A sophisticated Linux backdoor named GhostPenguin has been discovered by Trend Micro Research, evading detection for over four months after its initial submission to VirusTotal in July 2025.
The threat represents a new breed of stealthy malware designed to maintain a low profile while delivering comprehensive remote access and file system manipulation capabilities to threat actors.
The malware establishes sophisticated session handshake mechanisms and synchronizes multiple threads to handle critical functions, including registration, heartbeat signaling, and reliable command delivery.
Its architectural design prioritizes stealth and persistence, making it particularly dangerous for Linux server environments.
The backdoor’s discovery marks a significant advancement in proactive threat hunting methodologies.
Trend Micro Research employed an AI-driven, automated threat hunting pipeline explicitly designed to surface zero-detection Linux samples from VirusTotal.
GhostPenguin is a multi-threaded C++ backdoor that communicates with command-and-control servers over an RC5-encrypted UDP channel through port 53.
The parser extracted the relevant fields and mapped them into the database. We also stored the raw JSON files separately so they can be used later for research or processed by other tools.
Rather than relying on traditional signature-based detection, the approach extracted artifacts from thousands of malware samples, generated structured profiles, and deployed custom YARA rules combined with VirusTotal hunting queries to identify previously undetected threats.
These artifacts were stored in a structured database and tagged for comprehensive analysis, enabling researchers to build effective hunting rules against zero-detection samples that would otherwise evade traditional security tools.
Malware Technical Capabilities
Upon execution, GhostPenguin collects extensive system information including IP addresses, gateway details, OS versions, hostnames, and usernames, transmitting this data to its command-and-control server during a registration phase.
The investigation demonstrated how modern security teams can extract and analyze useful artifacts such as strings, API calls, behavioral patterns, function names, variable names, and constants from known attack samples.
The malware then receives and executes commands from remote operators, providing capabilities that span remote shell access and comprehensive file operations.
Supported commands enable threat actors to spawn remote shells via “/bin/sh” and perform extensive file system manipulation.
These operations include creating, deleting, and renaming files; reading and writing file contents; modifying file timestamps; and searching for files by specific extensions.
Directory operations are equally comprehensive, allowing full filesystem traversal and manipulation.
GhostPenguin implements a custom reliability layer over the inherently unreliable UDP protocol, ensuring commands and results are delivered even when network packets are dropped.
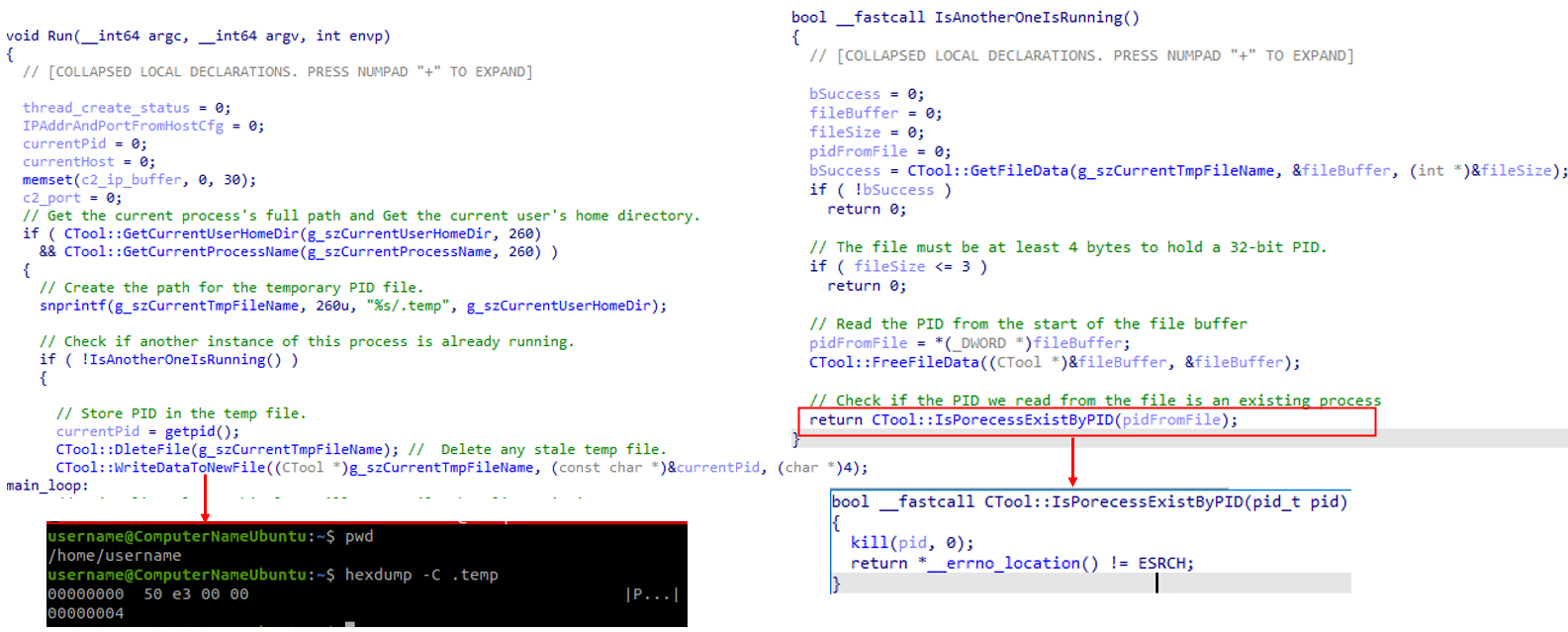
If the call confirms the PID corresponds to a live process, the malware concludes that an active instance is already running and aborts initialization; otherwise, the stale entry is ignored and execution proceeds.
