In the past couple of weeks, we have observed an ongoing campaign targeting system administrators with fraudulent ads for popular system utilities. The malicious ads are displayed as sponsored results on Google’s search engine page and localized to North America.
Victims are tricked into downloading and running the Nitrogen malware masquerading as a PuTTY or FileZilla installer. Nitrogen is used by threat actors to gain initial access to private networks, followed by data theft and the deployment of ransomware such as BlackCat/ALPHV.
We have reported this campaign to Google but no action has been taken yet. This blog post aims to share the tactics, techniques and procedures (TTPs) as well as indicators of compromise (IOCs) so defenders can take action.
Step 1: Luring victims in via malicious ads
The initial intrusion starts from a malicious ad displayed via Google search. We have observed several different advertiser accounts which were all reported to Google. The lures are utilities commonly used by IT admins such as PuTTY and FileZilla.
Online ads from search engine result pages are increasingly being used to deliver malware to corporate users. ThreatDown users that have DNS Filtering can enable ad blocking in their console to prevent such malvertising attacks:
Step 2: Directing users to lookalike sites
The malvertising infrastructure deployed by Nitrogen threat actors uses a cloaking page that can either redirect to a decoy site or the infamous Rick Astley video. The redirect to a decoy page can be activated if the campaign is not weaponized yet or if the malicious server detects invalid traffic (bot, crawler, etc.).
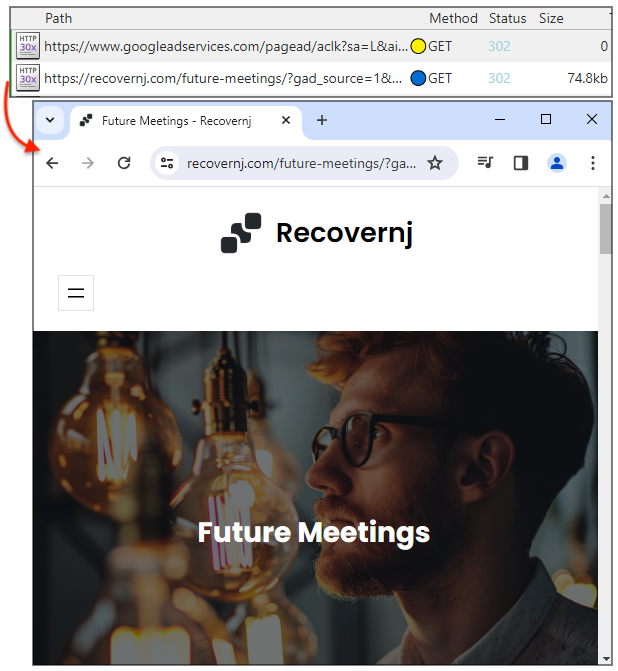
The Rick Astley redirect is mostly to mock security researchers investigating this campaign:
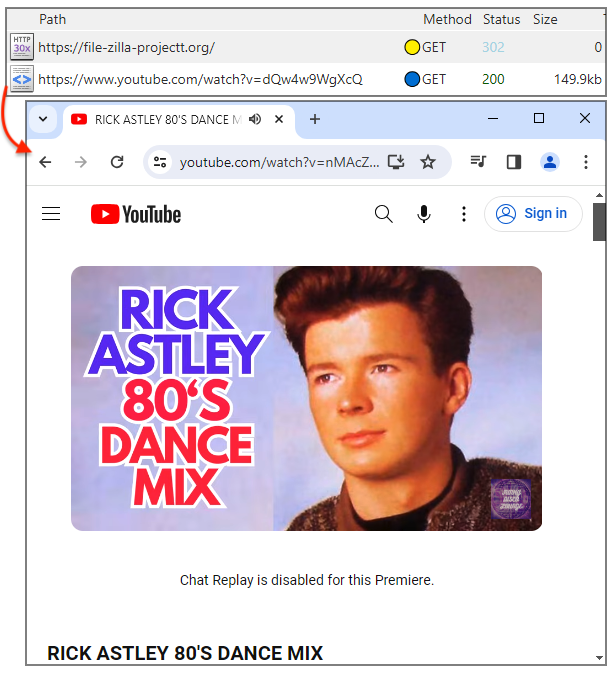
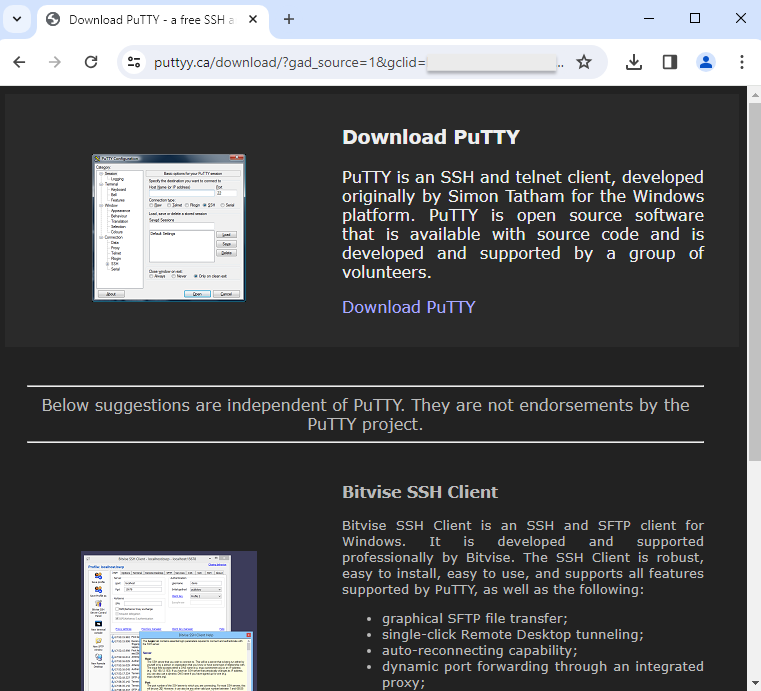
Actual lookalike pages are meant for potential victims. They are often good-looking copycats which could easily fool just about anyone:

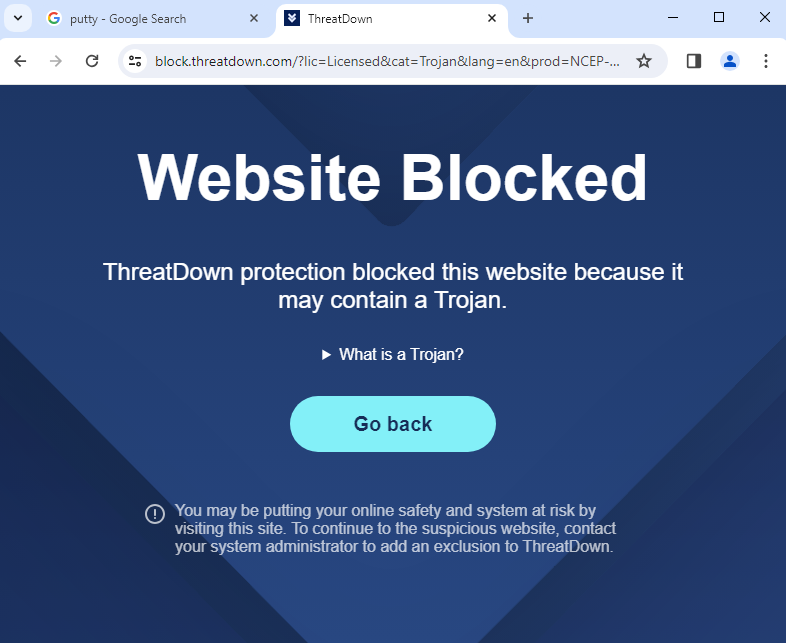
ThreatDown blocks these malicious websites to prevent your users from being social-engineered into downloading malware:
Step 3: Deploying malware via a fraudulent installer
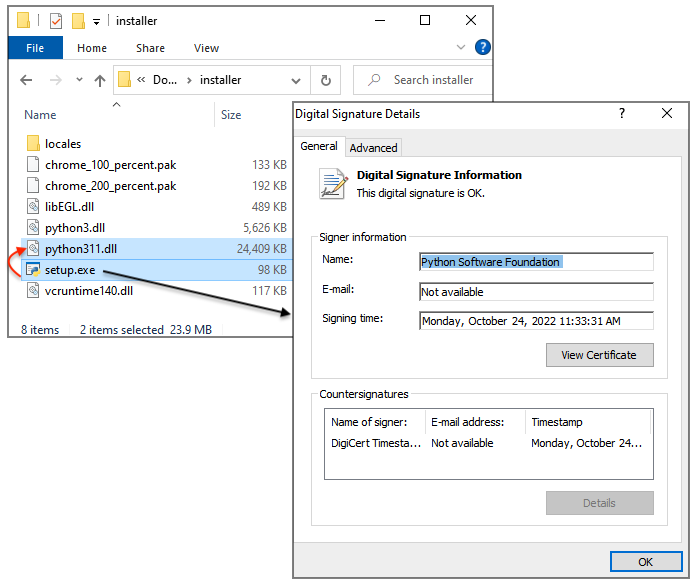
The final step in this malvertising chain consists of downloading and running the malware payload. Nitrogen uses a technique known as DLL sideloading whereby a legitimate and signed executable launches a DLL. In this case, setup.exe (from the Python Software Foundation) sideloads python311.dll (Nitrogen).
