Cisco warned this week that two vulnerabilities, which have been used in zero-day attacks, are now being exploited to force ASA and FTD firewalls into reboot loops.
The tech giant released security updates on September 25 to address the two security flaws, stating that CVE-2025-20362 enables remote threat actors to access restricted URL endpoints without authentication, while CVE-2025-20333 allows authenticated attackers to gain remote code execution on vulnerable devices.
When chained, these vulnerabilities allow remote, unauthenticated attackers to gain complete control over unpatched systems.

The same day, CISA issued an emergency directive ordering U.S. federal agencies to secure their Cisco firewall devices against attacks using this exploit chain within 24 hours. CISA also mandated them to disconnect ASA devices reaching their end of support (EoS) from federal organization networks.
Threat monitoring service Shadowserver is currently tracking over 34,000 internet-exposed ASA and FTD instances vulnerable to CVE-2025-20333 and CVE-2025-20362 attacks, down from the nearly 50,000 unpatched firewalls it spotted in September.
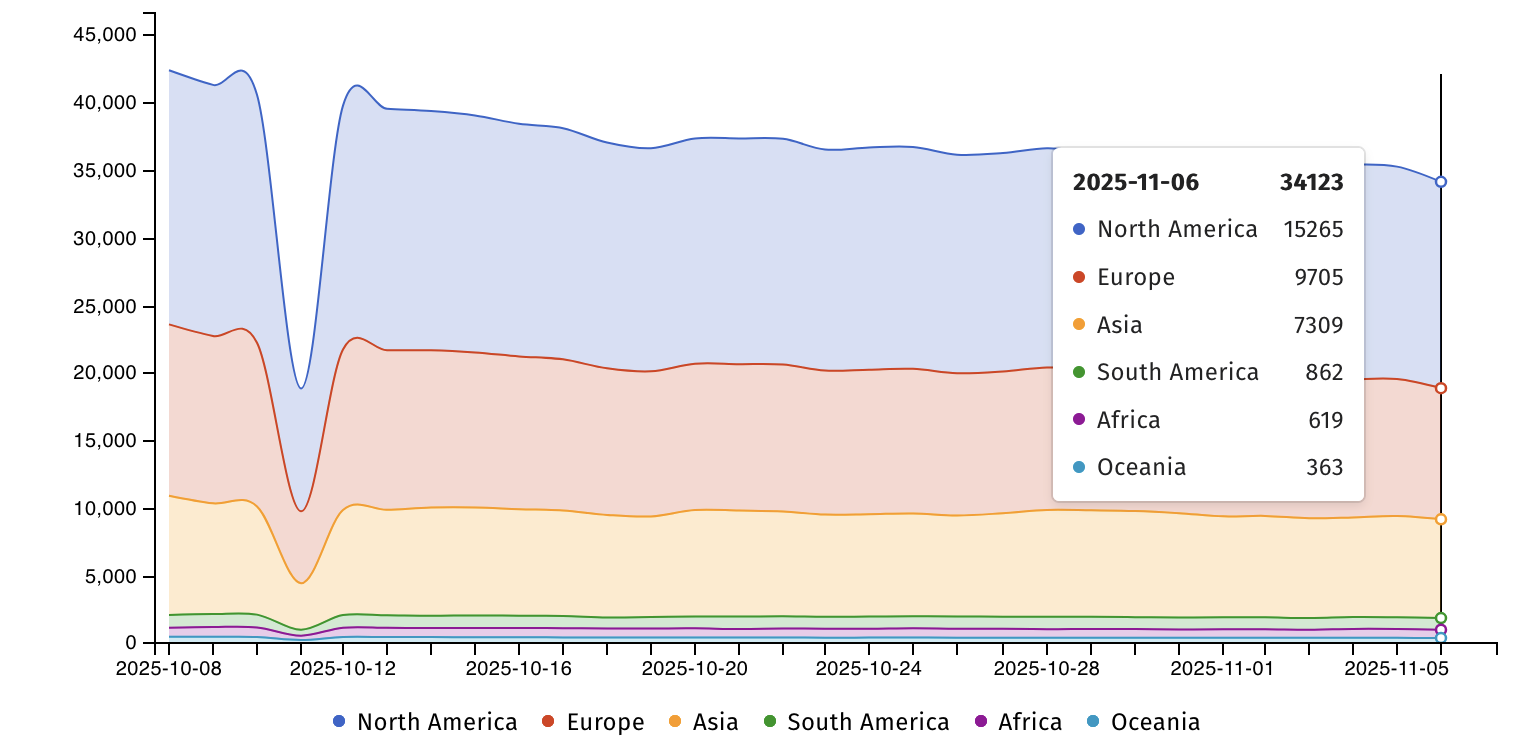
Now exploited in DoS attacks
“Cisco previously disclosed new vulnerabilities in certain Cisco ASA 5500-X devices running Cisco Secure Firewall ASA software with VPN web services enabled, discovered in collaboration with several government agencies. We attributed these attacks to the same state-sponsored group behind the 2024 ArcaneDoor campaign and urged customers to apply the available software fixes,” a Cisco spokesperson told BleepingComputer this week.
“On November 5, 2025, Cisco became aware of a new attack variant targeting devices running Cisco Secure ASA Software or Cisco Secure FTD Software releases affected by the same vulnerabilities. This attack can cause unpatched devices to unexpectedly reload, leading to denial of service (DoS) conditions.”
CISA and Cisco linked the attacks to the ArcaneDoor campaign, which exploited two other Cisco firewall zero-day bugs (CVE-2024-20353 and CVE-2024-20359) to breach government networks worldwide starting in November 2023. The UAT4356 threat group (tracked as STORM-1849 by Microsoft) behind the ArcaneDoor attacks deployed previously unknown Line Dancer in-memory shellcode loader and Line Runner backdoor malware to maintain persistence on compromised systems.
On September 25, Cisco fixed a third critical vulnerability (CVE-2025-20363) in its Cisco IOS and firewall software, which can allow unauthenticated threat actors to execute arbitrary code remotely. However, it didn’t directly link it to the attacks exploiting CVE-2025-20362 and CVE-2025-20333, saying that its Product Security Incident Response Team was “not aware of any public announcements or malicious use of the vulnerability.”
Since then, attackers have started exploiting another recently patched RCE vulnerability (CVE-2025-20352) in Cisco networking devices to deploy rootkit malware on unprotected Linux boxes.
More recently, on Thursday, Cisco released security updates to patch critical security flaws in its Contact Center software, which could enable attackers to bypass authentication (CVE-2025-20358) and execute commands with root privileges (CVE-2025-20354).
“We strongly recommend all customers upgrade to the software fixes outlined in our security advisories,” Cisco added on Thursday.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
