AISURU botnet launched a DDoS attack targeting Black Myth: Wukong distribution platforms in August 2024 that leveraged a 0DAY vulnerability on cnPilot routers and used RC4 encryption for sample strings.
After a brief pause in September, the botnet reappeared in October with the name kitty and was updated again in November as AIRASHI.
The current AIRASHI variant uses ChaCha20 encryption for CNC communication with HMAC-SHA256 verification and boasts rich IP resources for the CNC server that make it resilient to takedown attempts.
AI-RASHI botnet spreads through NDAY vulnerabilities, TELNET weak passwords, and 0DAY vulnerabilities. It exploits various vulnerabilities, including CVE-2013-3307, CVE-2016-20016, etc.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Botnet operators often showcase their attack capabilities through social media platforms to attract potential customers or intimidate competitors. The AIRASHI botnet uses this exact method to prove its attack capabilities, which are around 1-3 Tbps.

The AIRASHI botnet is a DDoS botnet that targets various industries globally by frequently updating and has multiple versions with functionalities including DDoS attacks, operating system command execution, and proxy services.
The latest version communicates with the C2 server through SOCKS5 proxies using username jjktkegl and password 2bd463maabw5, which is not encrypted and uses a switch-case structure for handling different stages.
It sends heartbeat packets every 2 minutes and receives commands from the C2 server in the format of cmdtype+payload, while DDoS commands include a new AttckID field.


AIHASHI is a malware family that includes AIRASHI-DDoS, Go-Proxisdk, and AIRASHI-Proxy. AIRASHI-DDoS and AIRASHI-Proxy use RC4 for string decryption with a 16-byte key and share some commonalities with AISURU.
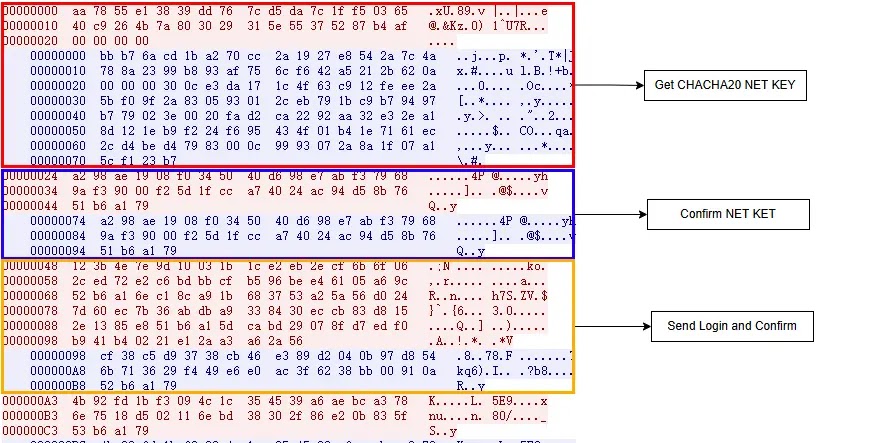
They use a custom protocol with HMAC-SHA256 for message integrity verification and CHACHA20 for encryption that involves key negotiation, key confirmation, sending a startup packet and check-in confirmation.
According to XLab, AIRASHI-DDoS supports 13 message types, including get net key, confirm net key, confirm login, heartbeat, start attack, exit, killer report, exec command, and reverse shell.
On the other hand, AIRASHI-Proxy is only capable of supporting five different types of messages, which include get net key, confirm net key, confirm login, heartbeat, and an unknown format.

The Snort rule detects potential attempts to exploit a 0-day vulnerability affecting cnPilot routers that identifies malicious traffic by searching for specific keywords like “execute_script,” “sys_list,” and “ASPSSIONID” within network packets.
To gain unauthorized access to the router and possibly compromise the system, these keywords are indicative of commands that are frequently used by attackers.
Deploying this rule in the user intrusion detection system (IDS) or intrusion prevention system (IPS) will help them to monitor network traffic for signs of this exploit and proactively mitigate the risk of successful attacks.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
