Security researchers from Synacktiv CSIRT have uncovered a sophisticated Linux rootkit dubbed LinkPro that leverages eBPF (extended Berkeley Packet Filter) technology to establish persistent backdoor access while remaining virtually invisible to traditional monitoring tools.
The infection chain originated from a vulnerable Jenkins server exposed to the internet, exploited through CVE-2024-23897.
Threat actors leveraged this initial access point to deploy a malicious Docker image named “kvlnt/vv” across multiple Amazon EKS (Elastic Kubernetes Service) clusters.
The containerized payload consisted of a Kali Linux base image containing three critical components: a bash startup script, a VPN server program called “vnt” for proxy capabilities, and a Rust-based downloader malware dubbed “vGet”.paste.txt
The malware addressed a significant evolution in Linux-targeted threats, combining advanced stealth capabilities with flexible operational modes to compromise GNU/Linux systems across cloud infrastructure.paste.txt.
The first piece of malicious code is a dropper embedding another vShell backdoor (v4.9.3) executed in memory, this time communicating via DNS tunneling.
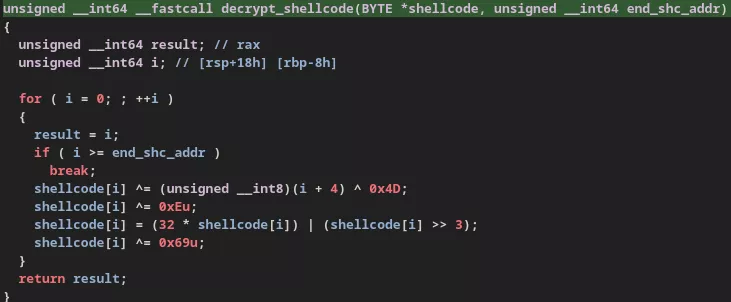
The vGet downloader retrieved an encrypted payload from an Amazon S3 bucket, delivering vShell 4.9.3 backdoor directly into memory to avoid leaving traces on disk.
This previously documented backdoor, notably used by threat actor UNC5174, communicated with its command and control server at 56.155.98.37 via WebSocket.
The sophisticated attack eventually led to the deployment of LinkPro, the crown jewel of the operation.paste.txt
Advanced eBPF-Based Stealth Mechanisms
LinkPro distinguishes itself through its dual-layer concealment strategy utilizing two distinct eBPF modules.
LinkPro embeds four ELF modules: a shared library, a kernel module, and two eBPF modules:
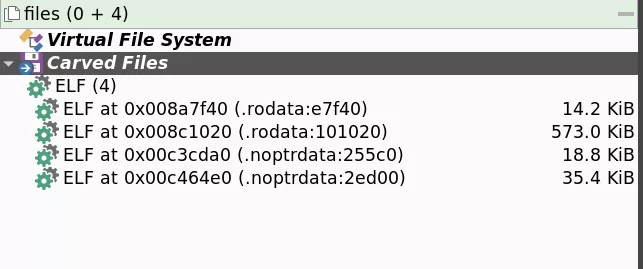

The first module, referred to as the “Hide” module, implements eBPF programs of Tracepoint and Kretprobe types to intercept critical system calls.
By hooking into getdents and getdents64 system calls, LinkPro filters directory listings to remove any references to files containing keywords like “.tmp~data” or “.system”.
The rootkit also hides specific process directories under /proc/ whose process IDs are stored in its eBPF map, capable of concealing up to 10 PIDs simultaneously.paste.txt
The Hide module employs an additional sophisticated technique to conceal its own eBPF programs from detection tools like bpftool.
By intercepting sys_bpf system calls and checking if returned program IDs match those stored in its internal map, LinkPro instructs the kernel to return an error code, effectively making its eBPF components invisible to administrative utilities.
However, this technique requires the Linux kernel to be compiled with the CONFIG_BPF_KPROBE_OVERRIDE configuration option, available in recent versions of Amazon Linux and Ubuntu 24.04.paste.txt
When eBPF-based hiding fails due to missing kernel features, LinkPro deploys an alternative stealth mechanism by modifying the /etc/ld.so.preload configuration file.
The rootkit extracts and installs a malicious shared library named libld.so to /etc/libld.so, which gets loaded by all programs requiring dynamic linking.
This library hooks several libc functions including fopen, getdents, readdir, and kill to hide LinkPro network traces and filesystem artifacts.paste.txt
The libld.so hook particularly targets /proc/net/tcp, /proc/net/tcp6, /proc/net/udp, and /proc/net/udp6 files, filtering out any lines containing port 2233—LinkPro’s default listening port.
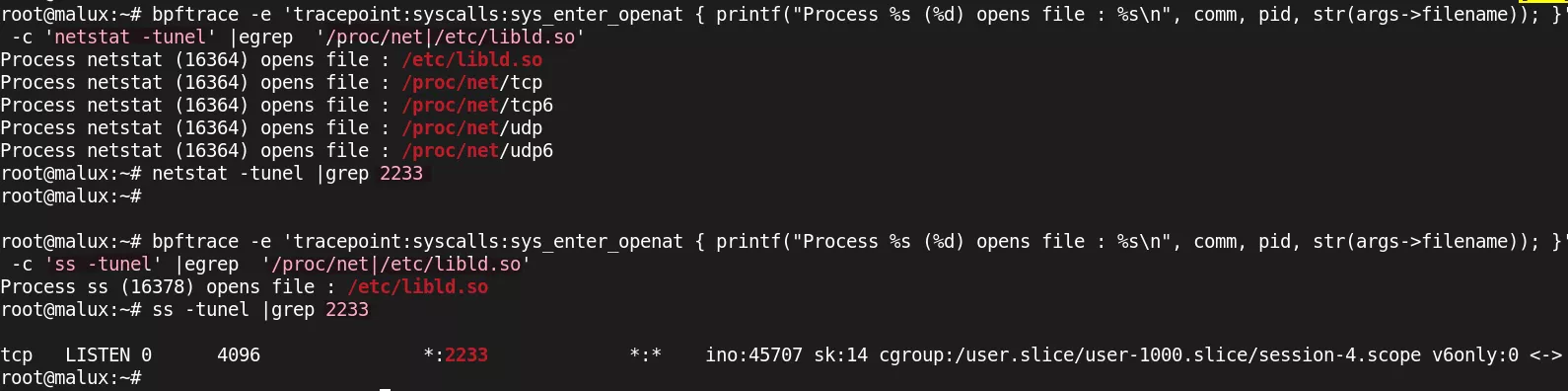

