A sophisticated Android banking trojan known as deVixor has emerged as a significant threat to mobile users, combining financial data theft, device surveillance, and ransomware capabilities into a single malicious platform.
Active since October 2025, the malware represents a concerning evolution in Android-based financial threats, targeting victims through fake automotive websites and leveraging Telegram infrastructure for command-and-control operations.
The malware is primarily spread through counterfeit websites masquerading as legitimate automotive businesses, luring victims with heavily discounted vehicle offers.
When users attempt to take advantage of these deals, they unknowingly download malicious APK files that install the deVixor trojan on their devices.
Cyble Research and Intelligence Lab’s (CRIL) comprehensive analysis of over 700 samples has revealed a large-scale infection campaign orchestrated by threat actors using deceptive distribution methods.
The campaign demonstrates sophisticated social engineering, with fraudulent domains including asankhodroo[.]shop, asan-khodro.store, and naftyar.info distributing the malware.
Multiple indicators suggest the operation specifically targets Iranian users, including linguistic artifacts in Telegram communications, Persian-language phishing overlays, and an exclusive focus on Iranian banks, domestic payment services, and local cryptocurrency exchanges, confirming the regional nature of this threat.
Banking Data Harvesting Capabilities
deVixor employs multiple sophisticated techniques to steal banking credentials and financial information.
The malware extensively harvests SMS-based financial data, scanning up to 5,000 messages to extract one-time passwords (OTPs), account balances, credit and debit card numbers, and messages from banks and cryptocurrency exchanges.
The trojan targets explicitly 26 Iranian banks including Bank Melli Iran, Bank Mellat, Bank Tejarat, and Bank Saderat Iran, along with 14 cryptocurrency exchanges such as Binance, CoinEx, Ramzinex, and Exir.
Beyond SMS harvesting, deVixor implements WebView-based JavaScript injection attacks to capture banking credentials.
The malware generates fraudulent bank notifications that, when tapped by victims, load legitimate banking websites inside a WebView component.
Malicious JavaScript code is then injected into login forms, silently exfiltrating usernames and passwords to the command-and-control server as users enter their credentials.
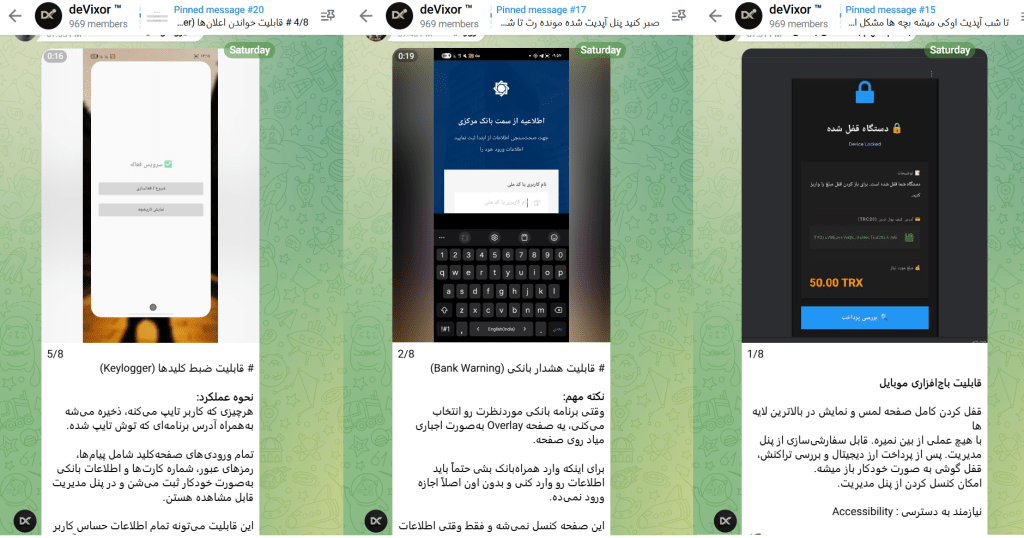
One of deVixor’s most concerning features is its remotely triggered ransomware capability. When threat actors issue the “RANSOMWARE” command, the malware locks the victim’s device and displays a ransom message demanding cryptocurrency payment.
Based on screenshots shared on the threat actor’s Telegram channel, victims see a message stating “Your device is locked. Deposit to unlock” along with a TRON cryptocurrency wallet address and a demand of 50 TRX tokens.
The ransomware configuration is stored in a persistent file named LockTouch.json, ensuring the lock remains active even after device reboots.
Advanced Command Infrastructure
The deVixor operation demonstrates sophisticated infrastructure management through dual-server architecture.
GET_EXCHANGE command, this command collects the most recent SMS messages sent by known banks and payment services.
The malware uses Firebase for receiving commands from operators while maintaining a separate command-and-control server for exfiltrating stolen data.
Each deployed APK is assigned a unique Bot ID stored in a local port.json file, enabling operators to track, monitor, and control individual infected devices through a Telegram bot-based administrative panel.
Evidence from the threat actor’s Telegram channel reveals numerous simultaneously infected devices, each associated with unique Bot IDs, indicating an active campaign operating at significant scale.
The channel, created shortly after deVixor’s initial development, actively publishes version updates, promotes new capabilities, and shares operational screenshots, suggesting the malware is maintained as an ongoing criminal service rather than a short-lived operation.
Analysis of multiple variants shows clear evolution in deVixor’s capabilities. Early versions exhibited limited functionality focused on collecting personally identifiable information and harvesting banking-related SMS messages.
Subsequent variants introduced banking-focused overlay attacks, keylogging, ransomware functionality, Google Play Protect bypass techniques, and extensive abuse of Android’s Accessibility Service.
deVixor represents a concerning evolution in Android banking malware, demonstrating how modern mobile threats have progressed beyond basic credential harvesting into sophisticated remote access toolkits.
The latest versions support over 50 commands enabling comprehensive device control, including keystroke capture, screenshot collection, notification harvesting, contact extraction, gallery access, and application disguise.
Version 2 introduced additional commands such as SEARCH_ALL_SMS for keyword-based message searching, NOTIFICATION_READER for collecting device notifications, and GET_ALL_SENT_SMS for exfiltrating sent message history.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



