A major security vulnerability in the Android spyware operation Catwatchful has exposed the complete database of over 62,000 customer accounts, including plaintext passwords and email addresses, according to a security researcher who discovered the breach in June 2025.
Canadian cybersecurity researcher Eric Daigle uncovered the vulnerability through a SQL injection attack that allowed him to extract the entire user database from the stalkerware service.
The breach also exposed data from approximately 26,000 victims whose phones were being monitored without their knowledge.
Critical Security Flaw in “Undetectable” Spyware
Catwatchful marketed itself as completely invisible surveillance software, boasting that it “cannot be detected” and “cannot be uninstalled.” However, the service’s backend proved far less secure than its marketing claims suggested.
The vulnerability stemmed from an unauthenticated PHP API endpoint that was susceptible to SQL injection attacks. Despite operating a hybrid architecture using Google’s Firebase platform for storing stolen victim data, Catwatchful maintained a separate MySQL database containing user credentials that lacked basic security protections.
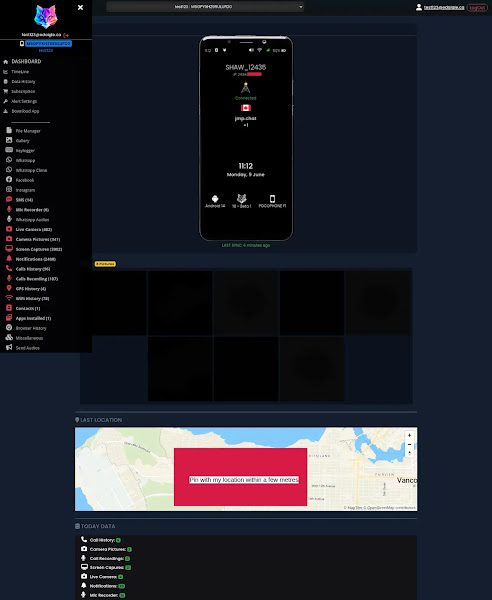
The leaked database revealed that Catwatchful had been operating since at least 2018, with victims primarily located in Mexico, Colombia, India, Peru, Argentina, Ecuador, and Bolivia.
The spyware collected comprehensive personal data, including photos, text messages, call logs, location data, and could remotely activate device cameras and microphones.
The breach also exposed the identity of the operation’s administrator, Omar Soca Charcov, a Uruguay-based developer who failed to respond to disclosure requests from journalists.
Catwatchful employed a sophisticated dual-server system. User registration triggered account creation in both Google Firebase and a custom database hosted on catwatchful.pink. While Firebase provided robust security for storing victim data, the custom server handling user authentication was completely vulnerable.
Daigle discovered that the service’s API calls were entirely unauthenticated, allowing anyone to access device information using simple parameters.
When he tested for SQL injection vulnerabilities using automated tools, he successfully identified both time-based blind and union-based injection points that allowed complete database extraction.
This incident represents the fifth major stalkerware breach in 2025 alone, highlighting systemic security failures across the surveillance software industry. Previous breaches have exposed millions of victim records from services including SpyX, Cocospy, Spyic, and Spyzie.
The pattern reveals that while these services collect highly sensitive personal data, they consistently fail to implement basic cybersecurity measures to protect either their customers or victims.
Following responsible disclosure, TechCrunch contacted various service providers. The hosting company temporarily suspended Catwatchful, though the service later migrated to HostGator. Google added Catwatchful to its Play Protect detection system, but has not yet disabled the Firebase instance storing victim data.
Security experts note that Android users can detect Catwatchful by dialing “543210” on their device, which triggers a built-in backdoor revealing the hidden application.
The exposed credentials have been added to the Have I Been Pwned breach notification service, allowing affected users to check if their accounts were compromised.
This breach highlights the inherent risks associated with stalkerware operations, illustrating that these illicit surveillance tools pose a threat to both perpetrators and victims due to inadequate security practices and insufficient data protection measures.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
