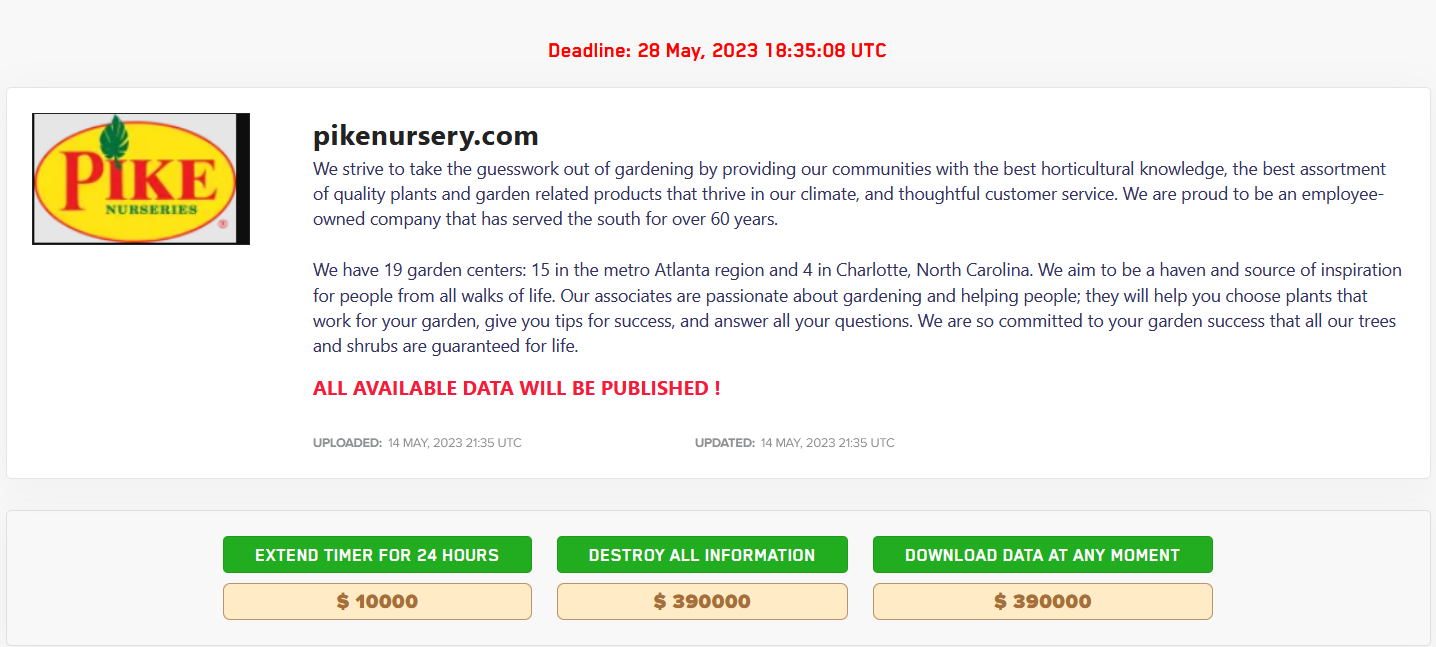
Renowned gardening and horticultural company Pike Nurseries was targeted by the notorious LockBit ransomware group. The threat actors have explicitly stated their intentions to release the company’s sensitive data on May 28, 2023.
In a post shared on their leak site, the ransomware group shared details about the alleged Pike Nurseries cyber attack along with the option to extend the timer, destroy information and download the stolen data.
The Cyber Express team has reached out to the company for confirmation regarding the Pike Nurseries cyber attack. Unfortunately, the company has not responded yet.
As a trusted name in the gardening community, the alleged Pike Nurseries cyber attack immediately puts customer data at risk.
The company has been dedicated to providing a wide range of quality plants and garden-related products tailored to thrive in the local climate.
Pike Nurseries cyber attack explained
The LockBit gang, previously known as ABCD, has gained notoriety for their involvement in various ransomware campaigns. The group operates through different iterations of the LockBit ransomware, with LockBit 3.0 being their most recent release in June 2022.
According to researchers, LockBit 2.0, released by the group in May 2022, accounted for 46% of all ransomware attacks that occurred throughout the year.
These statistics highlight the scale and effectiveness of the LockBit gang’s operations, emphasizing the urgent need for companies like Pike Nurseries to enhance their cybersecurity measures.
While the details of the potential Pike Nurseries cyber attack remain uncertain, the cyber attack serves as a reminder of the persistent threats organizations face in today’s digital landscape.
As we await further information on the Pike Nurseries cyber attack, individuals must stay informed about potential risks and exercise caution when sharing personal information online.
By proactively protecting ourselves and supporting affected organizations, we can collectively combat the growing threat of cybercrime and strive for a safer digital future.
Pike Nurseries cyber attack and LockBit victims
Pike Nurseries cyber attack is the latest in the long list of LockBit ransomware’s attacks.
When it comes to the top 10 ransomware gangs, LockBit maintains a hefty first position, according to cybersecurity researcher Dominic Alvieri.
With a staggering 1,716 public victims to their name, LockBit has been averaging over one company per day since their initial formation as ABCD, he noted in his list of top 10 ransomware gangs.
“No other group even comes close,” Alvieri wrote. Alphv/BlackCat comes in at a distant second with 371 public victims, followed by Clop with 251 and Black Basta with 226.
LockBit 3.0, also referred to as LockBit Black, represents the most recent variant of ransomware belonging to the LockBit family. It was initially detected in September 2019. Its primary targets are organizations capable of making substantial ransom payments, and it possesses the ability to self-propagate.
This latest version, identified towards the end of 2022, leverages encryption techniques to extract files from infected devices, demanding a ransom for their restoration. A report conducted by Sophos reveals that LockBit 3.0 maintains most of the functionalities observed in LockBit 2.0 while introducing new behaviors that enhance its resistance to analysis.
In certain instances, LockBit 3.0 mandates the use of a 32-character password by affiliates when launching the ransomware binary. The typical attack process involves infecting the targeted device, encrypting files, removing specific services, and modifying the wallpaper.
Failure to pay the ransom may result in the data being sold on the dark web. LockBit 3.0 is notorious for exploiting Windows Defender to deploy Cobalt Strike, which is a penetration testing tool, thereby initiating a series of malware infections.
LockBit functions as a Ransomware-as-a-Service (RaaS) model, collaborating with affiliates who may lack the necessary resources to develop and execute their own attacks. As per a December 2022 alert issued by the U.S. Department of Health & Human Services, a portion of the ransom proceeds is shared with the affiliated hacker.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
