A longstanding timing oracle attack targeting RSA encryption has resurfaced, as identified by a researcher from Red Hat. This particular oracle attack, initially unearthed in 1998 by Daniel Bleichenbacher, has proven to be still exploitable despite its age. Over the years, this vulnerability has made multiple reappearances, with the most recent instance recorded in 2018 when researchers Hanno Böck, Jurau Somorovsky, and Craig Young reintroduced it through their publication titled “ROBOT,” an acronym standing for “Return of Bleichenbacher’s Oracle Threat.”
Bleichenbacher initially pinpointed that SSL servers emitted error messages related to the PKCS #1 v1.5 padding. These messages inadvertently facilitated an assault on the ciphertext, undermining the confidentiality integral to Transaction Layer Security (TLS) protocols utilizing RSA encryption. Under this vulnerability, an individual able to observe the time required for the decryption process using the private key could feasibly decrypt RSA messages that were intercepted.
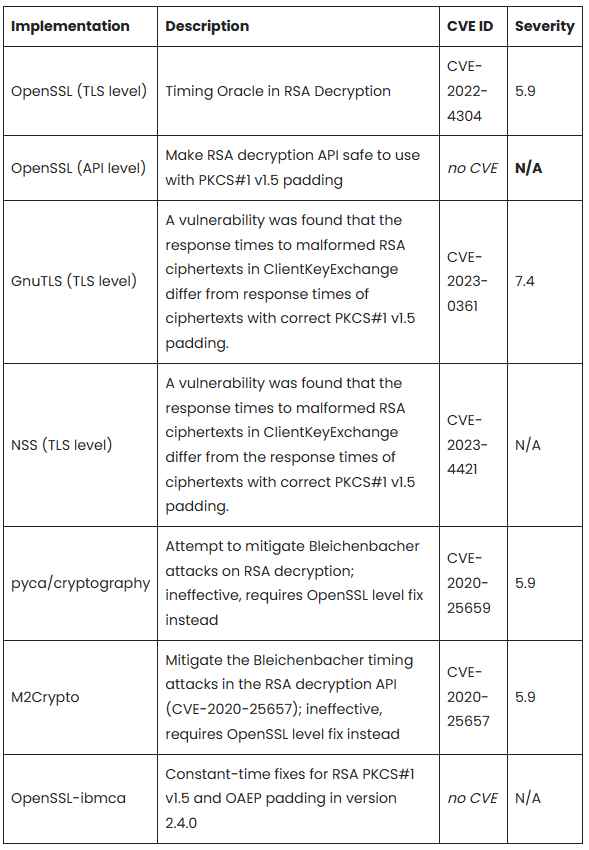
The revitalized attack strategy, whimsically named “Marvin” as a homage to both “The Hitchhiker’s Guide to the Galaxy” and the previously mentioned ROBOT attack, was recently unveiled by Hubert Kario, a researcher hailing from Red Hat’s Czech team. Kario’s intensive investigation revealed that this attack remains viable against several cryptographic applications, provided that it incorporates more statistically sophisticated techniques than those initially used by Bleichenbacher. The list of susceptible cryptographic implementations includes OpenSSL, GnuTLS, Mozilla’s NSS (notwithstanding existing patches, as per Kario’s findings), pyca/cryptography (which has only been partially remediated), M2Crypto, and OpenSSL-ibmca.
Kario’s documentation meticulously catalogues a variety of CVEs (Common Vulnerabilities and Exposures), providing a valuable resource for those in the cybersecurity field. He disclosed that the development of effective patches between 2020 and 2023 was significantly hampered by two primary obstacles. Firstly, the researchers grappled with an onslaught of false positives generated by the timing signal of their test script or harness. This issue, in turn, precipitated a second challenge: the unreliable results made it exceptionally difficult to identify the exact origin of the timing signal. Without this crucial information, engaging upstream developers in addressing the issue was a formidable task.
Progress was only realized mid-2022 when a constant-time test harness was finally developed, facilitating the creation and implementation of fixes. To assist others in the field, Kario has made scripts available that are designed to test for this specific vulnerability in various implementations. Furthermore, he suggested that system logs could serve as a reliable indicator of whether an attack had been initiated. In his words, servers that have not experienced a substantial number of connection attempts involving RSA key exchanges are likely safe from this attack.
Nevertheless, Kario strongly advocates for the discontinuation of RSA PKCS#1 v1.5 encryption usage, even in cases where there might be a perceived necessity for backward compatibility. According to the published research, any usage of the generic PKCS#1 v1.5 API absent of the Marvin workaround would be classified under CWE-242, denoting the “Use of Inherently Dangerous Function.” Without verified side-channel free code from the calling side, the calling code would be automatically deemed vulnerable. For a more in-depth understanding, Red Hat has published the comprehensive research paper, which delineates the threat vector, attack pattern, and additional data pertaining to this enduring vulnerability.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
