Cybercriminals are abusing Adobe Acrobat Sign, an online document signing service, to distribute info-stealing malware to unsuspecting users.
The service is being abused to send malicious emails that originate from the software company to bypass security protections and trick recipients into trusting the received email.
The strategy of abusing legitimate services isn’t new. Similar cases seen recently include the abuse of PayPal invoices, Google Docs comments, and more.
This new trend in cybercrime was reported by researchers at Avast, who warn about its effectiveness in bypassing security layers and tricking the targets.
Abusing legitimate services
Adobe Acrobat Sign is a free-to-try cloud-based e-signature service allowing users to send, sign, track, and manage electronic signatures.
Threat actors register with the service and abuse it to send messages to target email addresses, which link to a document (DOC, PDF, or HTML) hosted on Adobe’s servers (“eu1.documents.adobe.com/public/”).
The documents contain a link to a website that requests visitors to solve a CAPTCHA to add legitimacy and then serve them a ZIP archive that includes a copy of the Redline information stealer.
Redline is a dangerous malware capable of stealing account credentials, cryptocurrency wallets, credit cards, and other information stored on the breached device.
Avast has also spotted highly targeted attacks employing this method, like in one case where the target owned a popular YouTube channel with many subscribers.
Clicking on the link of the specifically-crafted message sent via Adobe Acrobat Sign took the victim to a document claiming music copyright infringement, a common and believable theme for YouTube channel owners.
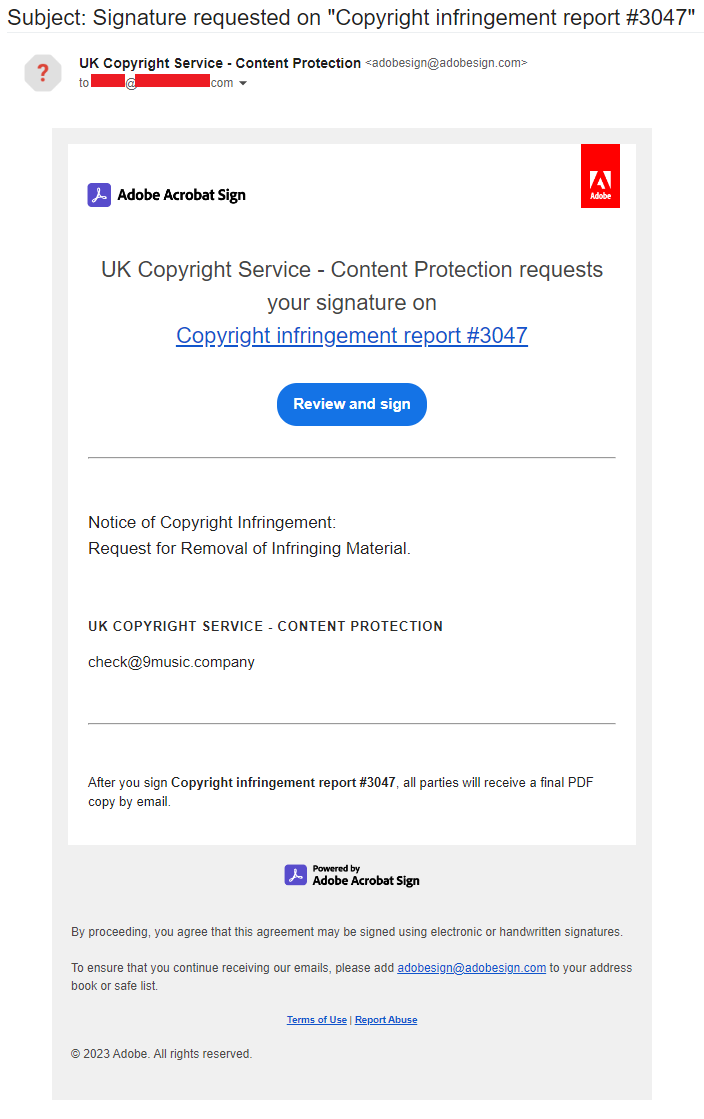
This time, the document was hosted on dochub.com, a legitimate online document signing platform.
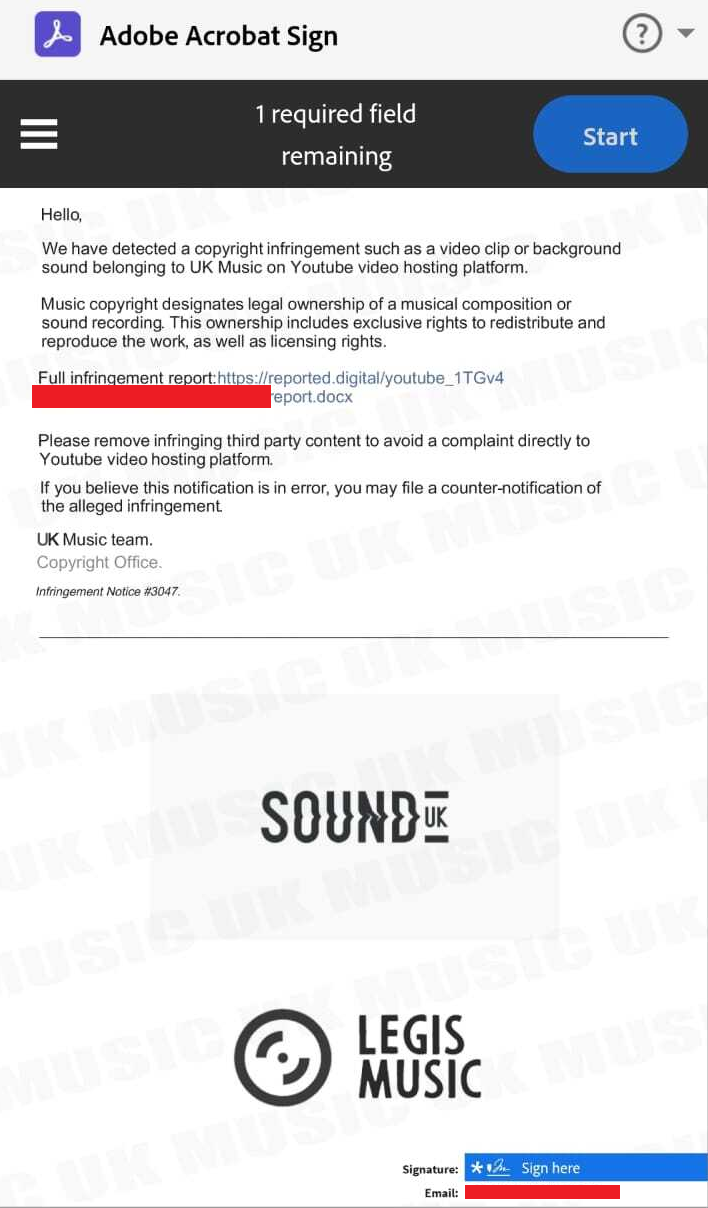
The link in the document leads to the same CAPTCHA-protected website that drops a copy of Redline.
In this case, however, the ZIP also contained several non-malicious executables from the GTA V game, likely an attempt to trick AV tools by mixing the payload with innocuous files.
Avast also reports that the Redline payload was artificially inflated to 400MB in both cases, which, again, helps protect from anti-virus scans. This same method was used in recent Emotet malware phishing campaigns.
Phishing actors are constantly looking for legitimate services that can be abused to promote their malicious emails, as these services help increase their inbox delivery and phishing success rates.
Avast has shared all details of its findings with Adobe and dochub.com, and hopefully, the two services will find a way to stop abuse from malware operators.
