The cybersecurity landscape continues to evolve with increasingly sophisticated malware variants, and a recent discovery highlights the persistent threat posed by advanced Android packers.
Security researchers have identified a highly complex packer dubbed “Ducex,” which serves as a delivery mechanism for the notorious Triada Android malware.
This Chinese-developed tool represents a significant advancement in mobile malware obfuscation techniques, demonstrating the lengths to which cybercriminals will go to evade detection and analysis.
The Ducex packer was discovered embedded within a fake Telegram application, showcasing the continued exploitation of popular messaging platforms as attack vectors.
Unlike traditional malware deployment methods, Ducex employs a multi-layered approach that combines function encryption, string obfuscation, and sophisticated anti-analysis techniques.
The malware’s primary objective extends beyond simple payload delivery, incorporating extensive measures to complicate reverse engineering and frustrate security researchers attempting to understand its operation.
ANY.RUN analysts identified the sample during routine malware analysis, recognizing the characteristic communication patterns associated with the Triada family.
The discovery emerged from the team’s investigation into suspicious Android applications, where the Interactive Sandbox quickly flagged the malware’s distinctive network behavior.
.webp)
The researchers noted that despite Triada’s nine-year presence in the threat landscape since 2016, this particular variant demonstrated unprecedented levels of sophistication in its packing and obfuscation mechanisms.
The packer’s impact extends beyond individual infections, representing a concerning trend toward more sophisticated mobile malware distribution.
By successfully evading traditional detection methods and complicating analysis workflows, Ducex enables the underlying Triada payload to establish persistence and execute its malicious operations.
This development poses significant challenges for security teams relying on conventional analysis tools and highlights the need for advanced dynamic analysis capabilities.
Advanced Function Encryption and Anti-Analysis Mechanisms
The most striking aspect of Ducex’s design lies in its comprehensive approach to function encryption and anti-analysis protection.
The packer implements a modified RC4 algorithm with additional shuffling mechanisms, encrypting entire function blocks to prevent static analysis.
.webp)
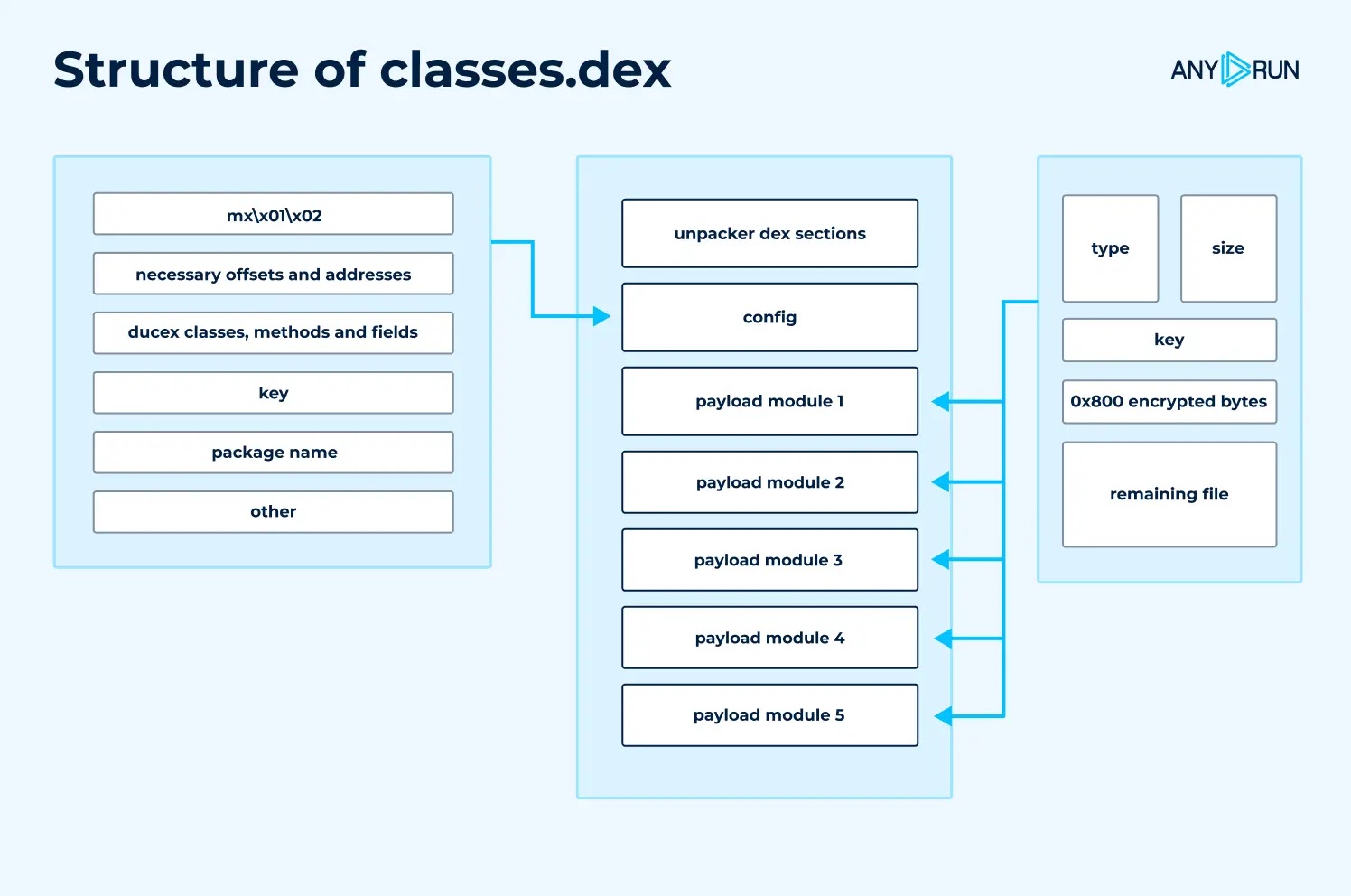
This encryption occurs at the library level, specifically within the libducex.so component, where critical functions including the program entry point and JNI_OnLoad remain encrypted until runtime execution.
The decryption process follows a sophisticated configuration-based approach, utilizing a structure containing magic values, decryption start addresses, byte counts, callback functions, and 16-byte encryption keys.
The implementation deviates from standard RC4 through the incorporation of additional shuffling operations, requiring custom decryption routines rather than standard cryptographic libraries.
def rc4_process(s, encoded_data):
i = s[256]
j = s[257]
output = bytearray(encoded_data)
for n in range(len(encoded_data)):
i = (i + 1) & 0xff
a = s[i]
j = (j + a) & 0xff
b = s[j]
s[i], s[j] = b, a
output[n] ^= s[(a + b) & 0xff]
for _ in range(2):
i = (i + 1) & 0xff
a = s[i]
j = (j + a) & 0xff
b = s[j]
s[i], s[j] = b, a
return bytearray(output)The packer’s anti-analysis capabilities extend to comprehensive detection mechanisms targeting popular research tools including Frida, Xposed, and Substrate frameworks.
When any of these tools are detected in system memory, the malware immediately terminates execution, effectively blocking dynamic analysis attempts.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