While effective against tools like netstat that rely on /proc/net files, this technique can be bypassed by the “ss” command which uses the netlink protocol instead.paste.txt
Magic Packet Activation and Port Redirection
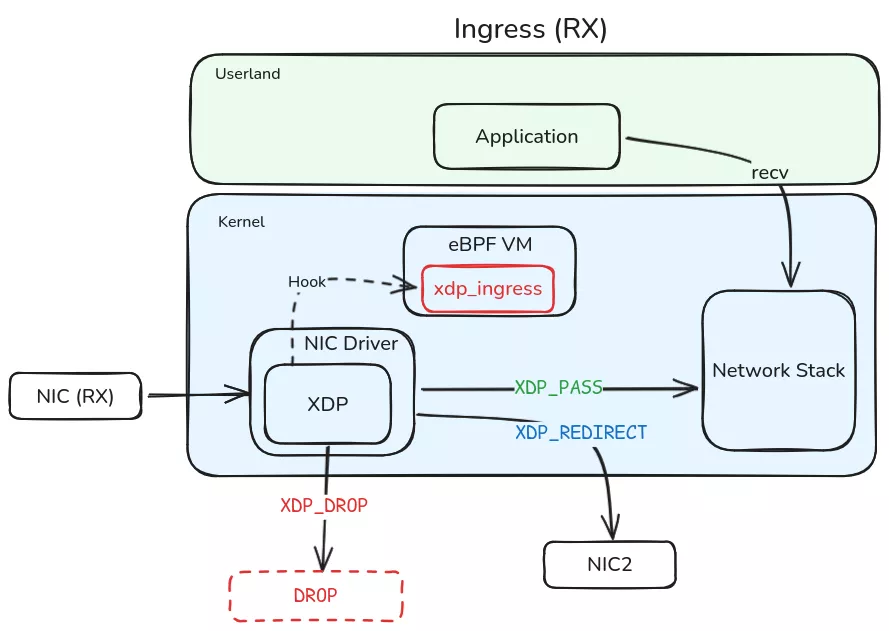
The second eBPF module, called “Knock,” enables LinkPro’s passive backdoor mode through magic packet activation.
This module consists of two eBPF programs: xdp_ingress of XDP (eXpress Data Path) type and tc_egress of TC (Traffic Control) type.

The backdoor can also establish SOCKS5 proxy tunnels for lateral movement within the compromised infrastructure and spawn additional HTTP listeners on demand.
The xdp_ingress program monitors incoming network traffic for a TCP SYN packet with a specific window size value of 54321. Upon detecting this magic packet, the program registers the source IP address in a knock_map with a one-hour expiration window, transitioning LinkPro into an “open” state for that specific IP.paste.txt
Once activated, xdp_ingress intercepts subsequent TCP packets from the registered IP and modifies the destination port to LinkPro’s internal listening port 2233, regardless of the original destination port specified.
The tc_egress program then modifies outgoing response packets to restore the original destination port as the source port, creating a transparent communication channel.
This sophisticated port redirection allows operators to send commands through any port authorized by front-end firewalls, significantly complicating forensic analysis and correlation between firewall logs and actual network activity.paste.txt
Systemd Service Disguise
LinkPro establishes persistence by masquerading as the legitimate systemd-resolved service responsible for network name resolution.
The rootkit copies its executable to /usr/lib/.system/.tmp~data.resolveld and creates a systemd unit file at /etc/systemd/system/systemd-resolveld.service with appropriate configuration to ensure automatic execution at system boot.
To further evade detection, LinkPro performs timestomping by modifying the creation and modification dates of its files to match those of /etc/passwd.paste.txt
The backdoor supports two operational modes: reverse (passive) and forward (active). In reverse mode, LinkPro listens for commands from its C2 server using the magic packet activation mechanism described above.
In forward mode, the backdoor actively initiates communication with its command and control server, supporting five different protocols: HTTP, WebSocket, UDP, TCP, and DNS tunneling. The analyzed samples communicated with IP address 18.199.101.111 using HTTP protocol over port 2233.paste.txt
Once established, LinkPro provides operators with extensive remote access functionality including interactive bash terminal sessions, arbitrary shell command execution, comprehensive file management operations, and file upload/download capabilities with chunked transfer encoding.
These features enable threat actors to maintain persistent access, exfiltrate sensitive data, and pivot to additional systems across the victim’s network environment.paste.txt.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




