Jamf Threat Labs has identified a new family of malicious stealers tracked as DigitStealer, representing a significant evolution in macOS-targeted malware.
Unlike traditional infostealers that follow linear execution paths, DigitStealer introduced sophisticated multi-stage attack techniques, extensive anti-analysis checks, and novel persistence mechanisms, demonstrating the threat actors’ deep understanding of macOS architecture.
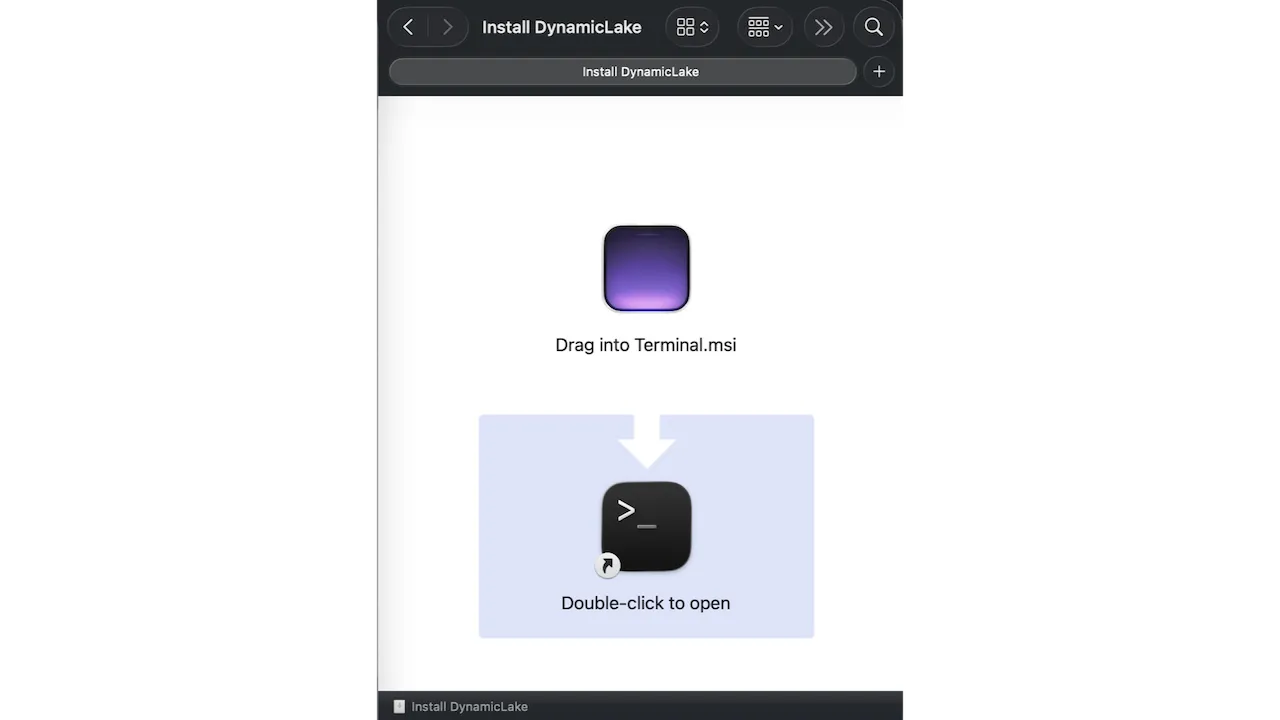
The DigitStealer campaign begins with a seemingly legitimate application disguised as DynamicLake, a genuine macOS utility.
The malicious payload is distributed through an unsigned disk image titled “DynamicLake.dmg” (SHA-256: 5c73987e642b8f8067c2f2b92af9fd923c25b2ec) hosted on the deceptive domain dynamiclake[.]org.
Unlike the legitimate version signed with Developer Team ID XT766AV9R9, this variant lacks proper code signing and remained completely undetected on VirusTotal at the time of analysis.
The disk image employs the drag-to-terminal technique to override macOS Gatekeeper protections and gain initial code execution.
Notably, the embedded dropper file uses a “.msi” extension typically associated with Windows installers which is unusual for macOS and may represent either an attempt to appear harmless or careless packaging by the malware authors.
Multi-Stage Attack Architecture
The attack unfolds through a sophisticated four-stage deployment process, each designed to evade detection through obfuscation and functional separation.
Stage One: Sophisticated Base Dropper begins with a simple bash one-liner that retrieves an obfuscated, base64-encoded script from the attacker’s infrastructure. What distinguishes this dropper is its advanced anti-analysis capabilities.
The script performs extensive checks for virtual machines, debugging environments, and notably, Apple Silicon-specific hardware features.
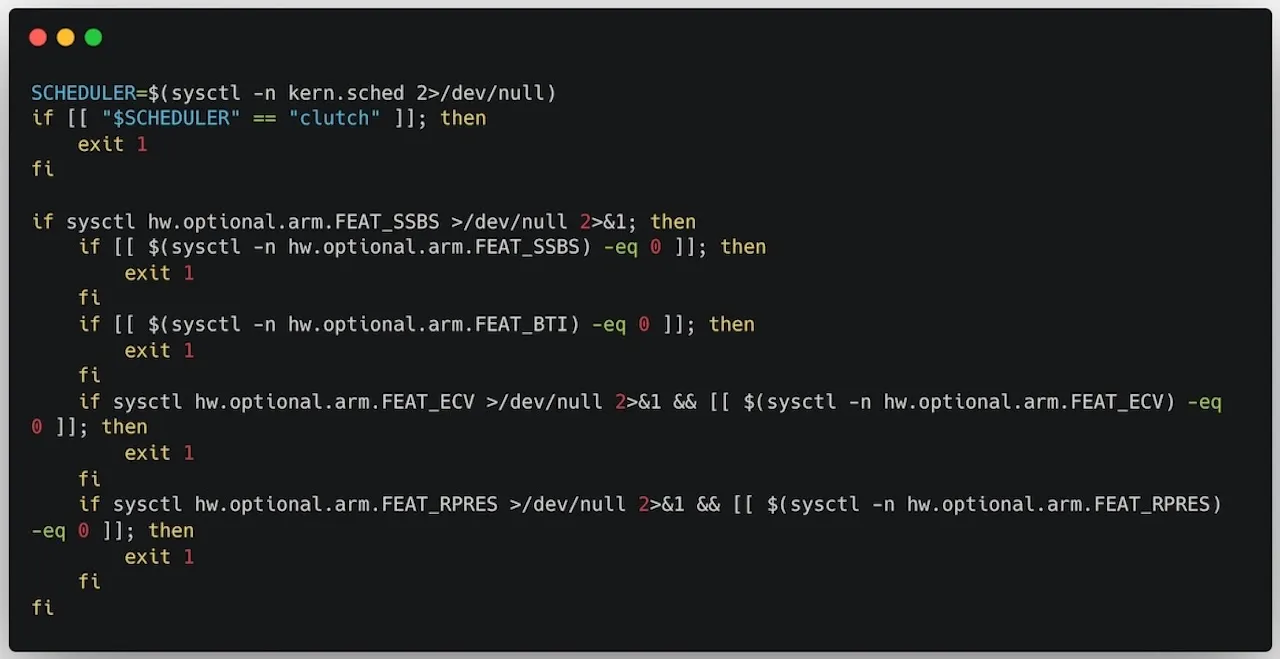