The malware maintains outgoing packets in a global queue, implementing automatic retry mechanisms until command-and-control servers confirm receipt through acknowledgment packets.
Evidence of Active Development
Analysis revealed that GhostPenguin remains actively under development. The researchers identified multiple indicators including debug artifacts and unused persistence functions implemented but never invoked by the malware.
The malware then enters its main operational loop, which continues until a global exit flag g_bIsClientExit is set. Inside this loop, it iterates through a list of C&C server addresses defined in a global configuration structure g_lpLinuxClientHostCfg.
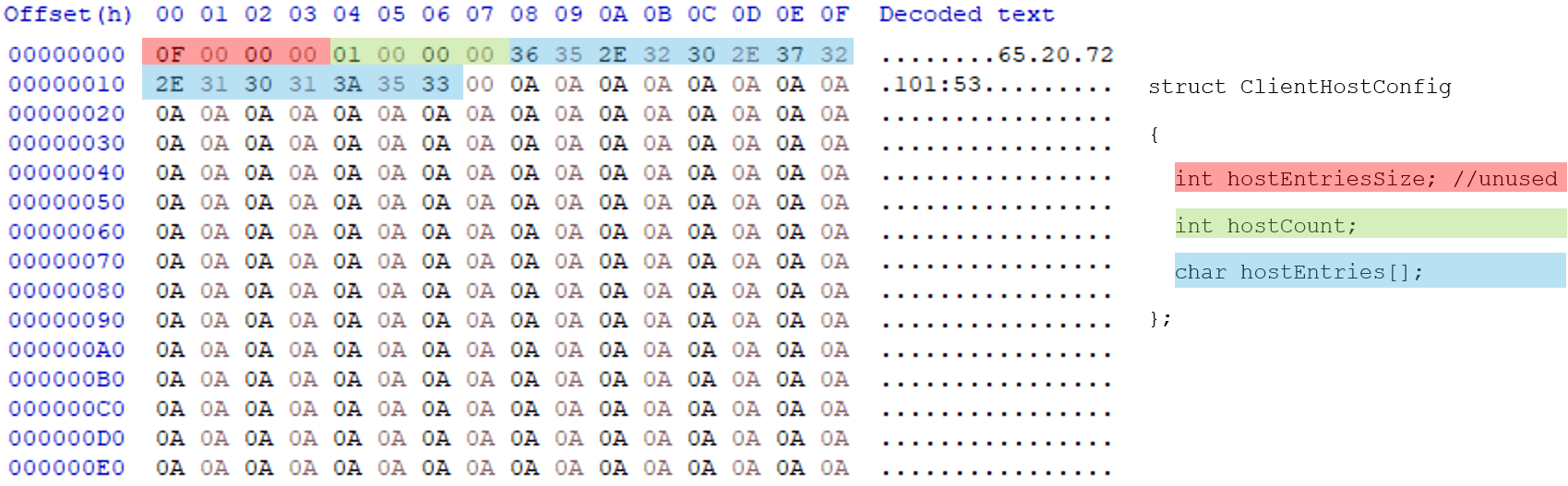
The discovery of leftover debug configuration variables containing separate testing domains and IP addresses further suggests the backdoor is in development stages rather than representing a mature, production-ready threat.
Trend Vision One platform now detects and blocks indicators of compromise associated with GhostPenguin, providing customers with hunting queries, threat insights, and intelligence reports.
The discovery underscores the increasing importance of AI-automated threat hunting in identifying sophisticated evasive malware that continues to pose significant risks to Linux server infrastructure across enterprise environments.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.