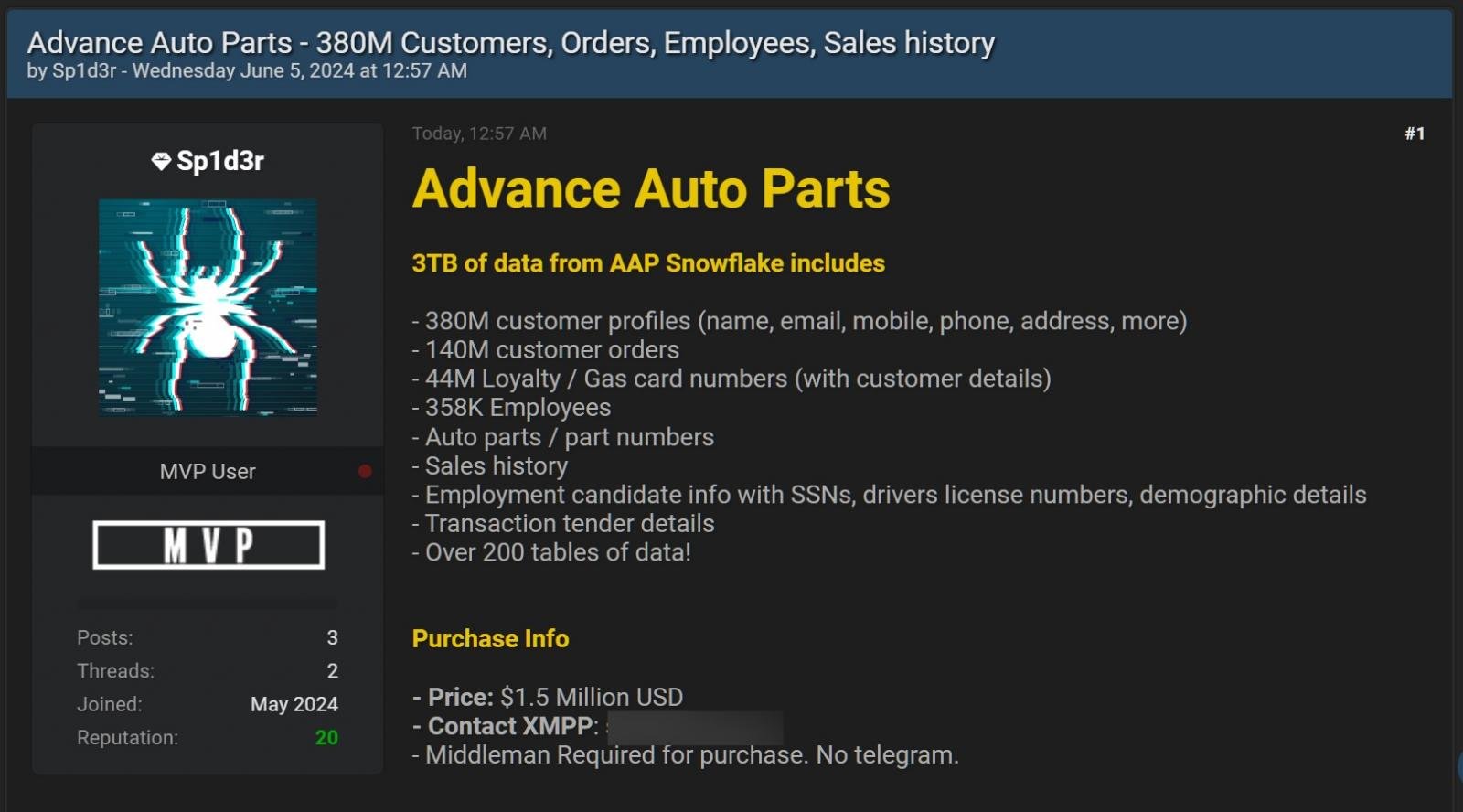
Threat actors claim to be selling 3TB of data from Advance Auto Parts, a leading automotive aftermarket parts provider, stolen after breaching the company’s Snowflake account.
Advance operates 4,777 stores and 320 Worldpac branches and serves 1,152 independently owned Carquest stores in the United States, Canada, Puerto Rico, the U.S. Virgin Islands, Mexico, and various Caribbean islands.
As the threat actor (using the Sp1d3r handle) revealed today, the massive archive of data stolen from Advance’s Snowflake cloud storage environment includes:
- 380 million customer profiles (name, email, mobile, phone, address, and more)
- 140 million customer orders
- 44 million Loyalty / Gas card numbers (with customer details)
- Auto parts/part numbers
- Sales history
- Employment candidate info with SSNs, driver’s license numbers, and demographic details
- Transaction tender details
While they also mentioned they’re selling the stolen information of 358,000 employees, the company currently has around 68,000. The difference could be old data belonging to former employees and associates.
BleepingComputer has been able to confirm that a large number of Advance Auto Parts customer records are legitimate.
Advance has yet to publicly disclose this breach and notify the U.S. Securities and Exchange Commission of the incident. BleepingComputer contacted an Advance Auto Parts spokesperson several times for confirmation and with questions about the breach but did not receive a reply.
Data stolen from Advance’s Snowflake account
The threat actor selling Advance’s data for $1.5 million on a hacking forum told BleepingComputer that the data had been stolen in recent attacks targeting cloud storage company Snowflake customers since at least mid-April 2024.
Snowflake’s cloud services are used by 9,437 customers, including high-profile companies worldwide, such as Adobe, AT&T, Kraft Heinz, Mastercard, Micron, Capital One, Doordash, HP, Nielsen, Novartis, Okta, PepsiCo, Siemens, Instacart, JetBlue, NBC Universal, US Foods, Western Union, Yamaha, and many others.
