Security researchers at The Shadowserver Foundation have identified active exploitation attempts targeting a critical zero-day vulnerability in Ivanti’s Enterprise Mobility Management (EPMM) platform.
The vulnerability, tracked as CVE-2025-4427, can be chained with CVE-2025-4428 to achieve remote code execution (RCE), posing a significant threat to unpatched systems.
Recent monitoring shows a concerning number of vulnerable instances remain exposed despite public disclosure, with attackers already attempting to exploit these security flaws.
The critical vulnerabilities affect Ivanti’s Enterprise Mobility Management platform, a solution widely used by organizations to manage mobile devices and applications across their networks.
CVE-2025-4427 serves as an initial access vector that attackers can exploit and subsequently chain with CVE-2025-4428 to achieve remote code execution on affected systems.
This dangerous combination allows attackers to potentially gain unauthorized access to sensitive corporate data, execute malicious code, or establish persistent access within compromised environments.
Security experts classify this vulnerability chain as particularly severe due to its straightforward exploitation path and the high-value nature of EPMM deployments, which typically manage critical enterprise mobile infrastructure.
Hundreds of Vulnerable Instances Remain Unpatched
The Shadowserver Foundation has implemented comprehensive scanning to identify vulnerable Ivanti EPMM instances across the internet.
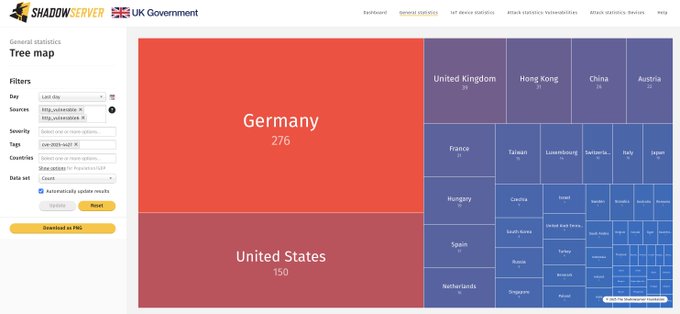
Their initial scans on May 15, 2025, discovered approximately 940 instances likely vulnerable to CVE-2025-4427.
Follow-up scans conducted on May 18, 2025, revealed a modest decrease to 798 vulnerable instances, indicating that while some organizations have applied patches, many systems remain at risk.
The geographical distribution of these vulnerable instances can be visualized through Shadowserver’s dashboard, which provides a detailed breakdown of affected systems by location.
Security researchers express concern about the relatively slow patching response, particularly given the active exploitation attempts observed in the wild.
Exploitation Monitoring Through Honeypot Sensors
The Shadowserver Foundation has deployed specialized honeypot sensors to track and analyze exploitation attempts targeting these vulnerabilities in real-time.
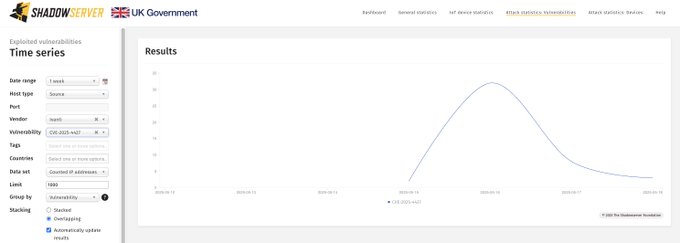
These sensors simulate vulnerable systems to attract and record attack attempts, providing valuable intelligence on exploitation techniques, attack sources, and evolving tactics.
The collected data is made publicly available through Shadowserver’s Dashboard, which displays time-series information about exploitation attempts, including source IP addresses, attack frequency, and targeting patterns.
This monitoring reveals that threat actors began attempting to exploit the vulnerabilities shortly after public disclosure, highlighting the urgent need for organizations to implement available patches or mitigations.
Security experts strongly recommend that organizations using Ivanti EPMM immediately patch their systems or implement recommended workarounds if patching isn’t immediately possible.
Additionally, organizations should conduct thorough reviews of potentially affected systems for indicators of compromise, as early exploitation attempts may have occurred before patches were applied.
The Shadowserver Foundation continues to provide updated statistics and monitoring data to help security teams and researchers track this evolving threat landscape and better protect vulnerable systems from exploitation.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
