A new variant of the Konfety Android malware emerged with a malformed ZIP structure along with other obfuscation methods that allow it to evade analysis and detection.
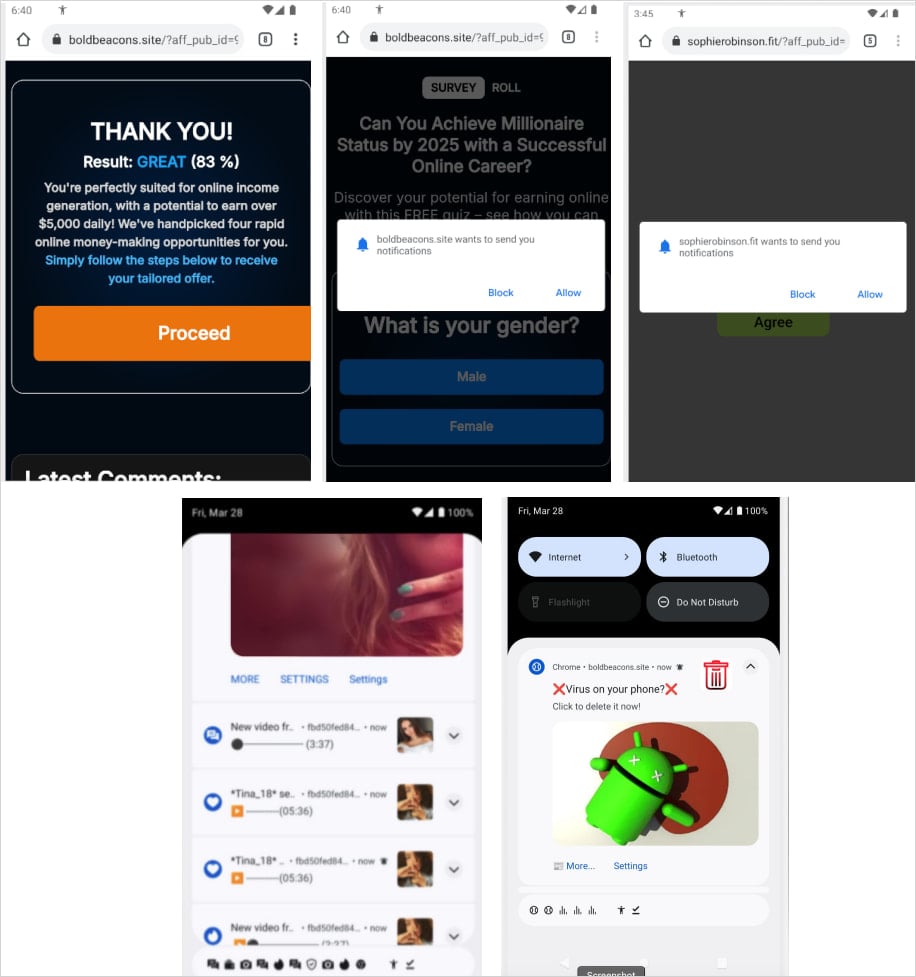
Konfety poses as a legitimate app, mimicking innocuous products available on Google Play, but features none of the promised functionality.
The capabilities of the malware include redirecting users to malicious sites, pushing unwanted app installs, and fake browser notifications.
Instead, it fetches and renders hidden ads using the CaramelAds SDK and exfiltrates information such as installed apps, network configuration, and system information.
Source: Zimperium
Although Konfety isn’t a spyware or RAT tool, it includes an encrypted secondary DEX file inside the APK, which is decrypted and loaded at runtime, containing hidden services declared in the AndroidManifest file.
This leaves the door open for installing additional modules dynamically, thus allowing the delivery of more dangerous capabilities on current infections.
Evasion tactics
Researchers at mobile security platform Zimperium discovered and analyzed the latest Konfety variant and report that the malware uses several methods to obfuscate its real nature and activity.