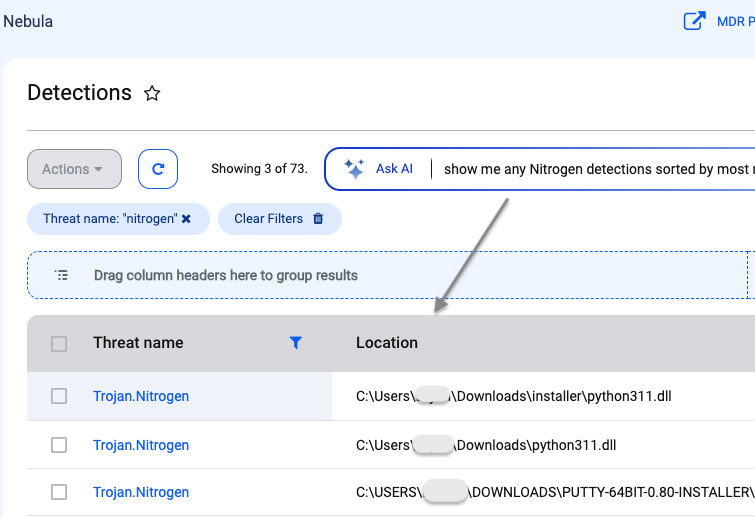
ThreatDown via its EDR engine quarantines the malicious DLL immediately. System administrators can log into their console and use the AI-assisted engine to quickly search and review the detection:
Recommendations
While there are many phishing training simulations for email threats, we aren’t aware of similar trainings for malvertising. Yet, the threat has become prevalent enough to warrant better user education.
Endpoints can be protected from malicious ads via group policies that restrict traffic coming from the main and lesser known ad networks. Click here for more information about DNS filtering via our Nebula platform.
Endpoint Detection and Response (EDR) is a cornerstone in your security posture, complemented by Managed Detection and Response (MDR) where analysts can quickly alert you of an impending intrusion.
Indicators of Compromise
Cloaking domains:
kunalicon[.]com
inzerille[.]com
recovernj[.]com
Lookalike sites:
file-zilla-projectt[.]org
puuty[.]org
pputy[.]com
puttyy[.]ca
Nitrogen payloads (URLs):
amplex-amplification[.]com/wp-includes/FileZilla_3.66.1_win64.zip
newarticles23[.]com/wp-includes/putty-64bit-0.80-installer.zip
support[.]hosting-hero[.]com/wp-includes/putty-64bit-0.80-installer.zip
mkt.geostrategy-ec[.]com/installer.zip
Nitrogen payloads (SHA256):
ecde4ca1588223d08b4fc314d6cf4bce82989f6f6a079e3eefe8533222da6281 2037ec95c91731f387d3c0c908db95184c93c3b8412b6b3ca3219f9f8ff60945 033a286218baca97da19810446f9ebbaf33be6549a5c260889d359e2062778cf
Nitrogen C2s:
94.156.65[.]98
94.156.65[.]115