The threat actor also told BleepingComputer that the automotive company is not the only Snowflake customer whose data was exfiltrated. Some Snowflake customers have also allegedly already paid to get their data back after being contacted by the attackers, according to the threat actor, but BleepingComputer has not been able to independently confirm if this was true.
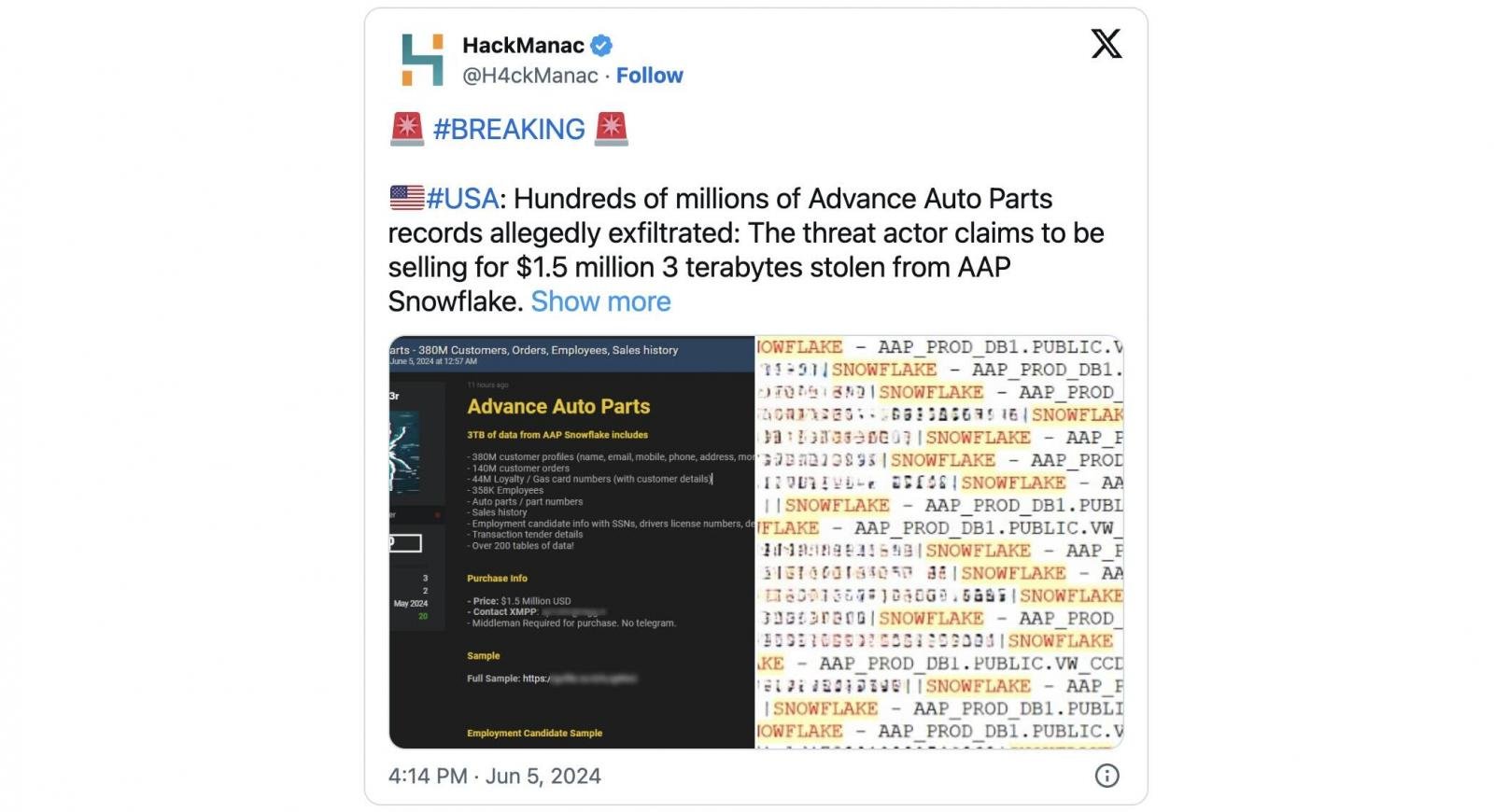
As first shared by threat intel company HackManac, the leaked data contains numerous references to ‘SNOWFLAKE,’ corroborating the threat actor’s claim that it was stolen in the recent Snowflake data theft attacks.
Recent Santander and Ticketmaster breaches were also linked to these attacks. On Friday, TicketMaster’s parent company, Live Nation, confirmed that a data breach hit the ticketing firm after its Snowflake account was compromised on May 20.
The company confirmed in a joint advisory with CrowdStrike and Mandiant that attackers use stolen credentials to target customers with multi-factor authentication disabled.
Snowflake added that while one employee’s demo account was compromised in this campaign using stolen credentials, this account didn’t provide the threat actors access to sensitive data and production or corporate systems.
“To date, we do not believe this activity is caused by any vulnerability, misconfiguration, or malicious activity within the Snowflake product,” Snowflake CISO Brad Jones said.
“Throughout the course of our ongoing investigation, we have promptly informed the limited number of customers who we believe may have been impacted.”
Mandiant Consulting CTO Charles Carmakal has told BleepingComputer that Mandiant has been assisting compromised Snowflake customers over the past few weeks. Mandiant’s investigations also indicate that the attackers are likely using credentials stolen by information-stealing malware to access the victims’ Snowflake tenants and steal data.