Konfety tricks victims into installing it by copying the name and branding of legitimate apps are available on Google Play and distributing it through third-party stores – a tactic that researchers at Human called “evil twin” or “decoy twin.”
The operators of the malware are promoting it on third-party app stores.
These marketplaces are often where users look for “free” variants of premium apps because they want to avoid Google tracking, have an Android device that is no longer supported, or don’t have access to Google services.
The dynamic code loading, where the malicious logic is hidden in an encrypted DEX file that loads at runtime, is another effective obfuscation and evasion mechanism that Konfety employs.
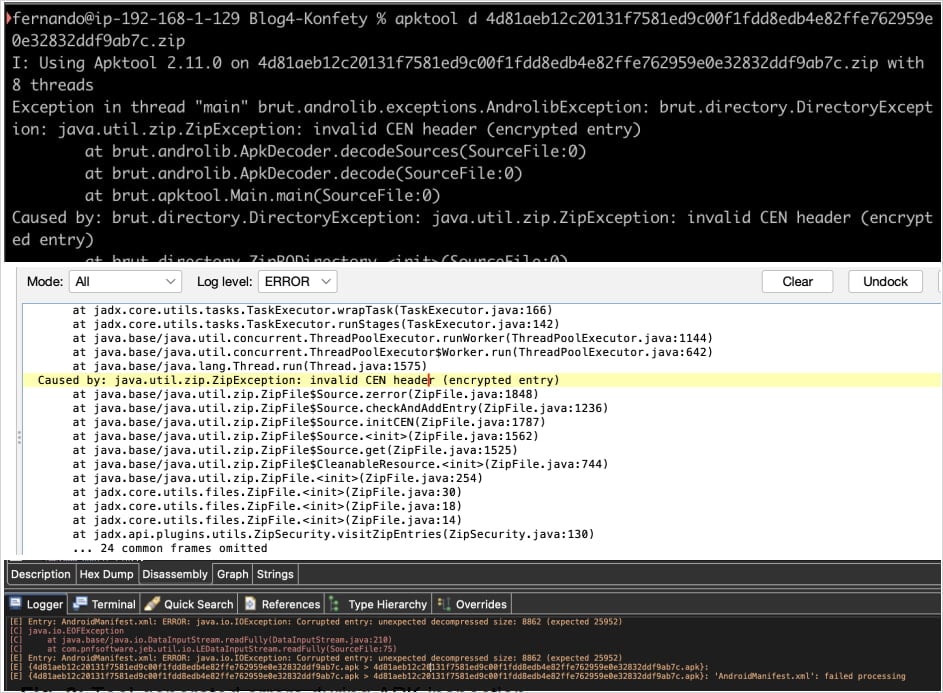
Another uncommon anti-analysis strategy in Konfety is to manipulate the APK files in a way that confuses or breaks static analysis and reverse engineering tools.
First, the APK sets the General Purpose Bit Flag to ‘bit 0,’ signaling that the file is encrypted, even though it is not. This triggers false password prompts when trying to inspect the file, blocking or delaying access to the APK’s contents.
Secondly, critical files in the APK are declared using BZIP compression (0x000C), which isn’t supported by analysis tools like APKTool and JADX, resulting in a parsing failure.
Source: Zimperium
Meanwhile, Android ignores the declared method and falls back to default processing to maintain stability, allowing the malicious app to install and run on the device without issue.
After installation, Konfety hides its app icon and name and uses geofencing to change behavior according to the victim’s region.
Compression-based obfuscation has been observed in the past in Android malware, as highlighted in a Kaspersky report from April 2024 on SoumniBot malware.
In that case, SoumniBot declared an invalid compression method in AndroidManifest.xml, declared a fake file size and data overlay, and confused analysis tools with very large namespace strings.
It is typically recommended to avoid installing APK files from third-party Android app stores and only trust software from publishers you know.

While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz’s detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.
