Adobe is warning of a critical vulnerability (CVE-2025-54236) in its Commerce and Magento Open Source platforms that researchers call SessionReaper and describe as one of ” the most severe” flaws in the history of the product.
Today, the software company released a patch for the security issue that could be exploited without authentication to take control of customer accounts through the Commerce REST API.
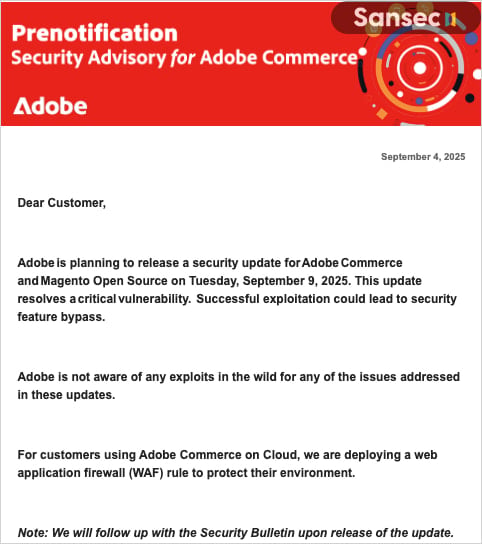
According to e-commerce security company Sansec, Adobe notified “selected Commerce customers” on September 4th of an upcoming emergency fix planned for September 9.
“Adobe is planning to release a security update for Adobe Commerce and Magento Open Source on Tuesday, September 9, 2025,” reads the notice.
“This update resolves a critical vulnerability. Successful exploitation could lead to security feature bypass.”
Customers using Adobe Commerce on Cloud are already protected by a web application firewall (WAF) rule deployed by Adobe as an intermediate measure.
Source: Sansec
Adobe says in the security bulletin that it is not aware of any exploitation activity in the wild. Sansec’s advisory also notes that the researchers have not seen any active exploitation of SessionReaper.
However, Sansec says that an initial hotfix for CVE-2025-54236 was leaked last week, which may give threat actors a potential head start on creating an exploit.
According to the researchers, successful exploitation “appears” to depend on storing session data on the file system, a default configuration that most stores use.
Administrators are strongly recommended to test and deploy the available patch (direct download, ZIP archive) immediately. The researchers warn that the fix disables internal Magento functionality that could lead to some custom or external code breaking.
To this end, Adobe updated its documentation for changes in the Adobe Commerce REST API constructor parameter injection.
“Please apply the hotfix as soon as possible. If you fail to do so, you will be vulnerable to this security issue, and Adobe will have limited means to help remediate” – Adobe
Sansec researchers expect CVE-2025-54236 to be abused via automation, at scale. They note that the vulnerability is among the most severe Magento vulnerabilities in the history of the platform, alongside CosmicSting, TrojanOrder, Ambionics SQLi, and Shoplift.
Similar issues in the past were leveraged for session forging, privilege escalation, internal service access, and code execution.
The security firm was able to reproduce the SessionReaper exploit but did not disclose the code or technical details, saying only that “the vulnerability follows a familiar pattern from last year’s CosmicSting attack.”

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