It deliberately avoids execution on M1 systems while targeting M2 and newer chips by checking for specific ARM features like FEAT_BTI, FEAT_SSBS, FEAT_ECV, and FEAT_RPRES.
Additionally, the malware includes geolocation-based filtering that terminates execution if the system locale matches certain countries, potentially indicating the threat actors’ operational base.


Stages Two through Four involve four separate payloads executed entirely in memory. The first payload is a plaintext AppleScript infostealer that prompts users for credentials and harvests sensitive data, including browser information, cryptocurrency wallets, keychain databases, and Telegram configurations.
The second payload, obfuscated in JavaScript for Automation (JXA), mirrors traditional infostealer functionality with specialized focus on crypto assets.
A particularly noteworthy innovation is DigitStealer’s approach to compromising Ledger Live. Rather than replacing the application with a single trojaned version, the malware downloads three separate components and concatenates them to recreate the app.asar file a multi-part technique designed to evade single-file detection systems.
The malicious version reverts the application name to “Ledger Live” and downgrades the version number, potentially to bypass signature validation.
Dynamic Command Execution
The final stage establishes persistence through a Launch Agent that employs an innovative technique: rather than containing static payloads, it dynamically retrieves commands from TXT records hosted on the attacker’s control server.
This approach represents a departure from conventional macOS malware persistence methods and demonstrates sophisticated operational security practices.
The persistent agent continuously polls the command and control server approximately every ten seconds, sending the system’s hardware UUID hashed with MD5.
DigitStealer’s sophisticated architecture reflects the evolving threat landscape targeting Apple’s ecosystem. The threat actors display advanced knowledge of macOS internals, legitimate cloud services for payload hosting, and modern anti-analysis techniques.


By splitting functionality across multiple stages and leveraging services like Cloudflare’s pages.dev, the malware authors complicate detection and blocking efforts.
Security teams should prioritize behavioral detection over reliance on static signatures, as these payloads execute entirely in memory with minimal disk footprint.
Organizations using Jamf Protect are advised to ensure threat prevention and advanced threat controls remain enabled and configured to blocking mode.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




