Weeks after launching its new leak site, the Akira ransomware group has listed three victims: American engineering consultancy business 4LEAF, US-based packaging materials manufacturer Park-Rite, and Canadian child care service Family Day Care Services.
Akira ransomware group has made three posts on the companies, each questioning the operations of the respective businesses, ending with a threat to release company records.
No indication of sample data or ransom demand were there on the posts. All three firms are yet to reply to the requests The Cyber Express made to comment on the attacks by the Akira ransomware group.
Akira ransomware group and new victims
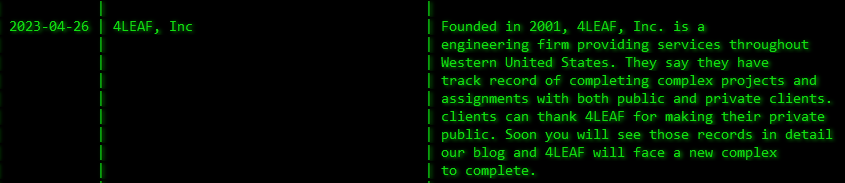
“They say they have track record of completing complex projects and assignments with both public and private clients,” read the post on the leak site of the Akira Ransomware Group, hinting an attempt to build pressure on 4LEAF from their clients.
“Clients can thank ALEAF for making their private (information) public. Soon you will see those records in detail our blog and ALEAF will face a new complex to complete.”
The website of 4LEAF was accessible at the time of writing, indicating that the alleged cyberattack did not impact the website.
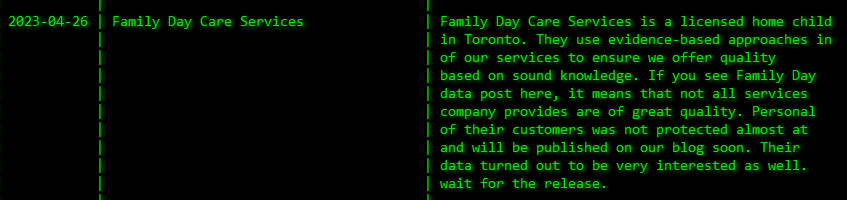
The same day after posting about the 4LEAF cyberattack on April 26, Toronto-based Family Day Care Services was also listed as a victim of their ransomware attacks. The website of the daycare was accessible at the time of writing.
The leak site post read, “If you see Family Day data post here, it means that not all services company provides are of great quality. Personal (information) of their customers was not protected….” The post threatened that all the stolen data from the cyberattack will be leaked on the group’s blog.
Akira ransomware group: Mode of operation
The Akira ransomware group add the .Akira extension to affected files. The Akira ransomware encrypts files and demands a ransom to decrypt the files. Hackers often reach the targeted users and systems via phishing emails with malicious attachments.
The ransomware group also infiltrates networks and renders the device inaccessible to the user, depending upon the malware. The Akira ransomware payload was also used to infect a system and then attack other devices.
The malware payload was found to get dropped in %Local%, %Temp%, %Windows%, %SystemDrive%, etc. The ransomware targets video files with the extension of .mp4 and .avi, audio files with .mp3 and .wav extensions, and images with .jpg and .png extensions among others.
The Akira Ransomware group seems to be an independent operation, as it does not belong to any larger family of ransomware or use the Ransomware as a Service (RaaS) tactic, observed a threat assessment report by Enigma Software.
The ransomware Trojan was first spotted on August 28, 2017, and appeared to be still in the testing phase then. The researchers noted that the Trojan is being distributed by hacking unprotected websites, specifically targeting those powered by WordPress.
“Once the victim loses access to their files, these Trojans demand the payment of a ransom in exchange for the decryption key necessary to recover the affected files,” the report said.
“Unfortunately, these Trojans use very strong encryption algorithms that make it nearly impossible to recover files encrypted by the attack. Because of this, it is necessary to have file backups to prevent becoming a victim of these infections.”
In the event of an Akira Ransomware infection, security experts advise against paying the ransom demanded by the attackers, as this does not guarantee that the files will be decrypted.
Instead, they recommend having proper measures in place to recover the encrypted files, such as having file backups and using a reliable security program that is up-to-date.
While the Akira Ransomware is not yet fully operational, computer users are advised to take precautions to protect themselves from the threat.
This includes keeping their security programs up-to-date, applying any security updates available for their website platforms, and having file backups in place to restore any affected files.
Related