A critical-severity vulnerability in the Advanced Custom Fields: Extended (ACF Extended) plugin for WordPress can be exploited remotely by unauthenticated attackers to obtain administrative permissions.
ACF Extended, currently active on 100,000 websites, is a specialized plugin that extends the capabilities of the Advanced Custom Fields (ACF) plugin with features for developers and advanced site builders.
The vulnerability, tracked as CVE-2025-14533, can be leveraged for admin privileges by abusing the plugin’s ‘Insert User / Update User’ form action, in versions of ACF Extended 0.9.2.1 and earlier.

The flaw arises from the lack of enforcement of role restrictions during form-based user creation or updates, and exploitation works even when role limitations are appropriately configured in the field settings.
“In the vulnerable version [of the plugin], there are no restrictions for form fields, so the user’s role can be set arbitrarily, even to ‘administrator’, regardless of the field settings, if there is a role field added to the form,” Wordfence explains.
“As with any privilege escalation vulnerability, this can be used for complete site compromise,” the researchers warn.
Although the outcome from exploiting the flaw is severe, Wordfence notes that the issue is only exploitable on sites that explicitly use a ‘Create User’ or ‘Update User’ form with a role field mapped.
CVE-2025-14533 was discovered by security researcher Andrea Bocchetti, who, on December 10, 2025, submitted a report to Wordfence to validate the issue and escalate it to the vendor.
Four days later, the vendor addressed the problem and released it in ACF Extended version 0.9.2.2.
Based on download stats from wordpress.org, roughly 50,000 users have downloaded the plugin since then. Assuming all downloads were for the latest version, that leaves roughly an equal number of sites exposed to attacks.
WordPress plugin enumeration activity
Although no attacks targeting CVE-2025-14533 have been observed yet, a report from threat monitoring firm GreyNoise presents large-scale WordPress plugin reconnaissance activity aimed at enumerating potentially vulnerable sites.
According to GreyNoise, from late October 2025 to mid-January 2026, nearly 1,000 IPs across 145 ASNs targeted 706 distinct WordPress plugins in over 40,000 unique enumeration events.
The most targeted plugins are Post SMTP, Loginizer, LiteSpeed Cache, SEO by Rank Math, Elementor, and Duplicator.
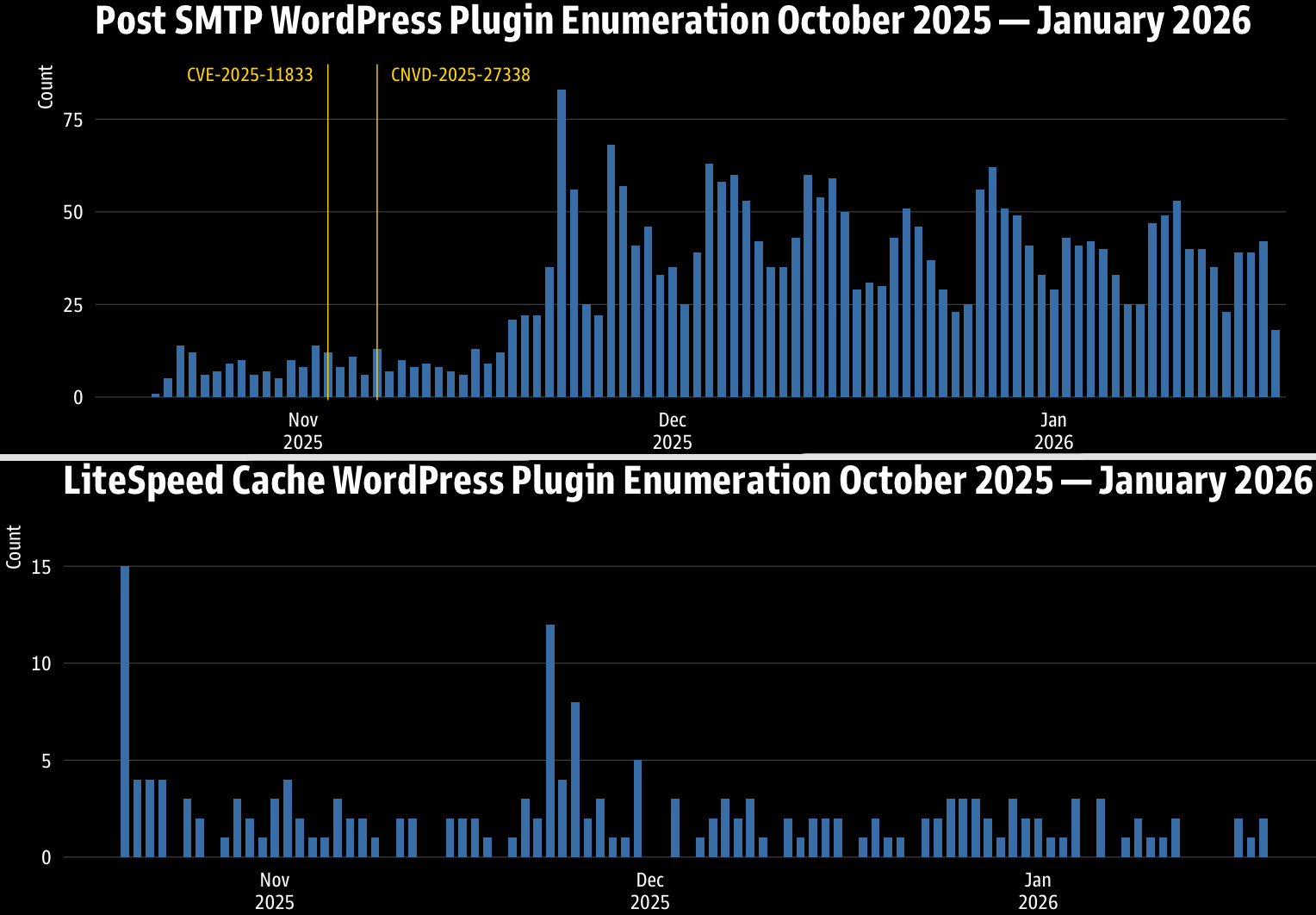
Source: GreyNoise
Active exploitation of the Post SMTP flaw CVE-2025-11833 was reported in early November 2025 by Wordfence, and GreyNoise’s records indicate a focused effort targeting this flaw involving 91 IPs.
Another flaw GreyNoise urged admins to patch is CVE-2024-28000, which impacts LiteSpeed Cache and was marked as actively exploited by Wordfence in August 2024.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
