Jérôme Segura, cybercriminals are exploiting search parameter vulnerabilities to inject fake phone numbers into the legitimate websites of major brands like Apple, Bank of America, Facebook, HP, Microsoft, Netflix, and PayPal.
This sophisticated attack, technically termed a “search parameter injection attack,” manipulates the search functionality of these trusted platforms, deceiving users into contacting scammers under the guise of official customer support.
Cybercriminals Exploit Search Parameter Vulnerabilities
By leveraging sponsored search ads on Google, attackers guide unsuspecting victims to authentic websites, where malicious URL parameters overlay fraudulent contact details, creating a seamless illusion of legitimacy.
The mechanics of this scam are as insidious as they are clever. Cybercriminals craft URLs that exploit reflected input vulnerabilities in a website’s search functionality, embedding fake phone numbers directly into the displayed search results.
For instance, on Netflix’s genuine support page, users see the legitimate URL in their browser’s address bar, and the site’s layout appears authentic.
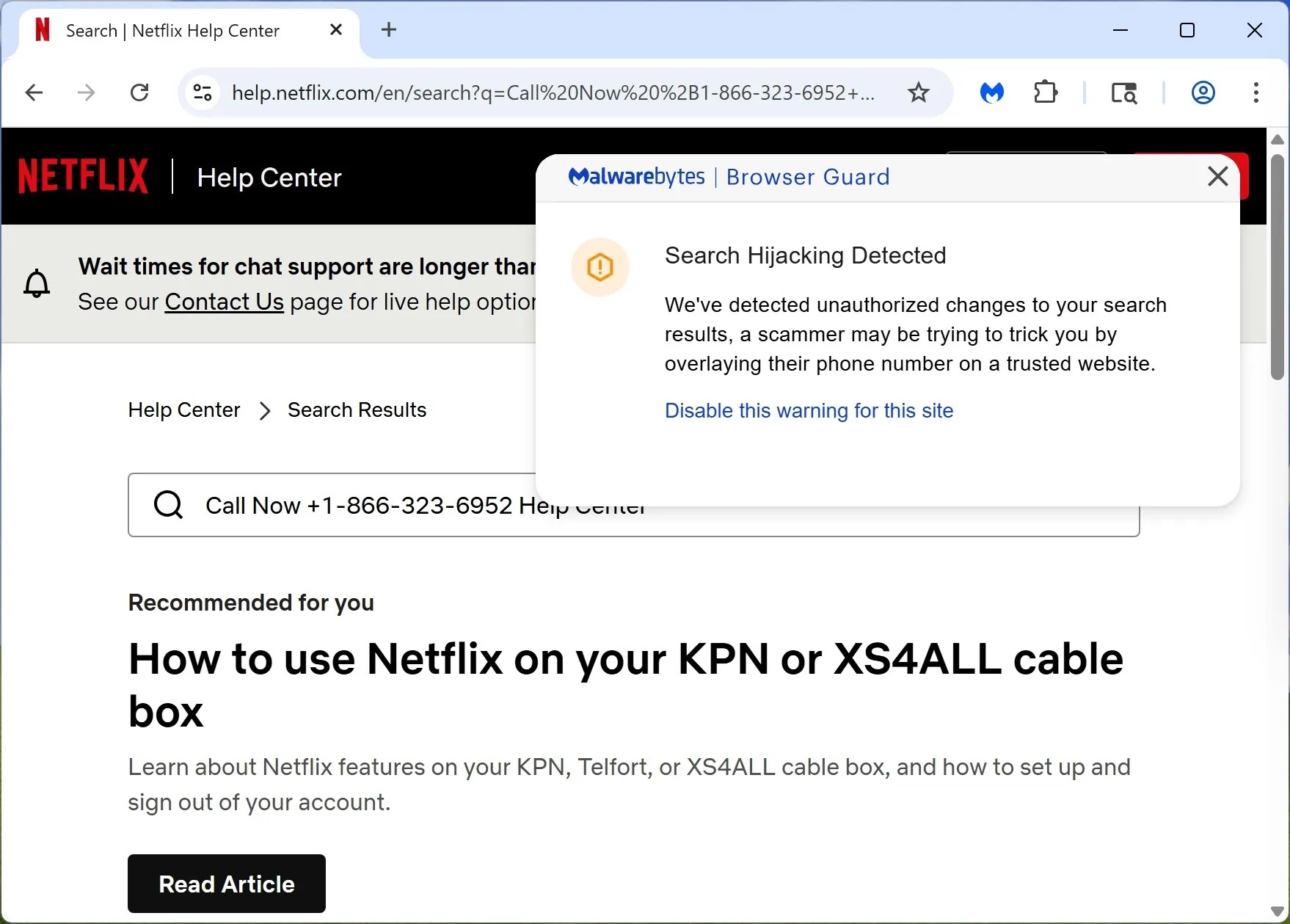
However, the search result prominently displays a scammer’s phone number, masquerading as an official contact.
This exploit thrives on the lack of proper sanitization or validation of user input in the search query parameter, allowing attackers to poison the information users rely on.
A Deceptive Trap with Real-World Consequences
Once victims dial the number, they are connected to fraudsters impersonating brand representatives, who then attempt to extract sensitive personal data, financial details, or even remote access to the victim’s device.
In cases involving financial institutions like Bank of America or PayPal, the ultimate goal is often to drain the victim’s accounts.
The impact of these attacks is amplified by their subtlety. On platforms like HP, small discrepancies such as the phrase “4 Results for” preceding the scammer’s text might hint at foul play, but most users, trusting the legitimacy of the website, overlook these clues.
Apple’s case is particularly deceptive, with the manipulated page suggesting no search results were found, nudging users to call the displayed fraudulent number for assistance.
This psychological manipulation, paired with the technical exploitation of trusted domains, makes these scams extraordinarily effective.
Fortunately, tools like Malwarebytes Browser Guard have begun to detect such manipulations, issuing warnings about “Search Hijacking Detected” to alert users of unauthorized alterations to search results.
According to the Report, This wave of attacks underscores a critical vulnerability in how major brands handle search parameters on their websites, exposing a gap in web security that cybercriminals are quick to exploit.
The trust users place in familiar URLs and sponsored Google ads becomes a weapon against them, as attackers blend authenticity with deception to devastating effect.
As this scam continues to target high-profile companies, it serves as a stark reminder for both users and corporations to prioritize robust input validation and heightened vigilance.
Without swift action to sanitize search functionalities and educate the public, these search parameter injection attacks risk eroding consumer confidence in even the most reputable digital platforms, turning a routine search for support into a gateway for fraud.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
