American wholesale drug company AmerisourceBergen confirmed a ransomware attack following its name being added to the Lorenz ransomware group’s extortion site.
The healthcare and pharmaceutical company confirmed the attack to BleepingComputer stating that the systems of its subsidiary were compromised. MWI Animal Health, the business of AmerisourceBergen was hacked by the Lorenz ransomware gang.
The date of exfiltration mentioned on the extortion site of the Lorenz ransomware group’s post was November 1, 2022, while the data was reportedly posted recently. This raises a question on the authenticity of the content claimed to be from the AmerisourceBergen ransomware attack.
Cybersecurity researcher Dominic Alvieri noted in his tweet that AmerisourceBergen’s subsidiary was hacked and exploited using a Lorenz backdoor. “Initial entry appears to be May 2022 while additional data was exfiltrated last week a few days before the new backdated post,” the tweet read.
(Photo: Dominic Alvieri)
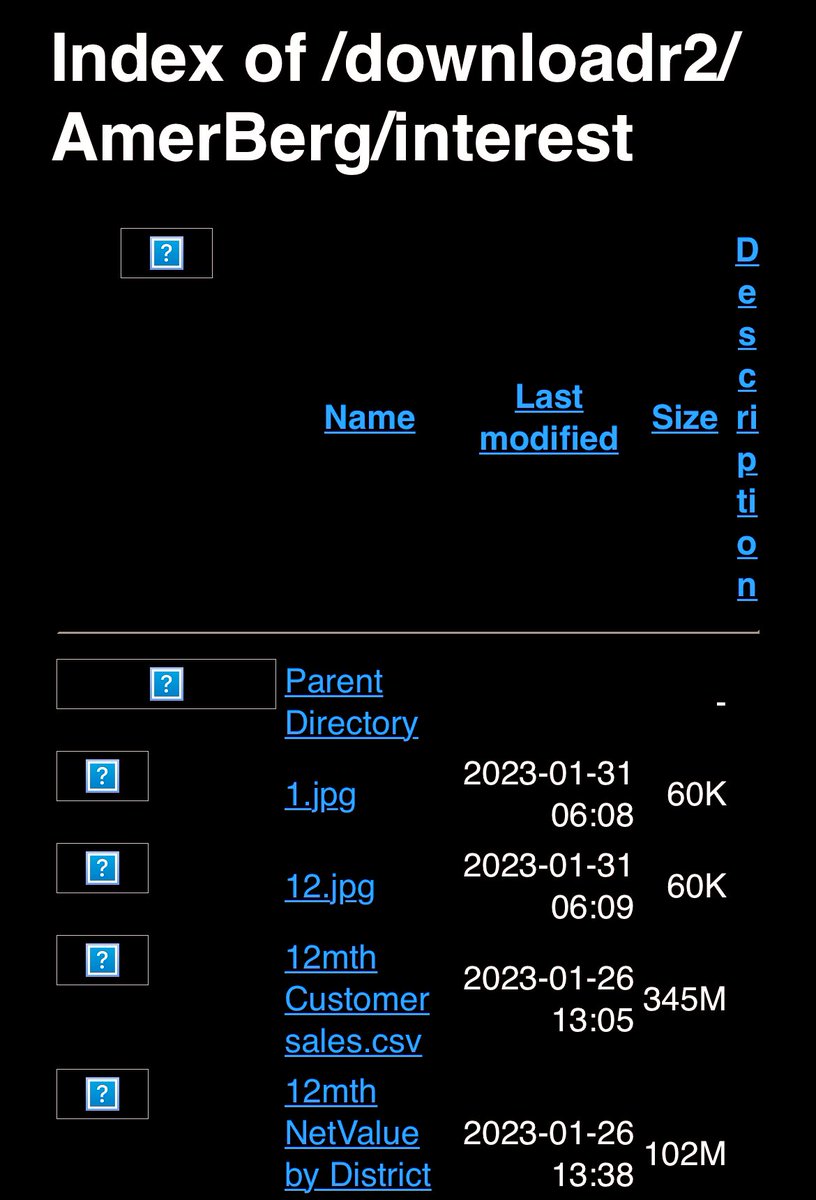
The screenshot from the data breach post about the AmerisourceBergen ransomware attack seemed to claim the possession of a parent directory along with some images all listed in the last week of January 2023.
“This was an isolated incident, and we are in the process of investigating to determine whether any sensitive data was compromised,” a company spokesperson told the news website. AmerisourceBergen also stated that it took precautionary measures to make sure all the systems were clear from any intrusion and the disruption was contained.
Links of Mitel cyberattack to AmerisourceBergen ransomware attack
Adding to the mystery of the different dates, researchers found a link between the Mitel MiVoice VOIP appliances’ vulnerability exploitation to it.
The Lorenz ransomware group was found to be using the phone systems of connected corporate networks to breach systems and gain initial access to systems. It is speculated that the group got access to AmerisourceBergen’s subsidiary through the same vulnerability i.e., CVE-2022-29499 connected through the telecommunications channel.
It is speculated that the data leak notice on the group’s extortion site could be a result of the denial of the ransom payment. AmerisourceBergen headquartered in Pennsylvania is yet to reply to The Cyber Express’s email asking for confirmation.