Agniane stealer, a new information stealer, has emerged on the dark web. This discreet information stealer is being promoted in the hacking community with its compact design, robust encryption, and an array of features tailored to steal sensitive data.
A user named thx4drugs reportedly sells the info stealer for $50 monthly. Here is a quick look at the information stealer and why it threatens security.
To begin, Agniane Stealer, or any information-stealing malware, functions as a Trojan crafted to extract data from targeted systems.
These info stealers gather sensitive information from the victims, including usernames, passwords, credit card information, and other important data that can be used against the victims to extort money.
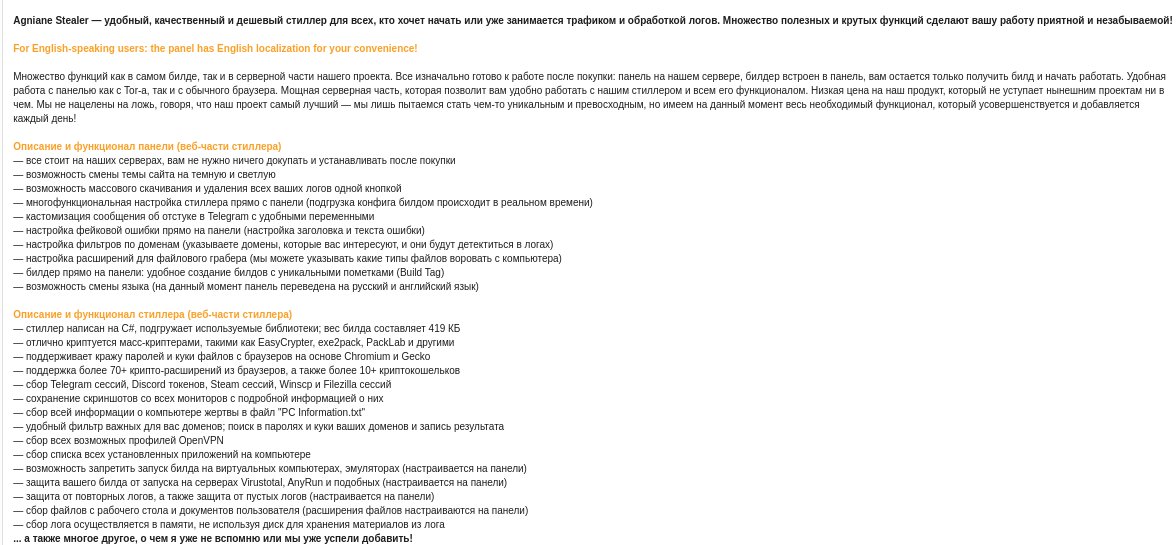
The Agniane stealer boasts a smaller footprint, yet its capabilities are far from modest, as claimed by the user selling the stealer.
Designed to infiltrate systems and silently extract valuable information, Agniane Stealer has set its sights on a wide range of targets.
Features and functions of Agniane stealer
The primary function of Agniane Stealer is to harvest sensitive login details. This includes usernames and passwords, which it meticulously captures from various sources.
What makes this info stealer particularly concerning is its ability to encrypt and transfer the stolen data to remote systems, either through email channels or over network connections.
Agniane Stealer comes armed with an arsenal of capabilities that underscore its proficiency as an information stealer.
Its most notable feature is its proficiency in stealing passwords and cookies stored within popular web browsers. By targeting browsers such as Chrome, Firefox, and Edge, Agniane Stealer can amass a wealth of user credentials.
Moreover, Agniane Stealer extends its reach to messaging platforms like Telegram and Discord, allowing it to intercept ongoing sessions and glean private conversations. In the wrong hands, this information could lead to dire consequences for unsuspecting users.
Agniane Stealer also demonstrates a keen interest in cryptocurrency. It seeks out crypto wallets, aiming to plunder digital riches without leaving a trace. The stealer even captures screenshots, providing cybercriminals with a visual snapshot of the victim’s activities.
The need to halt Agniane Stealer and similar info-Stealing malware
The seller behind Agniane Stealer paints a dark picture of its capabilities.
Described as a “Convenient, high-quality and cheap stealer for everyone who wants to start or is already engaged in traffic and log processing,” this stealer is marketed as a one-stop solution for aspiring hackers and cybercriminals alike.
At a mere $50 per month, Agniane Stealer presents itself as an accessible option for those seeking to exploit stolen information for financial gain.
While the seller attempts to downplay the risks associated with Agniane Stealer, it’s important to recognize the potential harm it can cause. From compromised accounts to identity theft, the consequences of falling victim to this info stealer can be devastating.
In addition, the Agniane stealer isn’t the sole data thief causing turmoil within the hidden corners of the web.
The Indian Computer Emergency Response Team (CERT-in) recently unveiled a significant data-stealing menace dubbed the “Redline info-stealer,” which operates as a Malware-as-a-Service (MaaS) framework.
Disseminated via phishing emails, this malware lures victims into clicking on attachments, enabling it to steal user data, crypto wallet info, browser details, VPN credentials, and more. Furthermore, the attacker gains access to victim specifics like geolocation and IP.
Notably, the malware has expanded its distribution through the OneNote service. Developed using C#/.NET, the malware adopts disguises, encoding, and communication tactics to carry out its malicious actions, encompassing DLLs for data collection and system info retrieval via WMI.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
