenClaw skills, and hundreds of them exhibit malicious characteristics.
While some contain poor security practices like hardcoded secrets and unsafe command execution, a significant portion are intentionally malicious, designed for data exfiltration, backdoor installation, and remote system control.
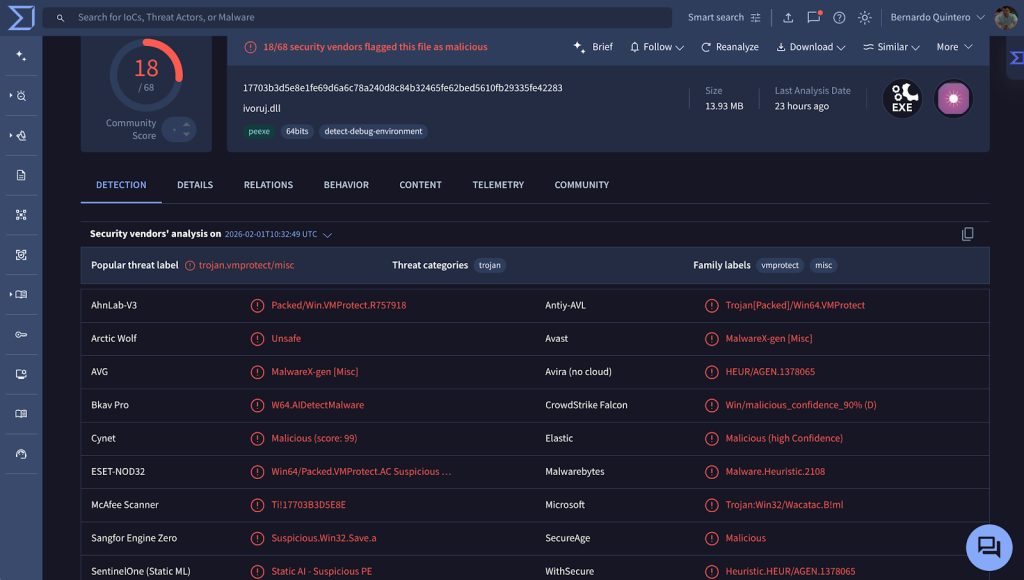
Security researchers discovered that the ClawHub user “hightower6eu” was operating as a prolific malware publisher, with 314 skills identified as malicious.
The threat actor distributes skills masquerading as crypto analytics, financial tracking, and social media tools, all of which instruct users to download and execute external code during setup.
Analysis of the “Yahoo Finance” skill revealed a sophisticated attack chain. Windows users are directed to download a password-protected ZIP file containing openclaw-agent.exe, which multiple vendors have flagged as a packed Trojan.
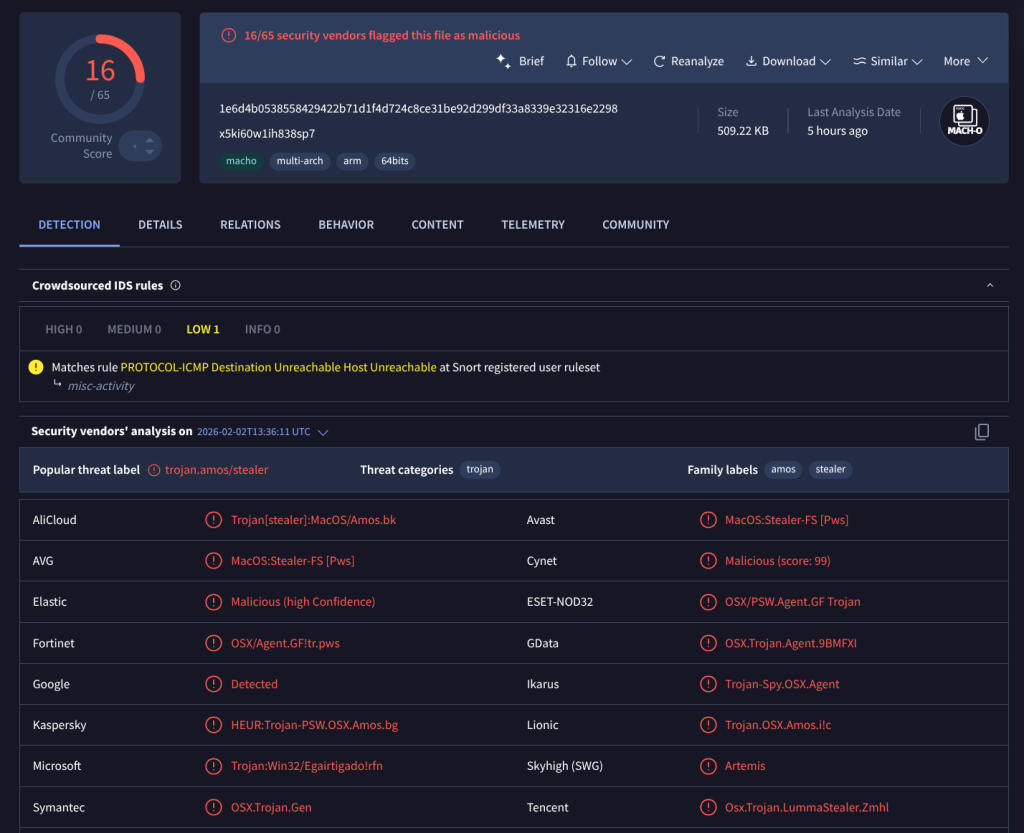
macOS users receive obfuscated Base64-encoded shell scripts that download and execute the Atomic Stealer (AMOS) malware, which harvests passwords, browser credentials, and cryptocurrency wallets.
Detection and Mitigation
VirusTotal deployed Gemini 3 Flash-powered analysis to detect malicious OpenClaw skills by examining actual behavior rather than claimed functionality.
The platform now identifies skills that download external code, access sensitive data, or contain instructions that could compromise systems.
Security experts recommend sandboxing OpenClaw executions, treating skill folders as trusted code boundaries, and scanning community skills before installation.
Marketplace operators should implement publish-time scanning to flag skills with remote execution capabilities or obfuscated scripts.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.


